CI/CD Processes on Azure DevOps for a Voting Application ( CD Part )
Azure DevOps
Steps for Continuous Delivery:
1. Create a k8s service.
Go to Microsoft Azure, search for Kubernetes services, and create a cluster.
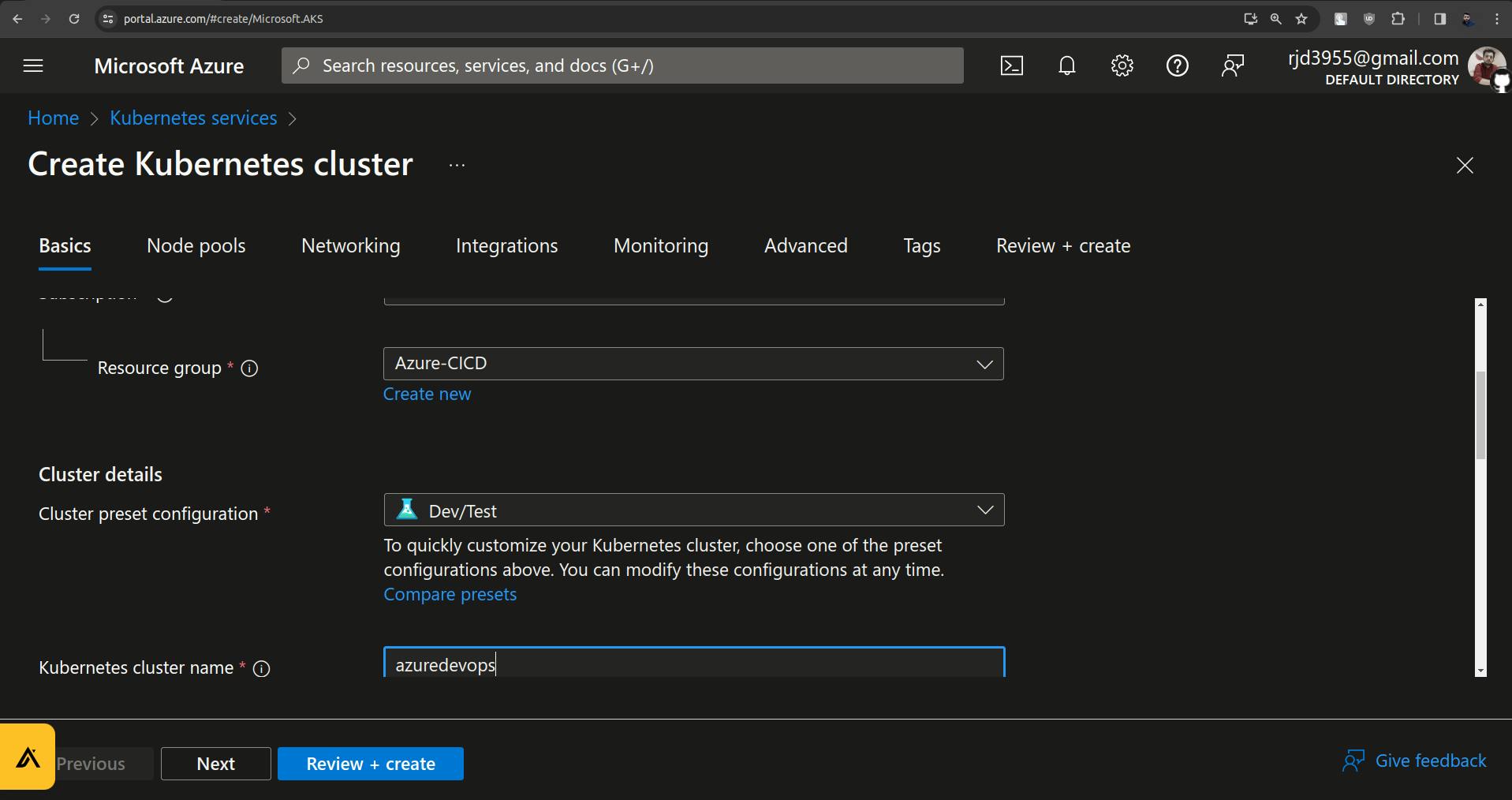
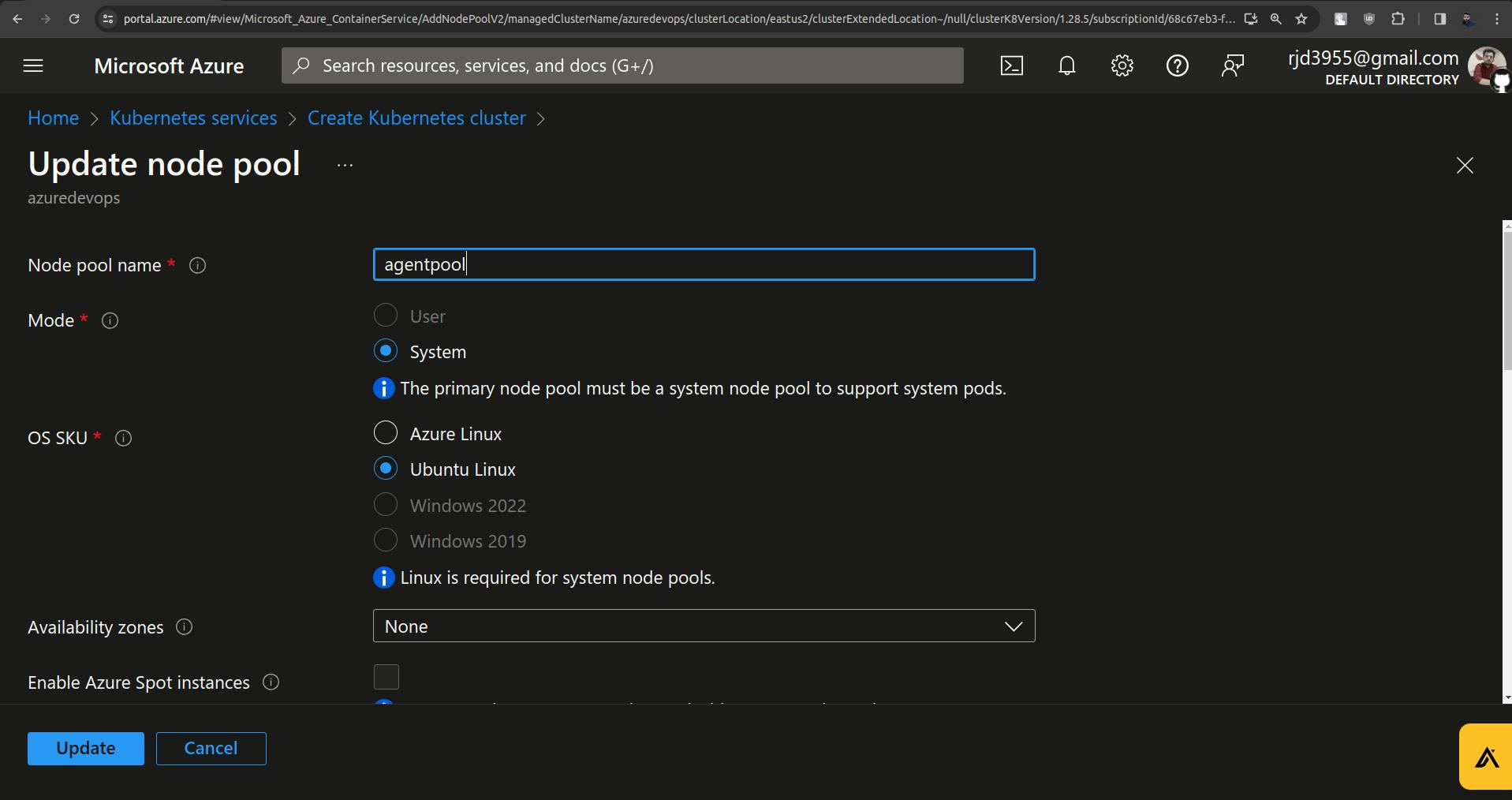
Click on that agenpool to update it.
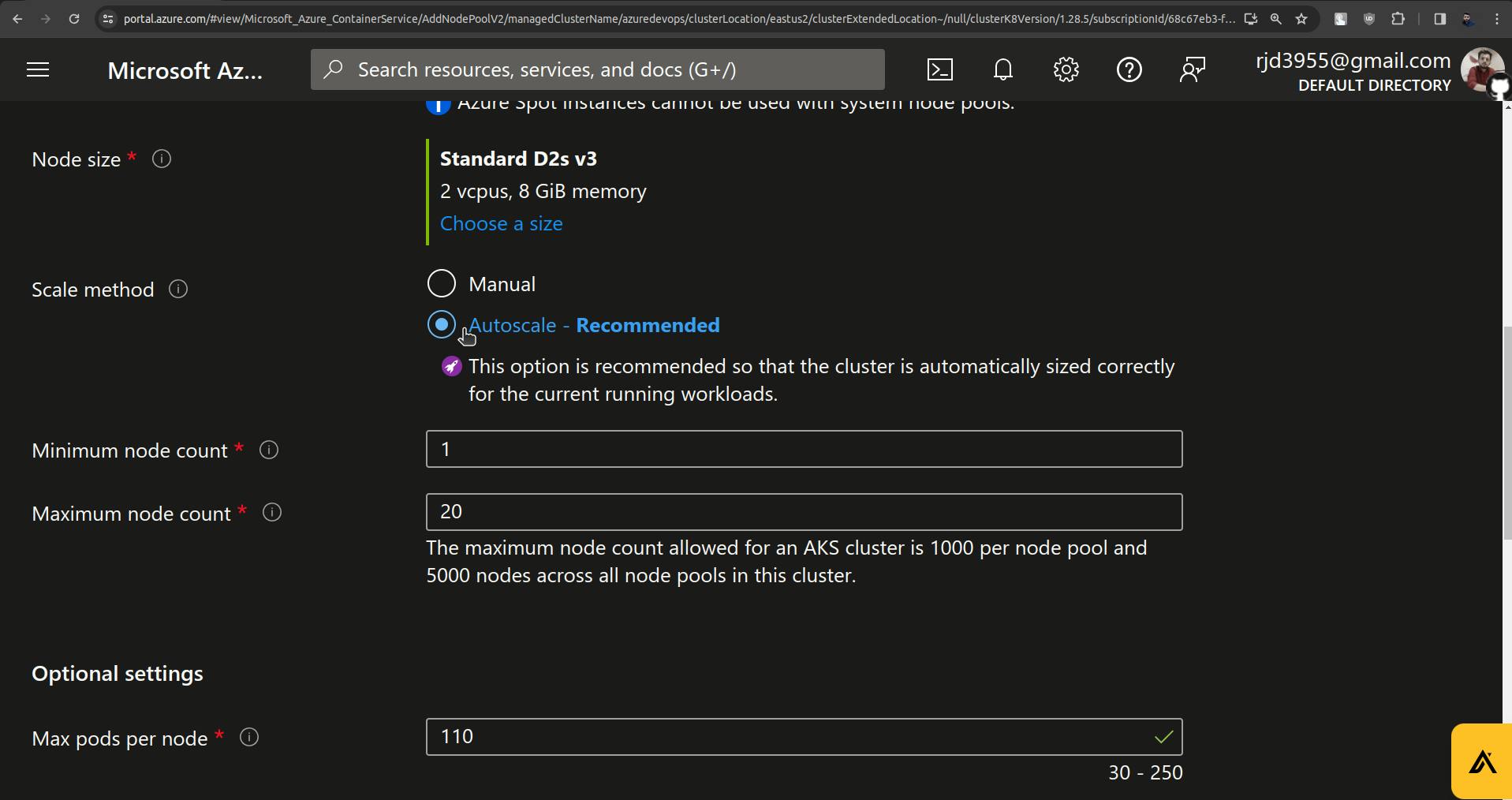
Set minimum node count to 1 and maximum node count to 2.
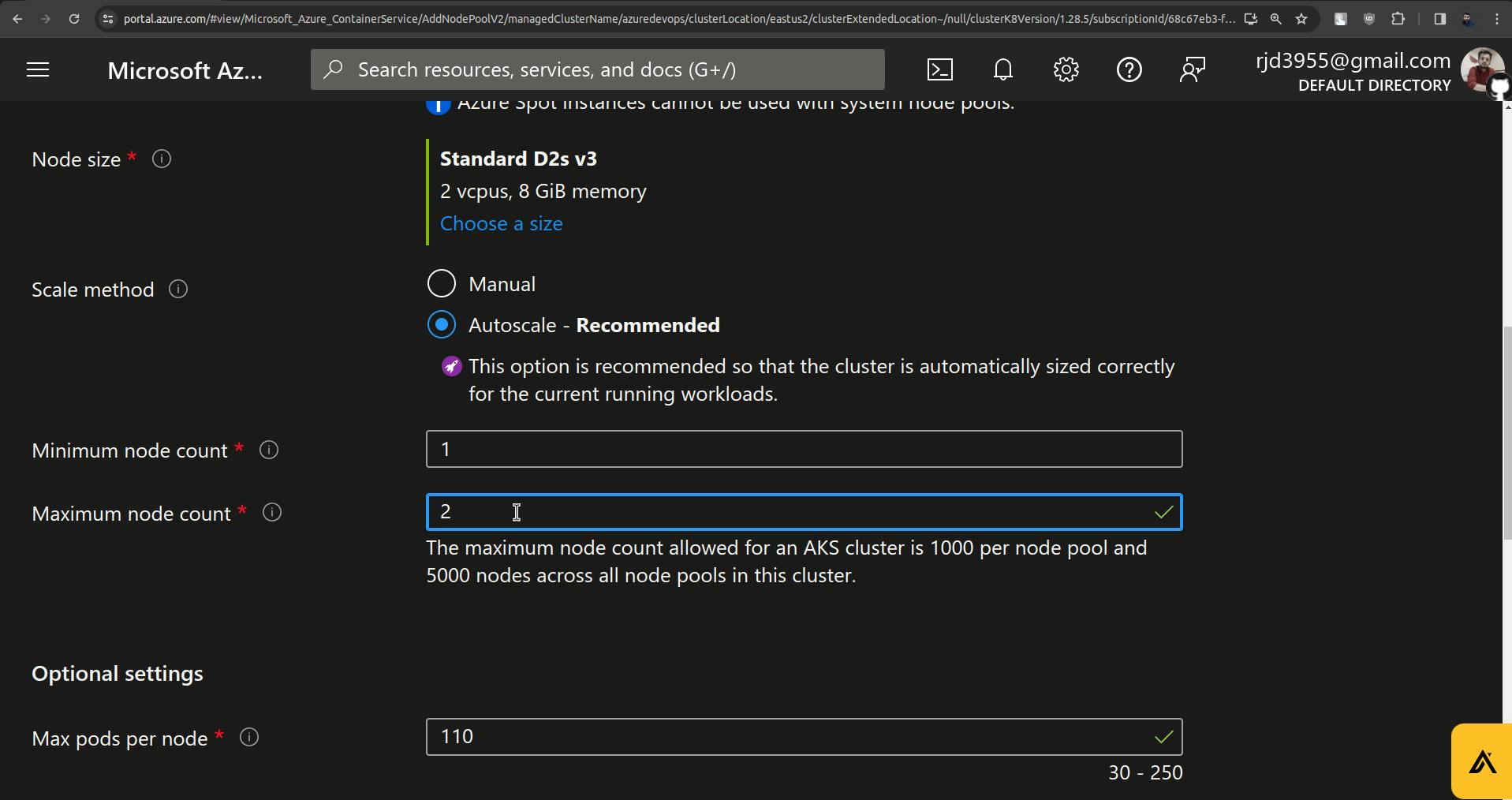
Set Max pods per node to 30.
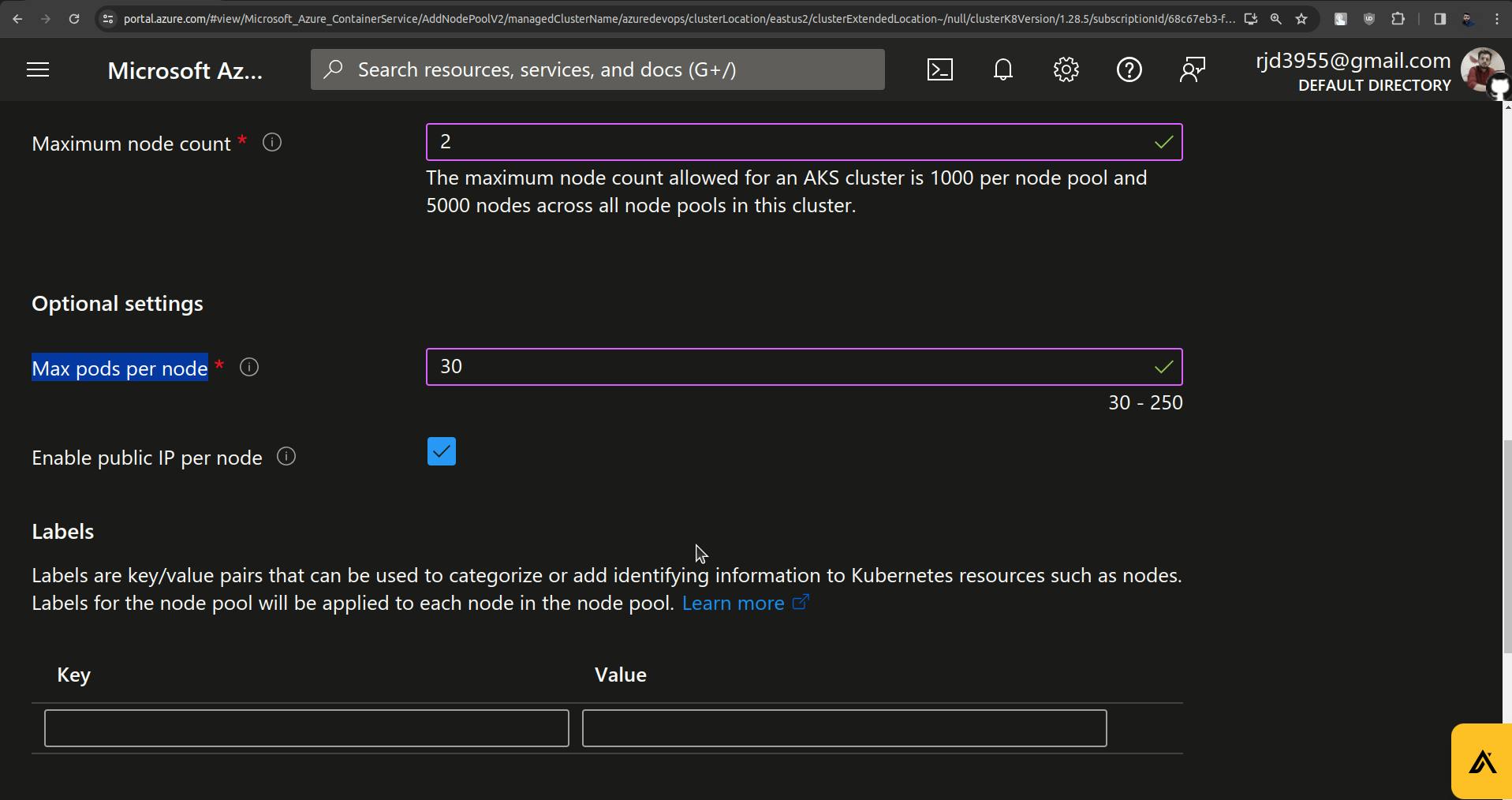
And click on update.
Click on Review+create.
Click on Create.
2. Now login to the k8s cluster.
az aks get-credentials --name azuredevops --resource-group Azure-CICD
This will set up the terminal with Azure Kubernetes cluster.
3. Set up ArgoCD ( Installation and configuration )
For installation refer to ArgoCD Documentation.
To install use the below commands or you can go with documentation.
kubectl create namespace argocd
kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
Check whether pods are up or not.
kubectl get pods -n argocd
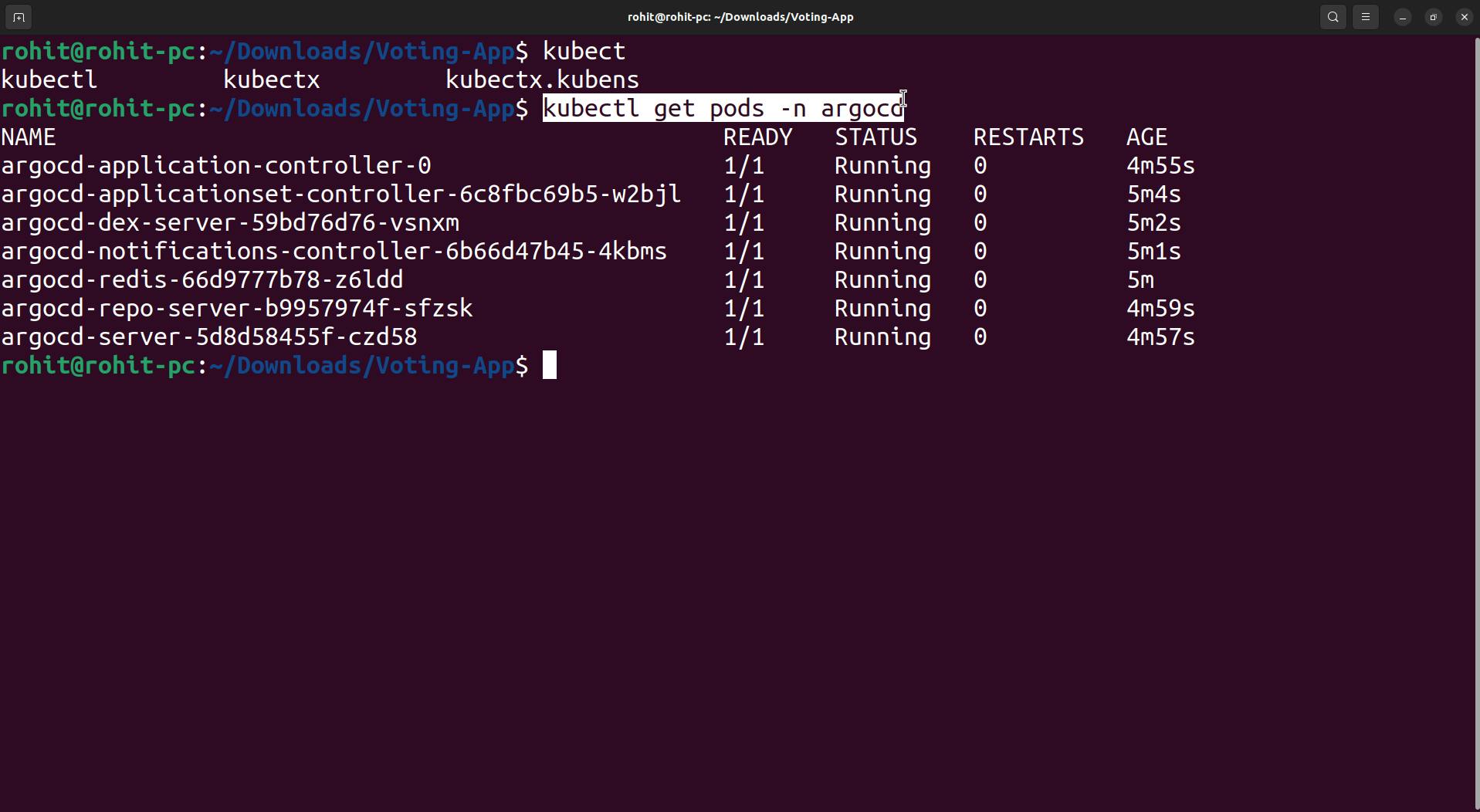
Once pods are up and running we start with ArgoCD configuration.
Login to ArgoCD, for it, just follow me through the commands.
kubectl get secrets -n argocd
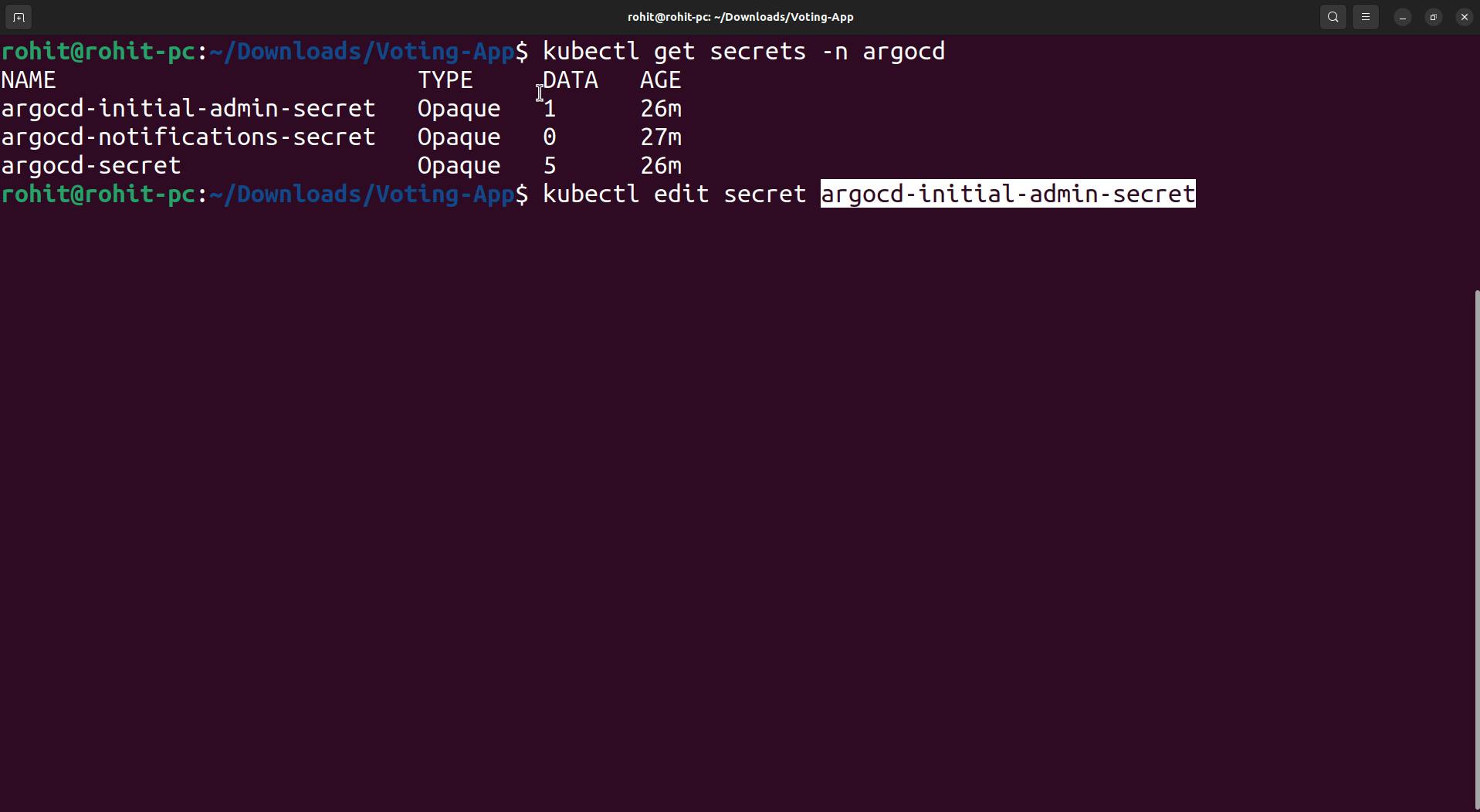
kubectl edit secret argocd-initial-admin-secret -n argocd
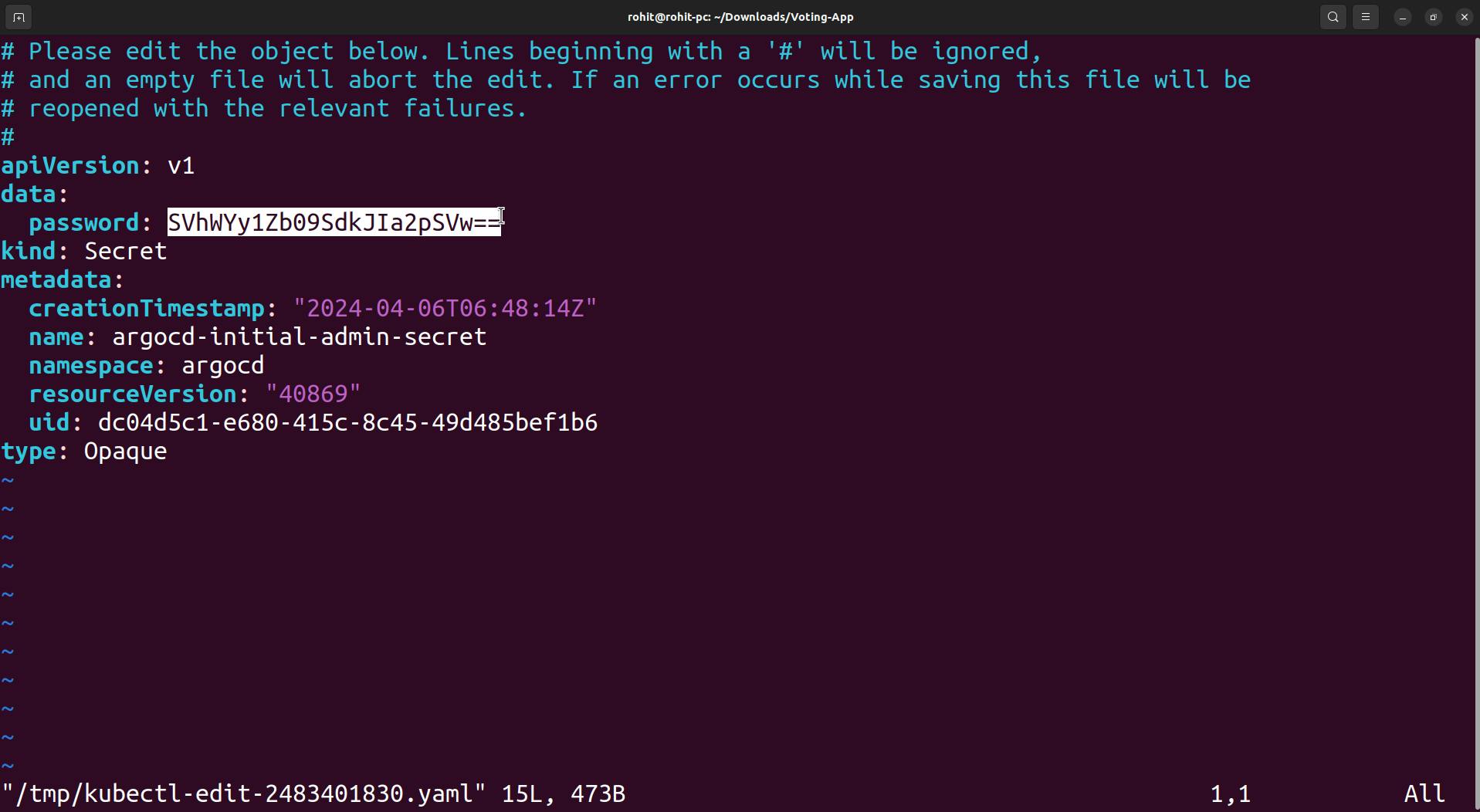
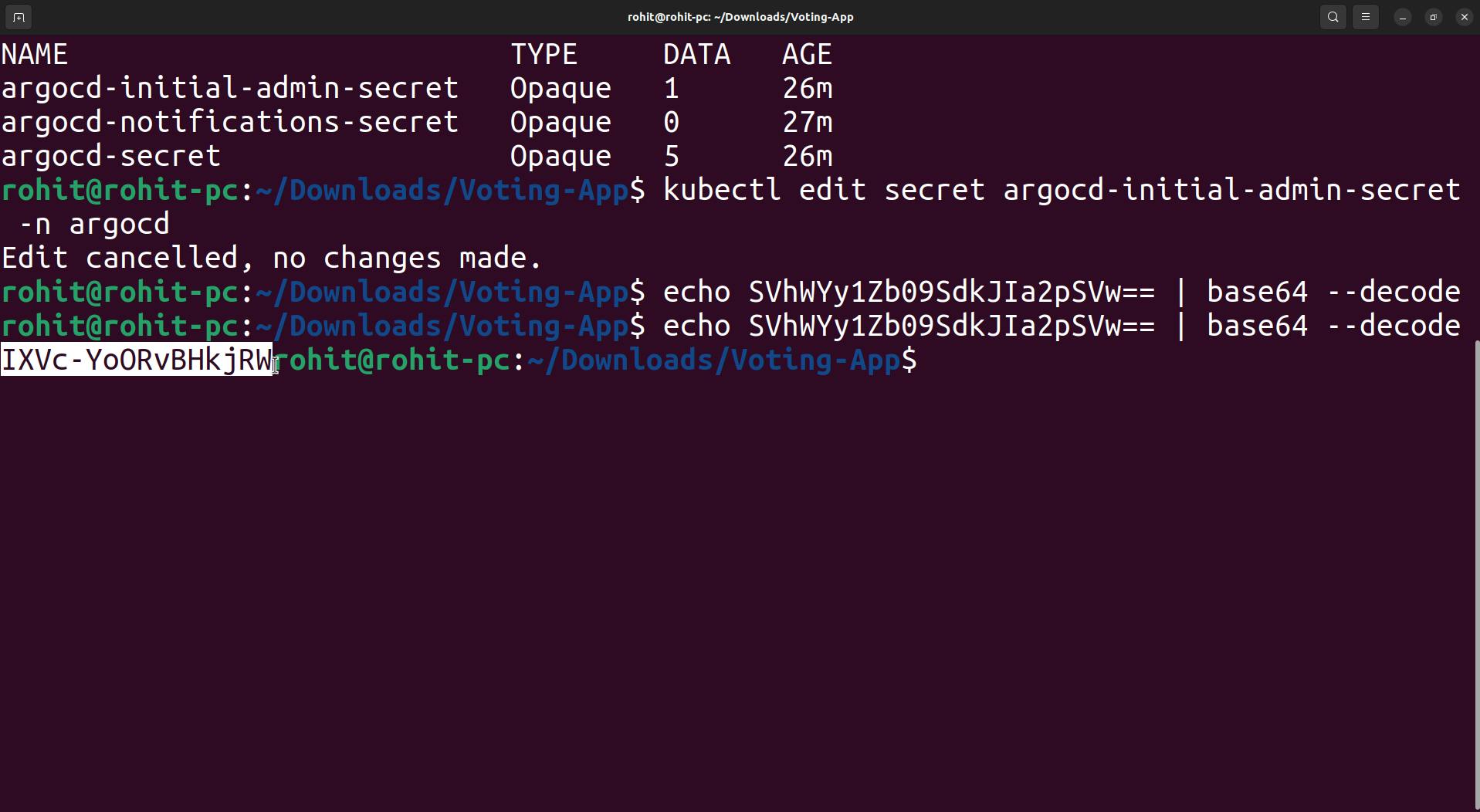
Copy that password which base64 encoded which we need to decode before using it for login.
echo SVhWYy1Zb09SdkJIa2pSVw== | base64 --decode
Now to get ArgoCd UI we need to expose ArgoCd to nodeport mode.
kubectl get svc -n argocd
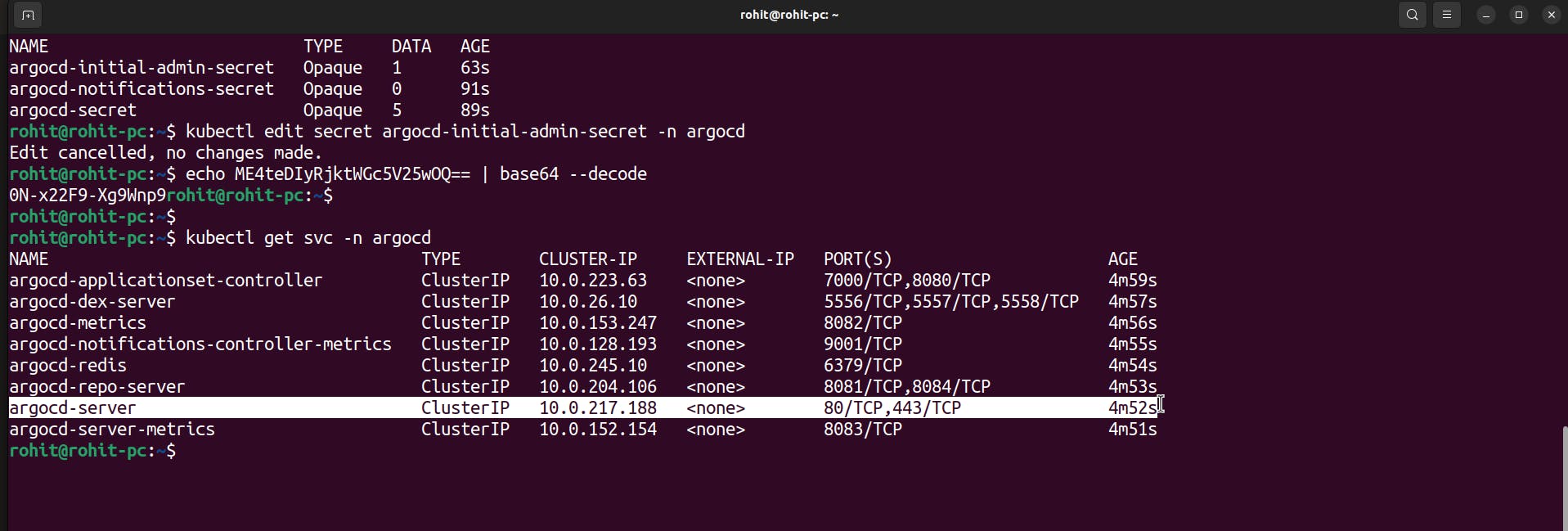
Here in the above screenshot, you can see that it is in ClusterIP mode.
So we will edit it.
kubectl edit svc argocd-server -n argocd
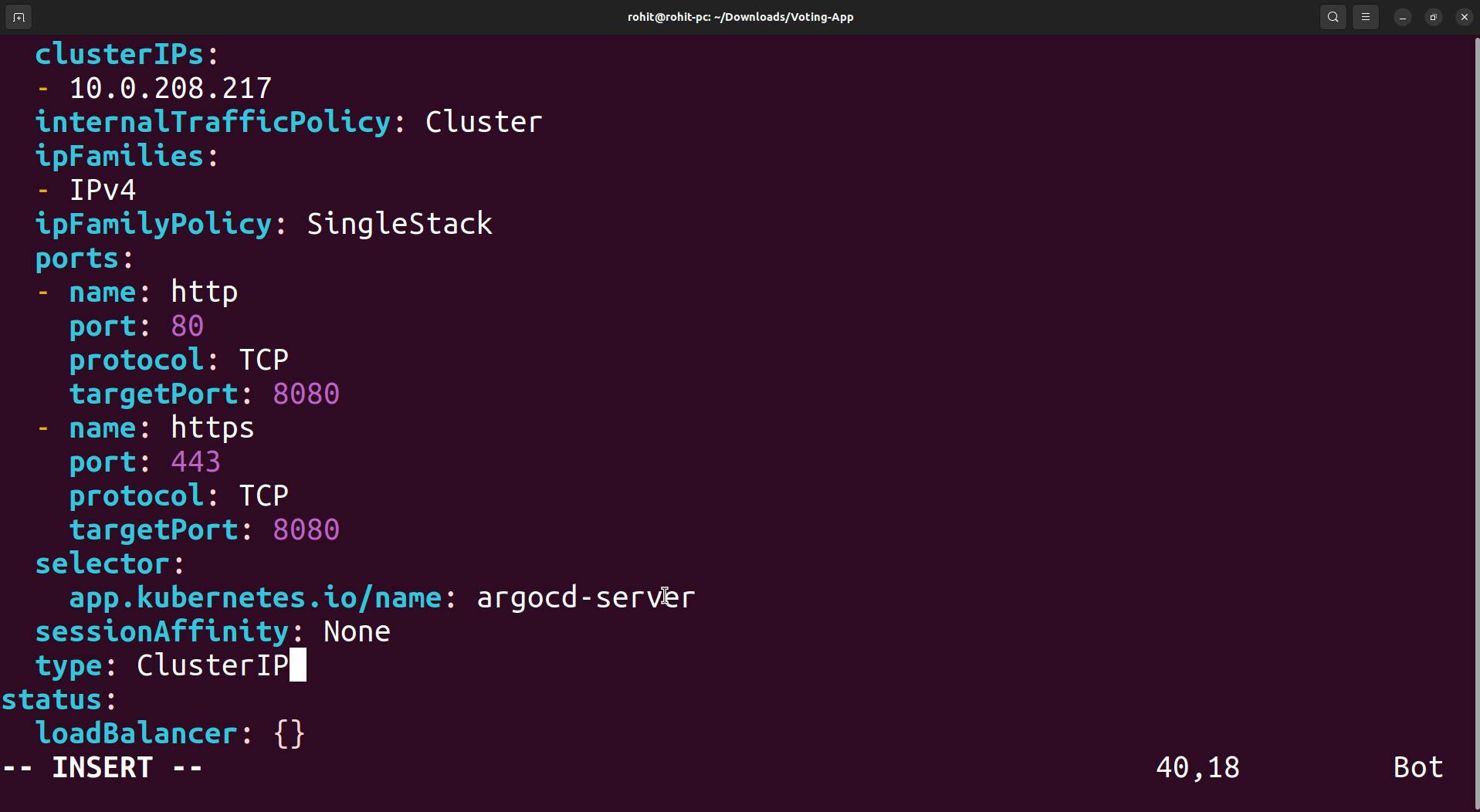
Here the type is ClusterIP, we will change it to NodePort.
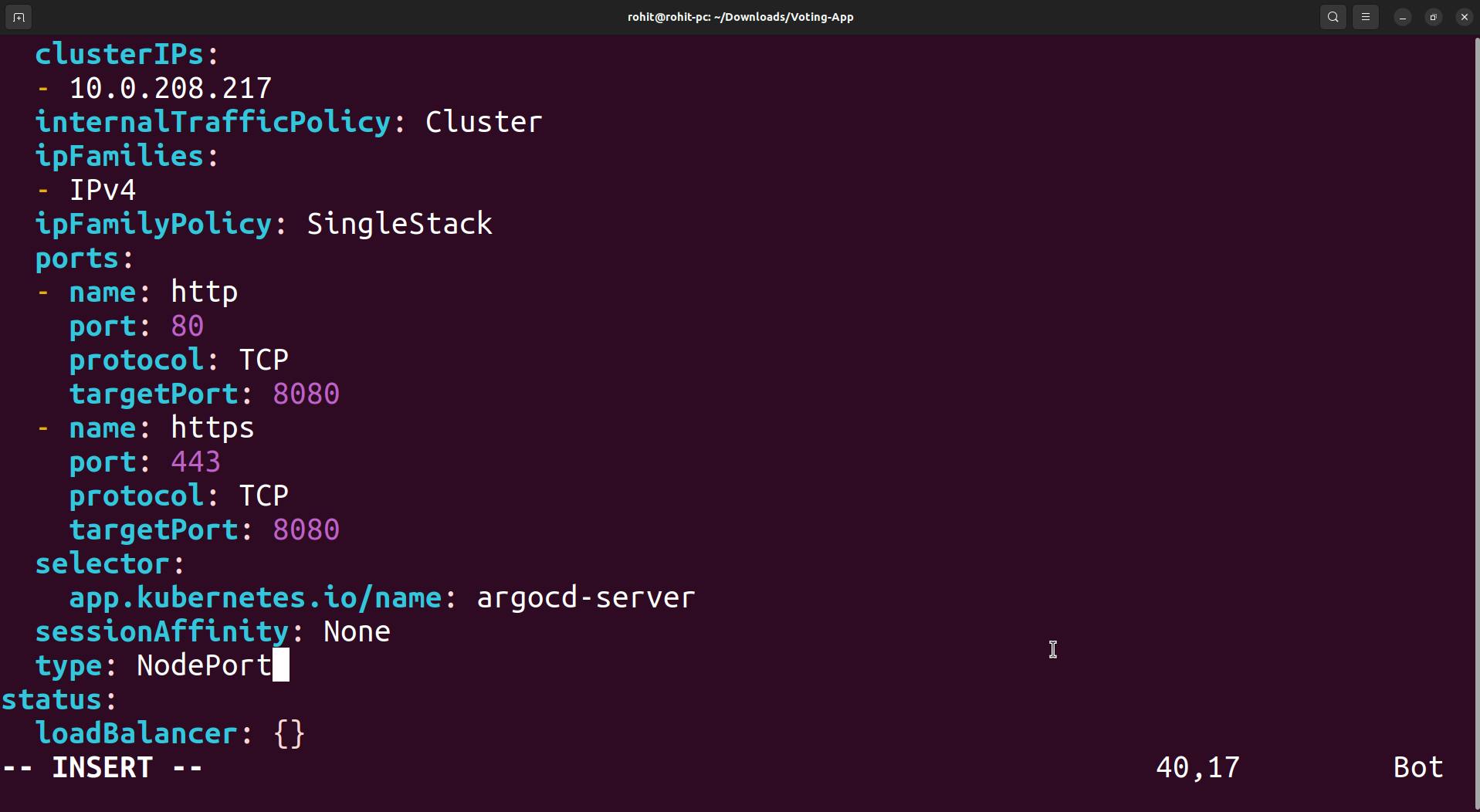
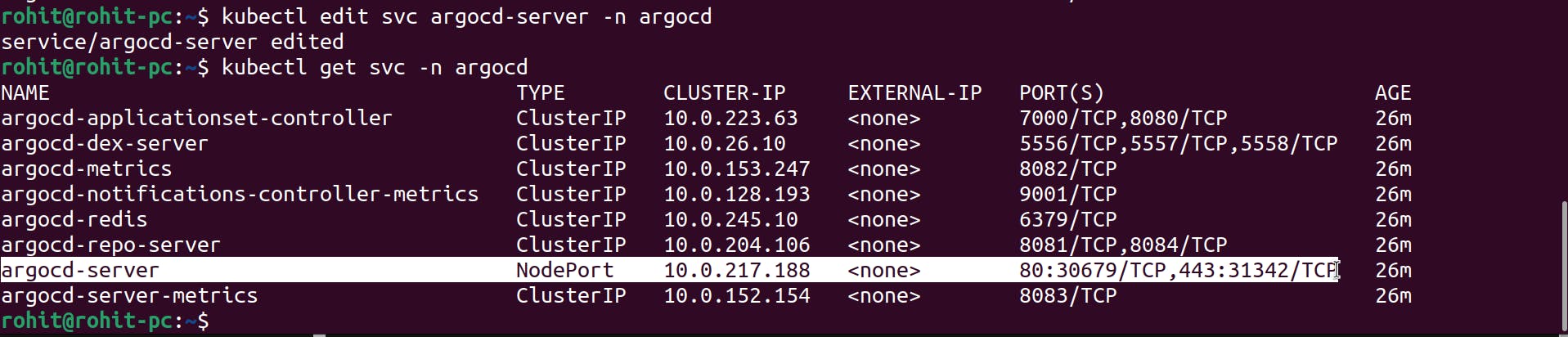
And here we get the NodePort 30679 (HTTP NodePort).
We also need Node External IP, to get this External IP use the following command.kubectl get nodes -o wide
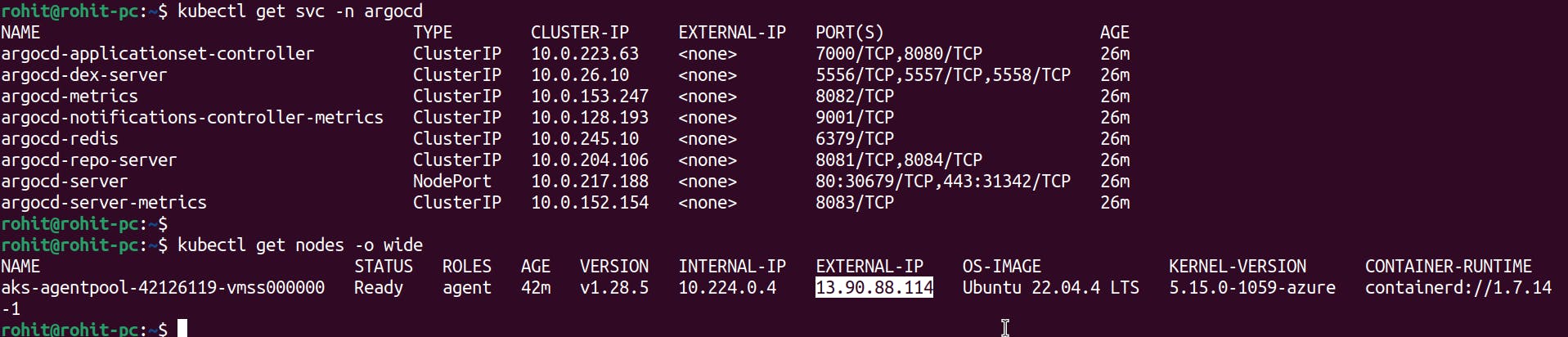
Here we get External IP and we also have a NodePort.Now go in the browser and try to access the Argo-CD UI .
You cannot access it here because we have not opened the port in the Network Security Group or Network Settings.
Now go to Microsoft Azure and search for Virtual machine scale sets.
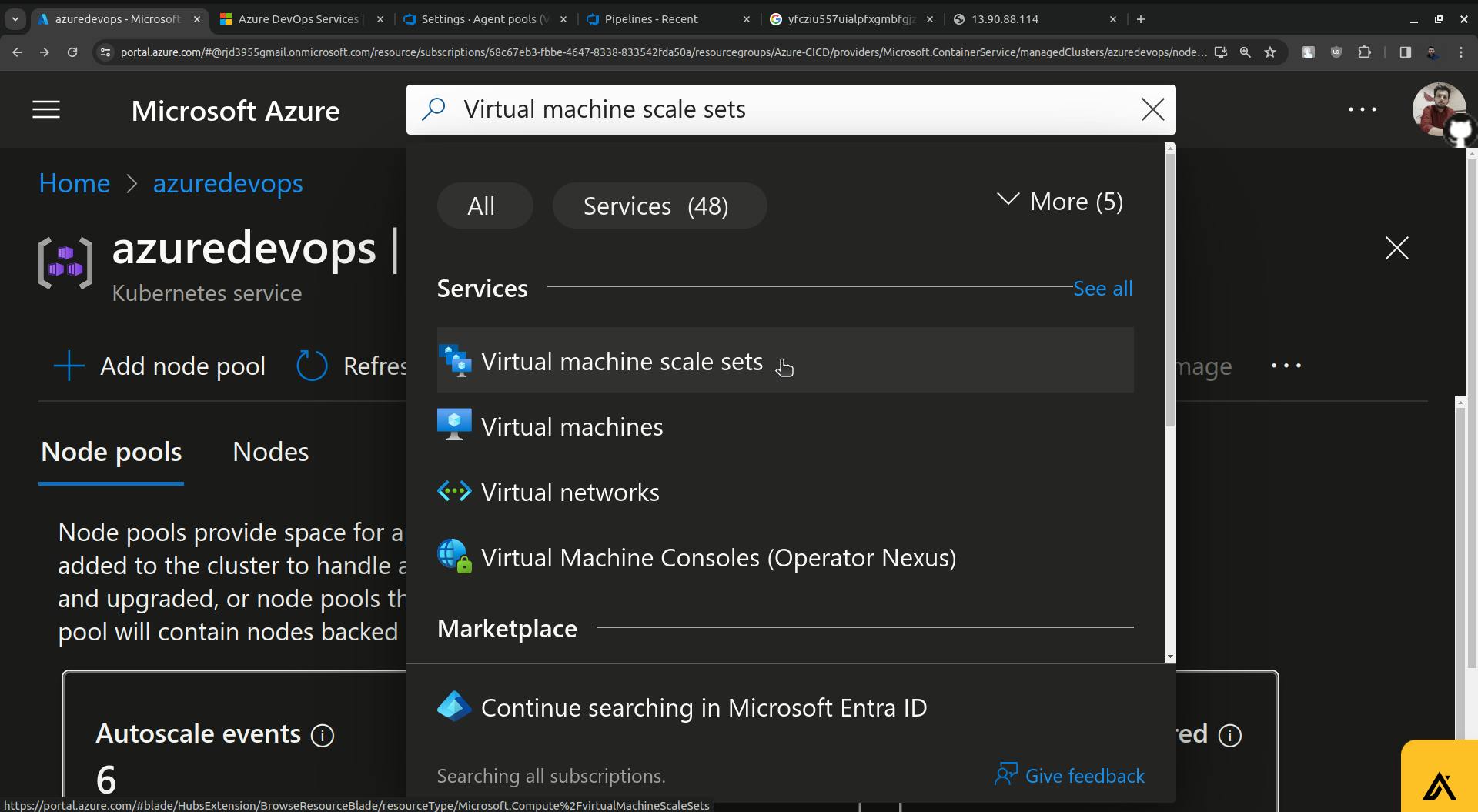
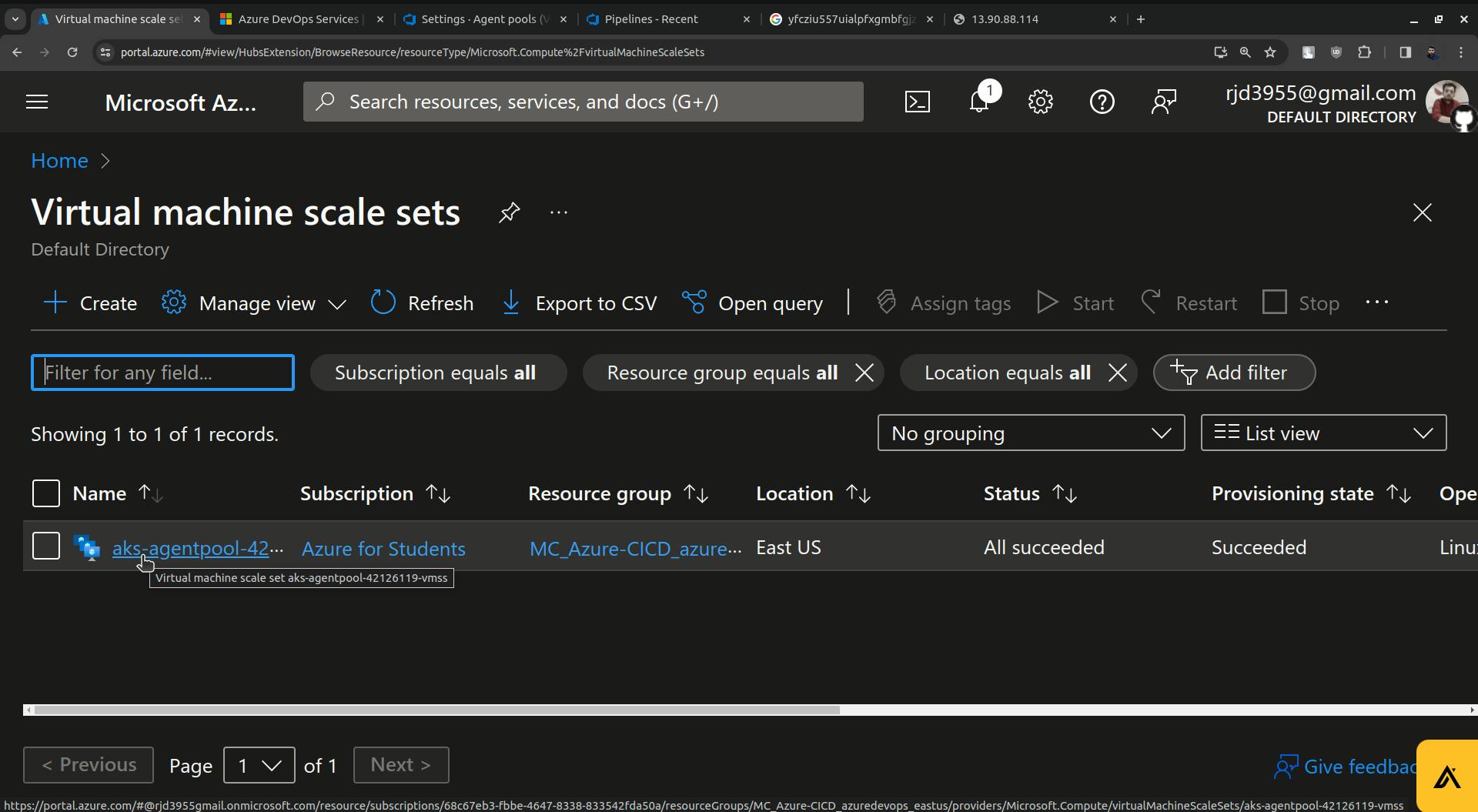
Click on instances.
Here click on Network settings.
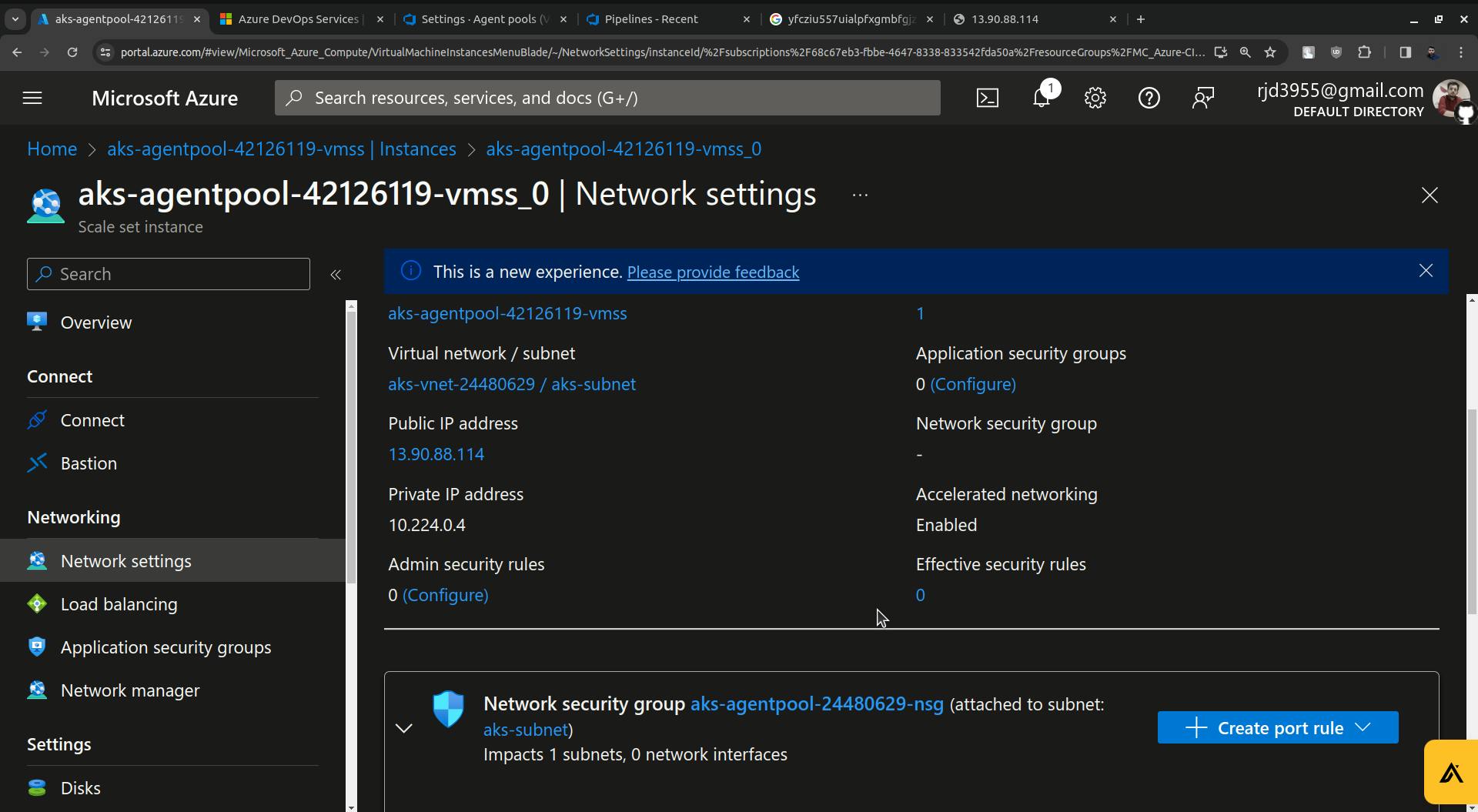
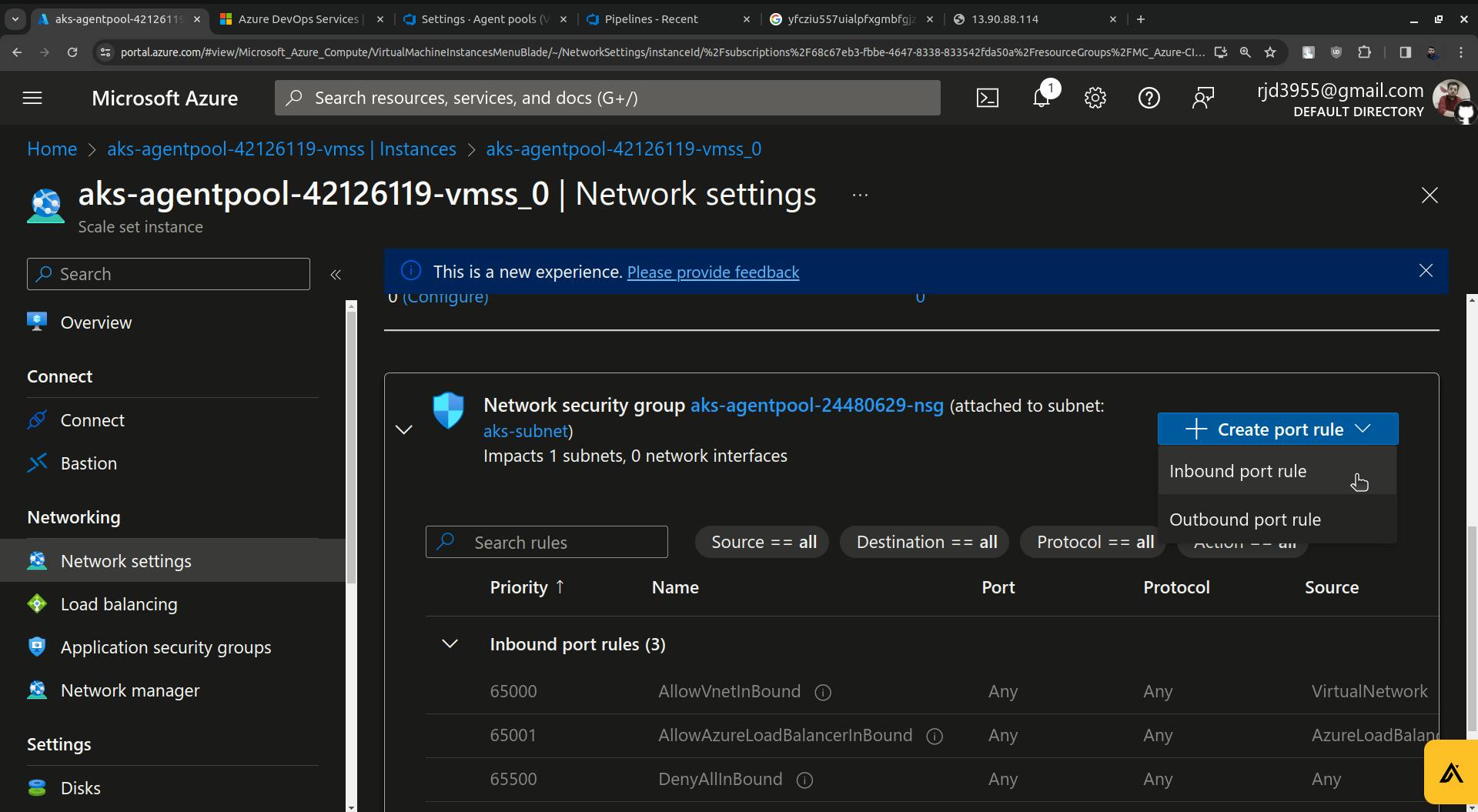
Click on Create port rule you will see two options " Inbound port rule and Outbound port rule ".
There Click on " Inbound port rule ".
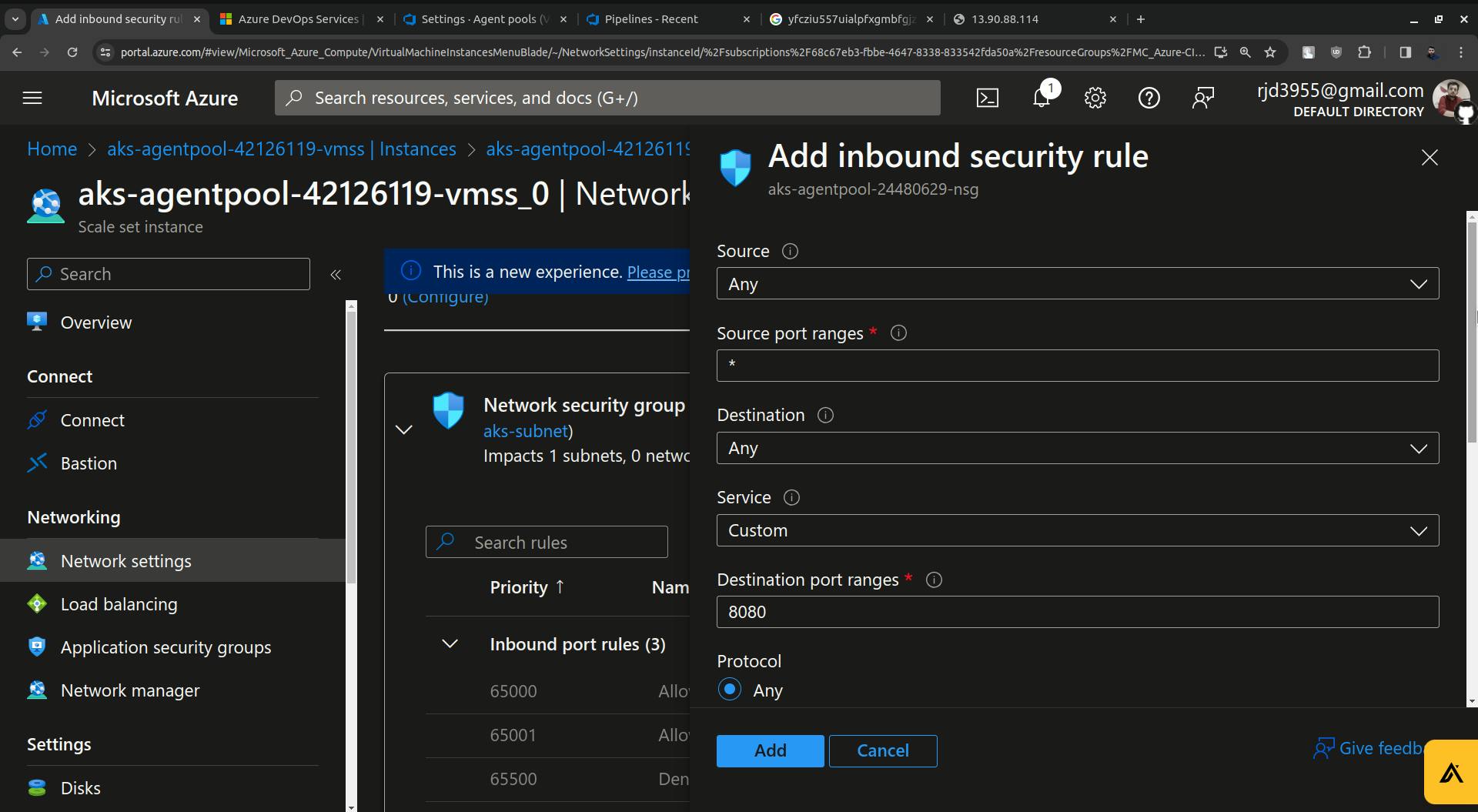
Update the destination port from 8080 to 30679( in my case it is 30679 you will have some different port ).
Click on the Add button and your security rule will be created.
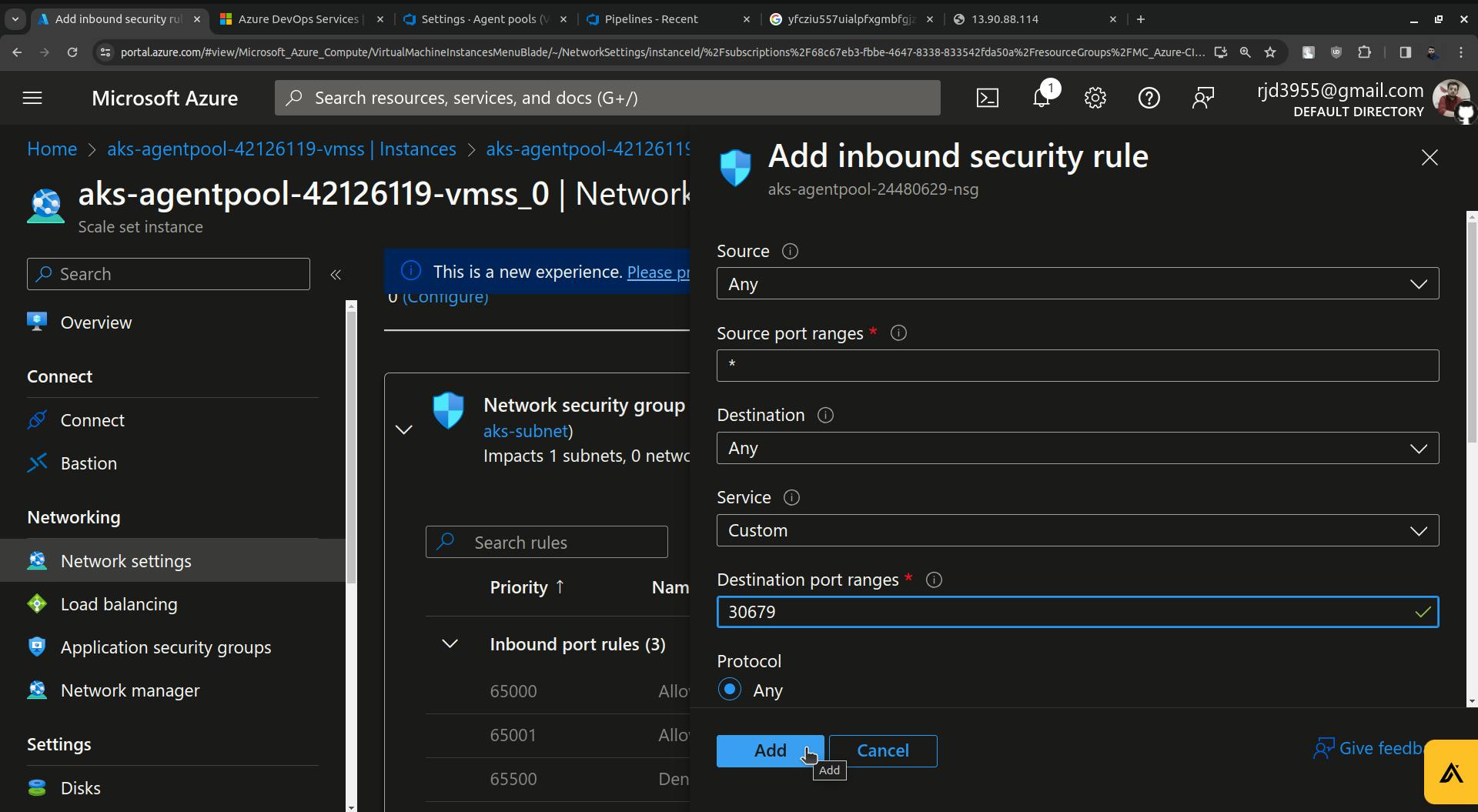
Once it is added go and try to access the ArgoCD.
Click on Advanced and also click on Proceed to 13.90.88.114 (unsafe).
You will able to see ArgoCD UI just using the username as admin and password which we get previously and we also decode it from base64.
Click on SIGN IN.
Now to connect ArgoCD with Azure Repo we need the access token(we require the access token because the Azure repo is secure no one can access it without permission).
On Azure DevOps create an access token to access the repo.
Click on the New Token.
I just granted Full access but you can also grant only the Read access.
Copy the token and store it somewhere so that you will not need to create more tokens further if needed.
Come to ArgoCD, go to settings, and click on Repositories.
You will see the option CONNECT REPO, click on it.
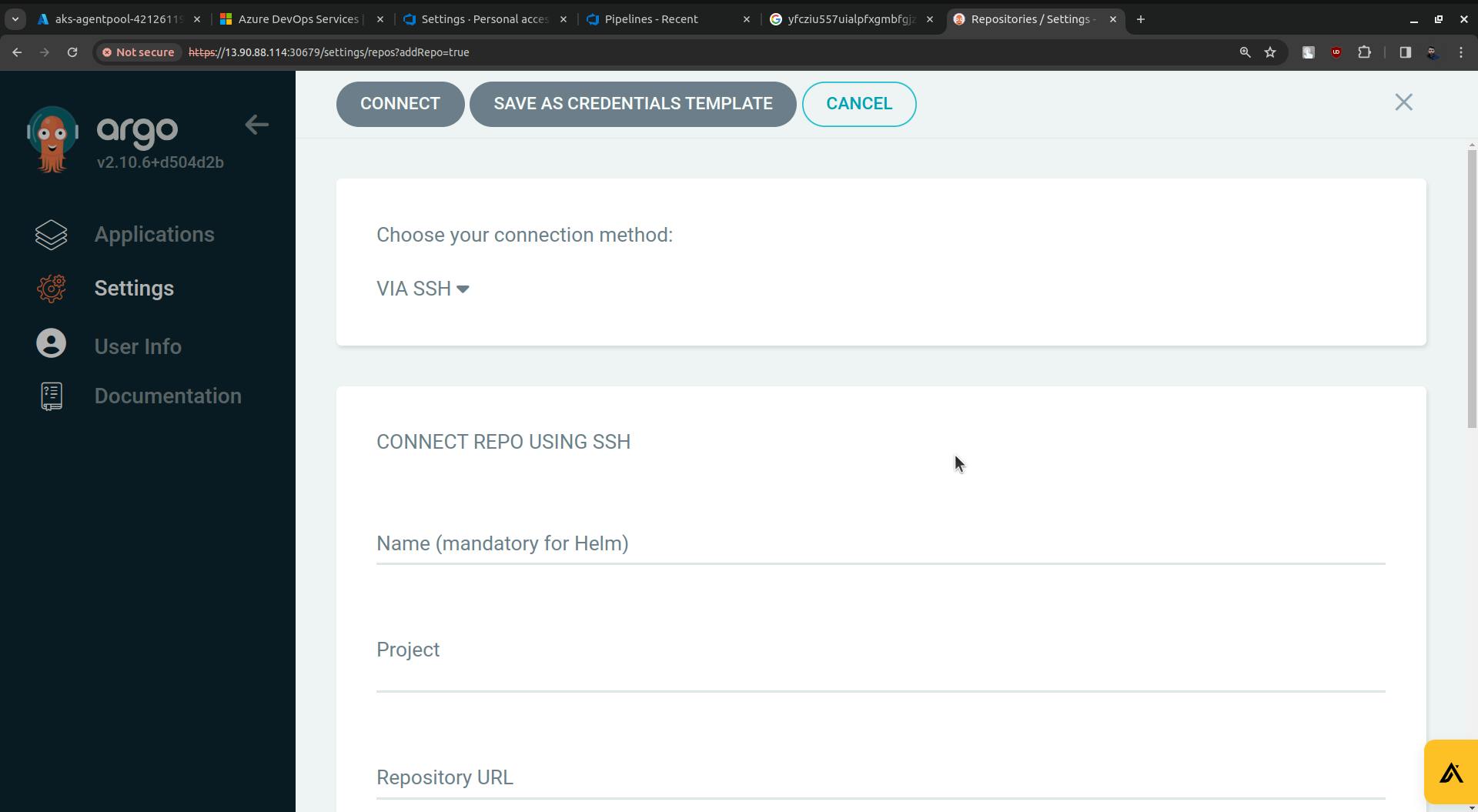
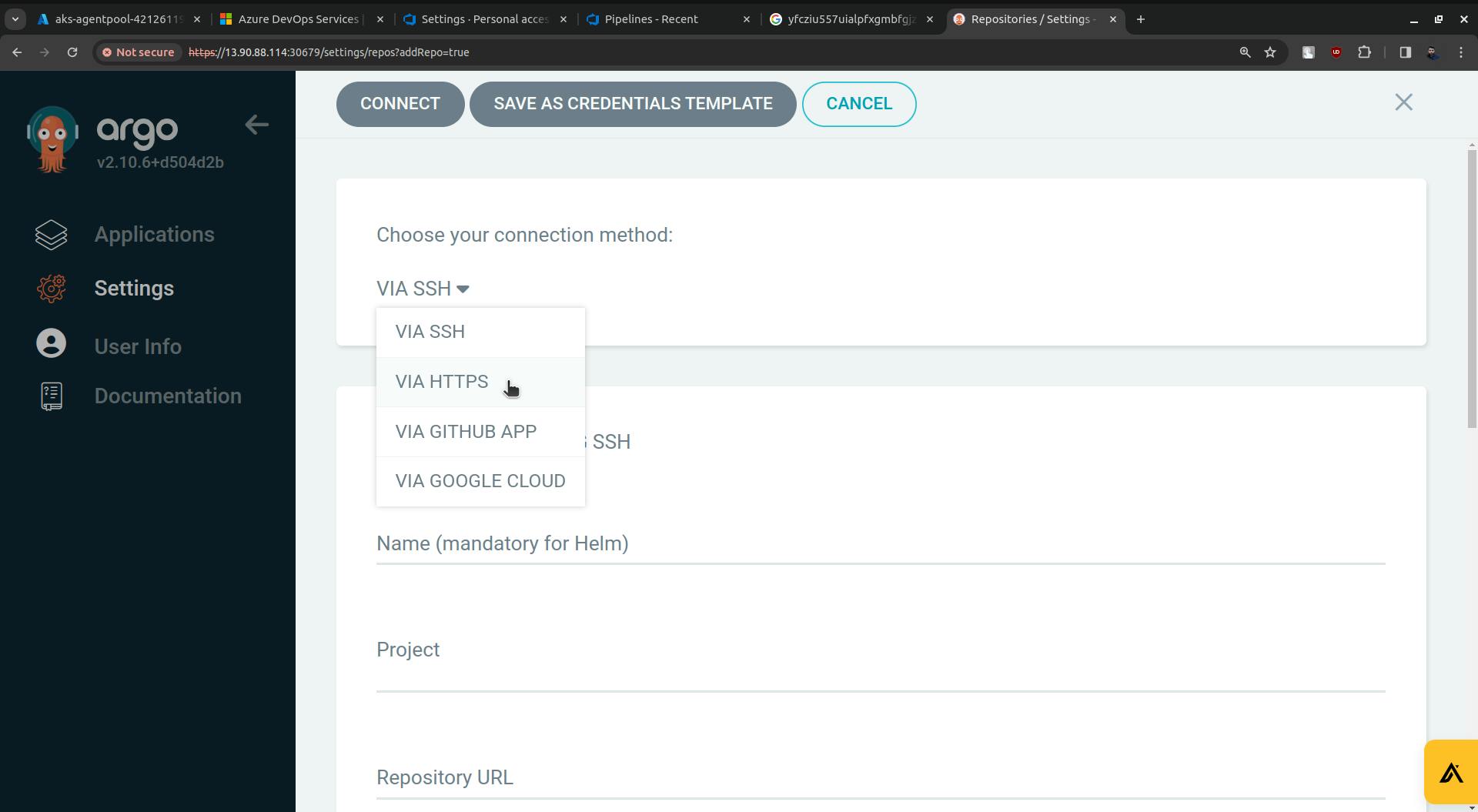
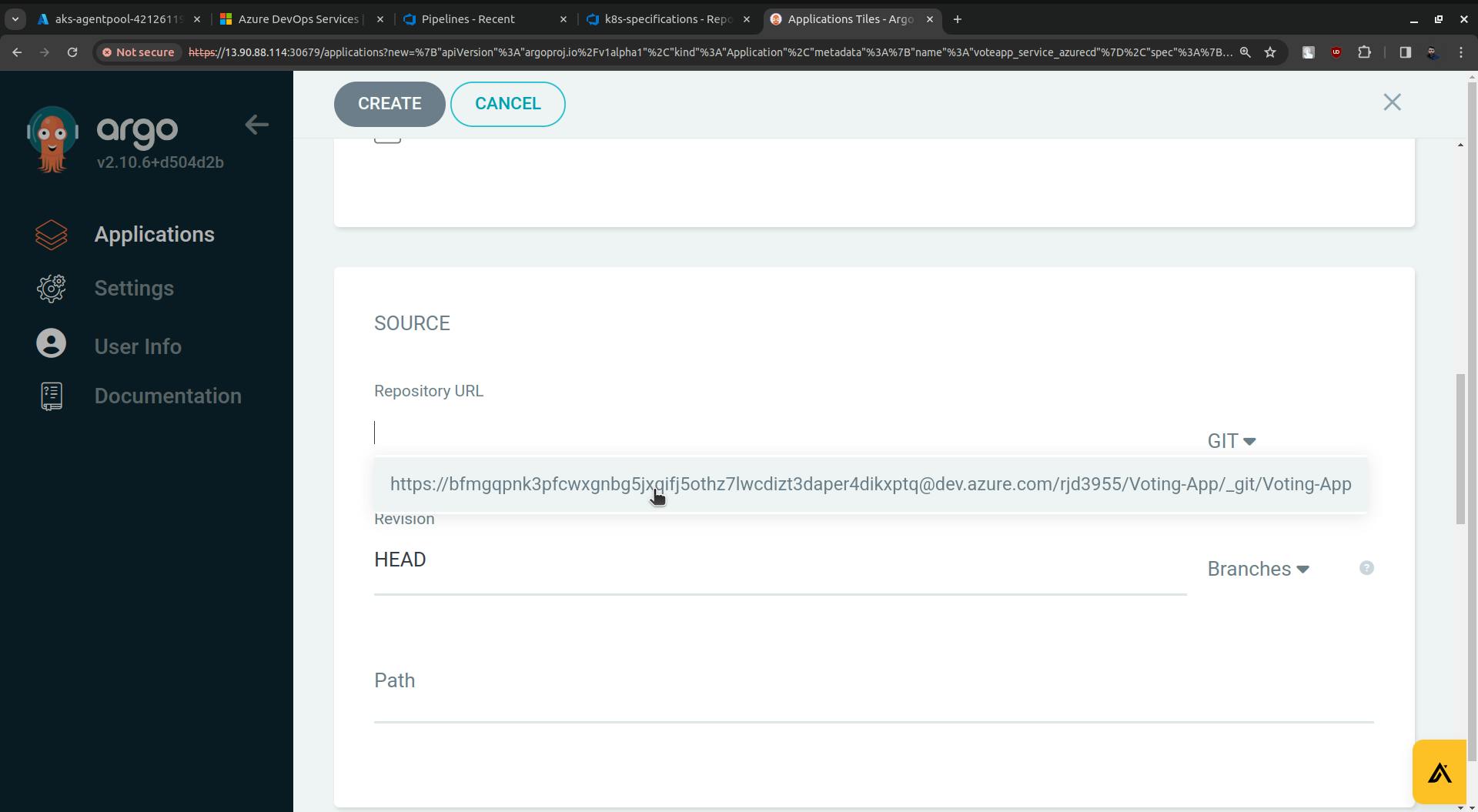
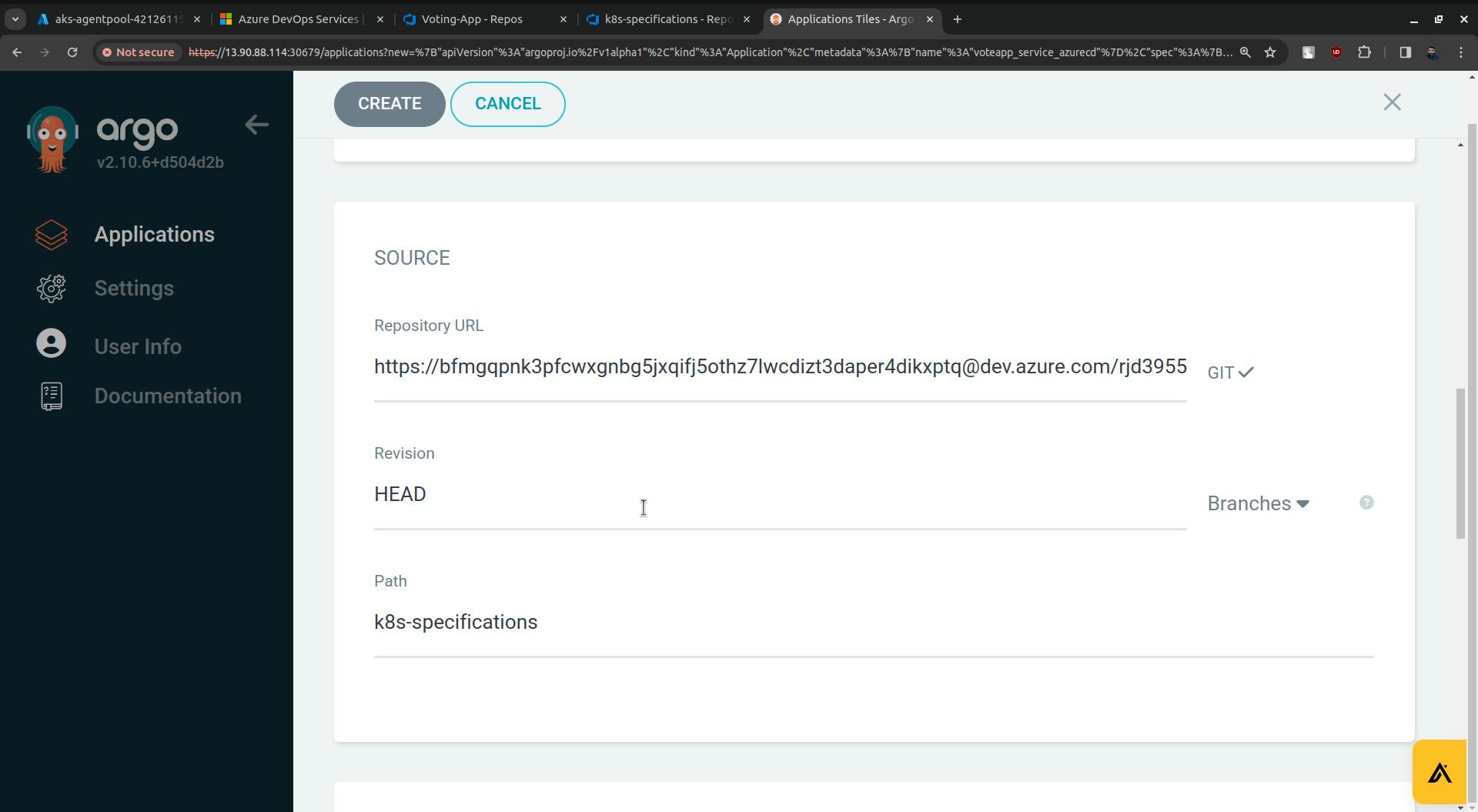
For Repository URL go to Azure Repo. Click on the Clone.
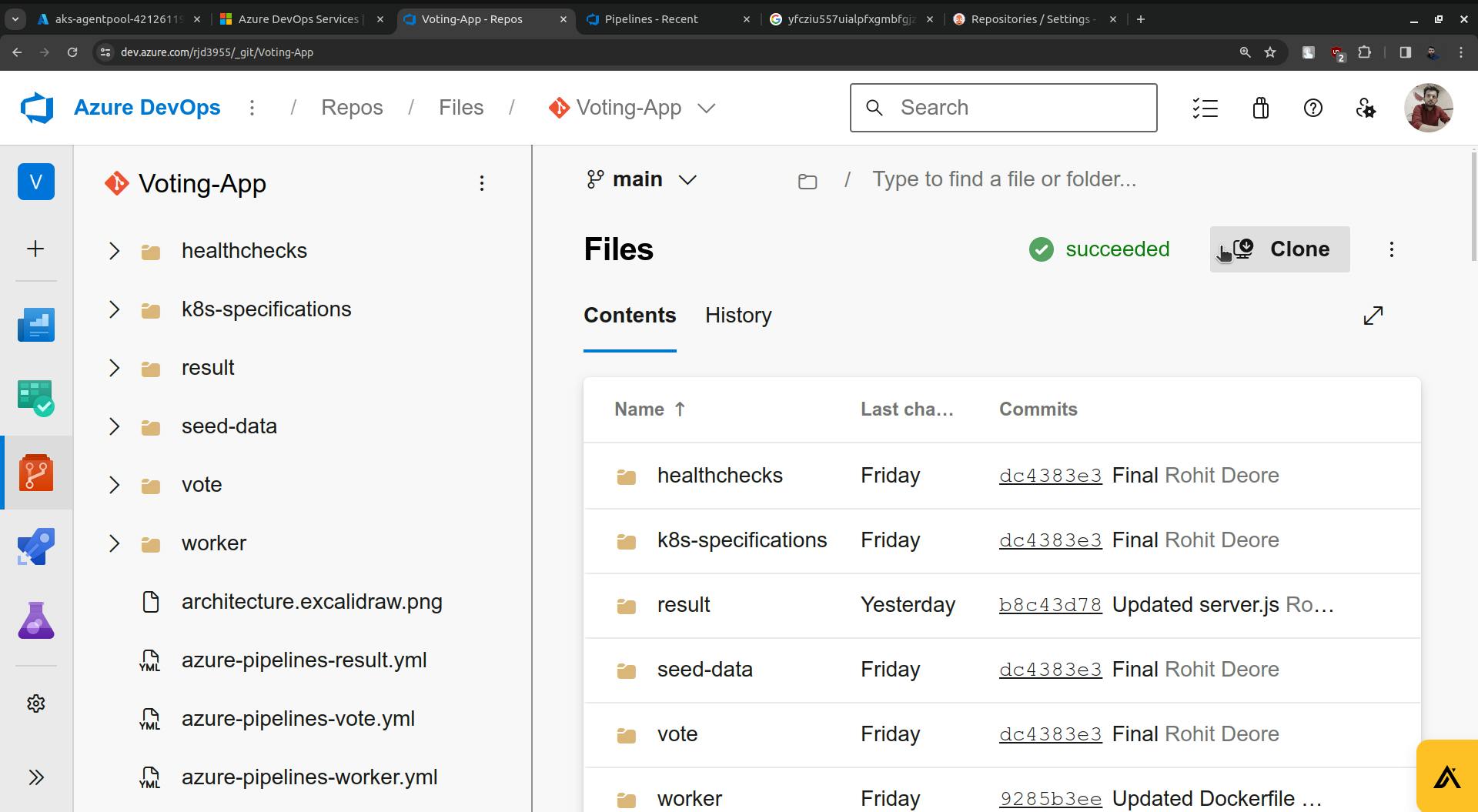
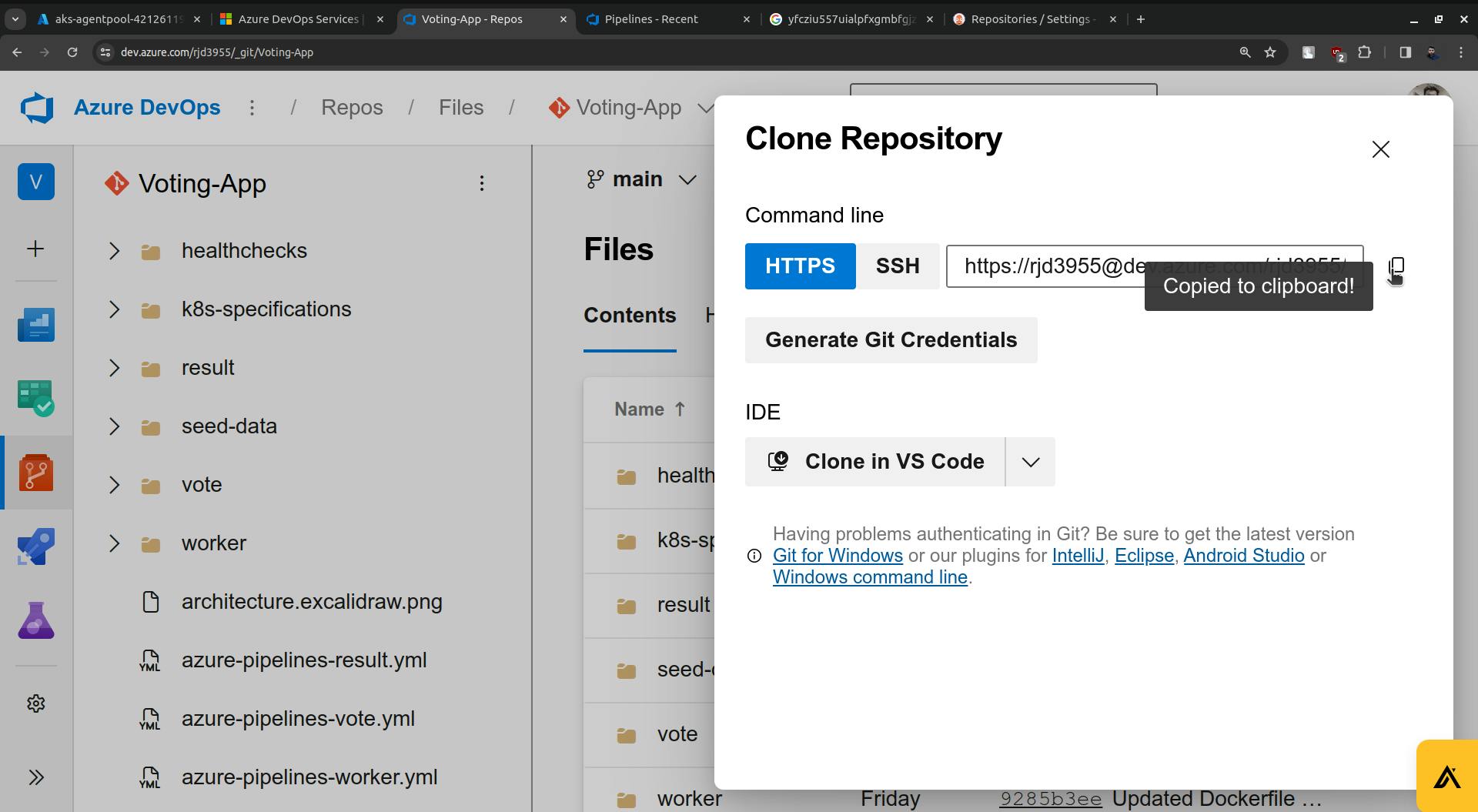
Copy the URL and paste it into the Repository URL field(ArgoCD).
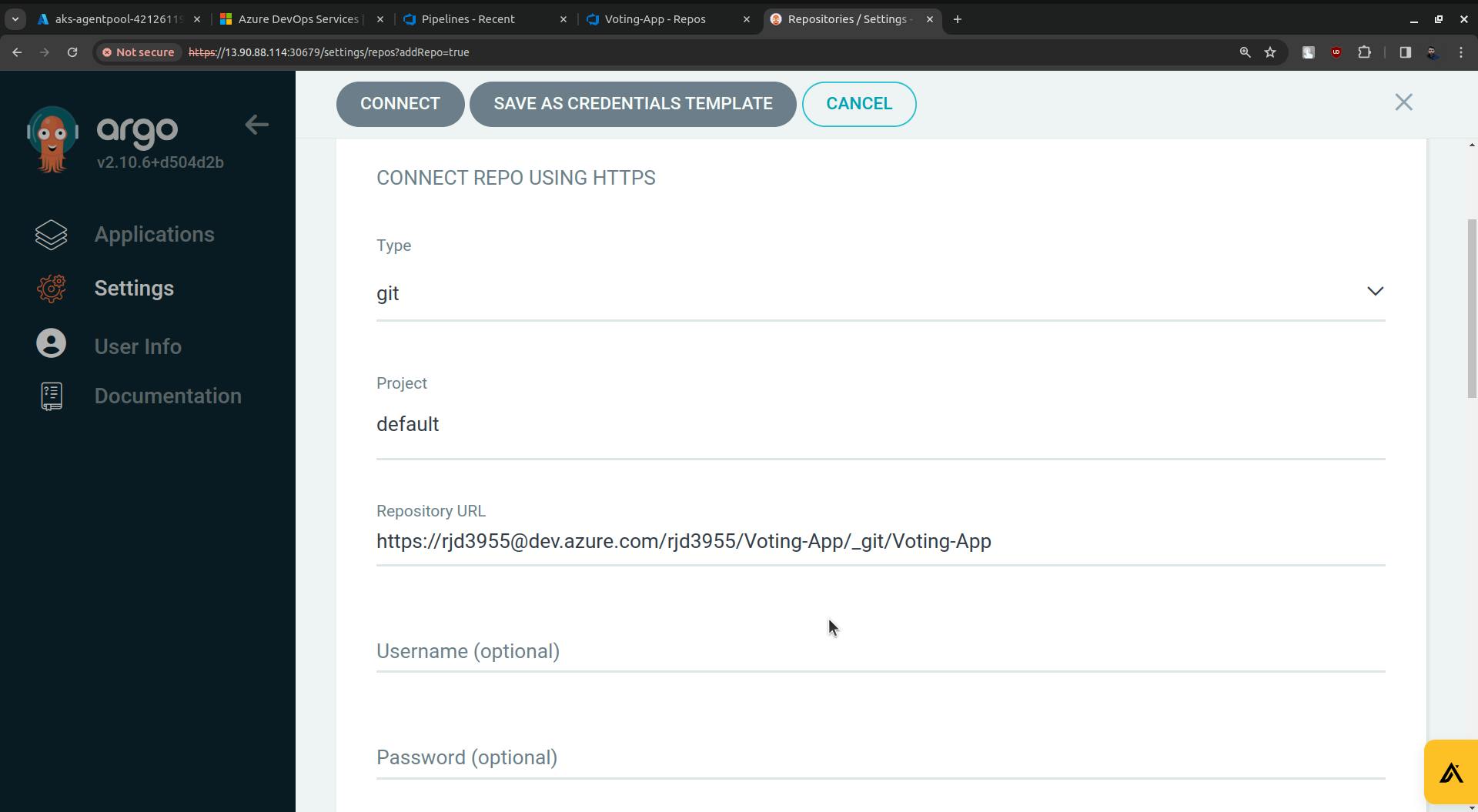
Now replace the rjd3955(in my case it is rjd3955 you will have something else) with the access token.
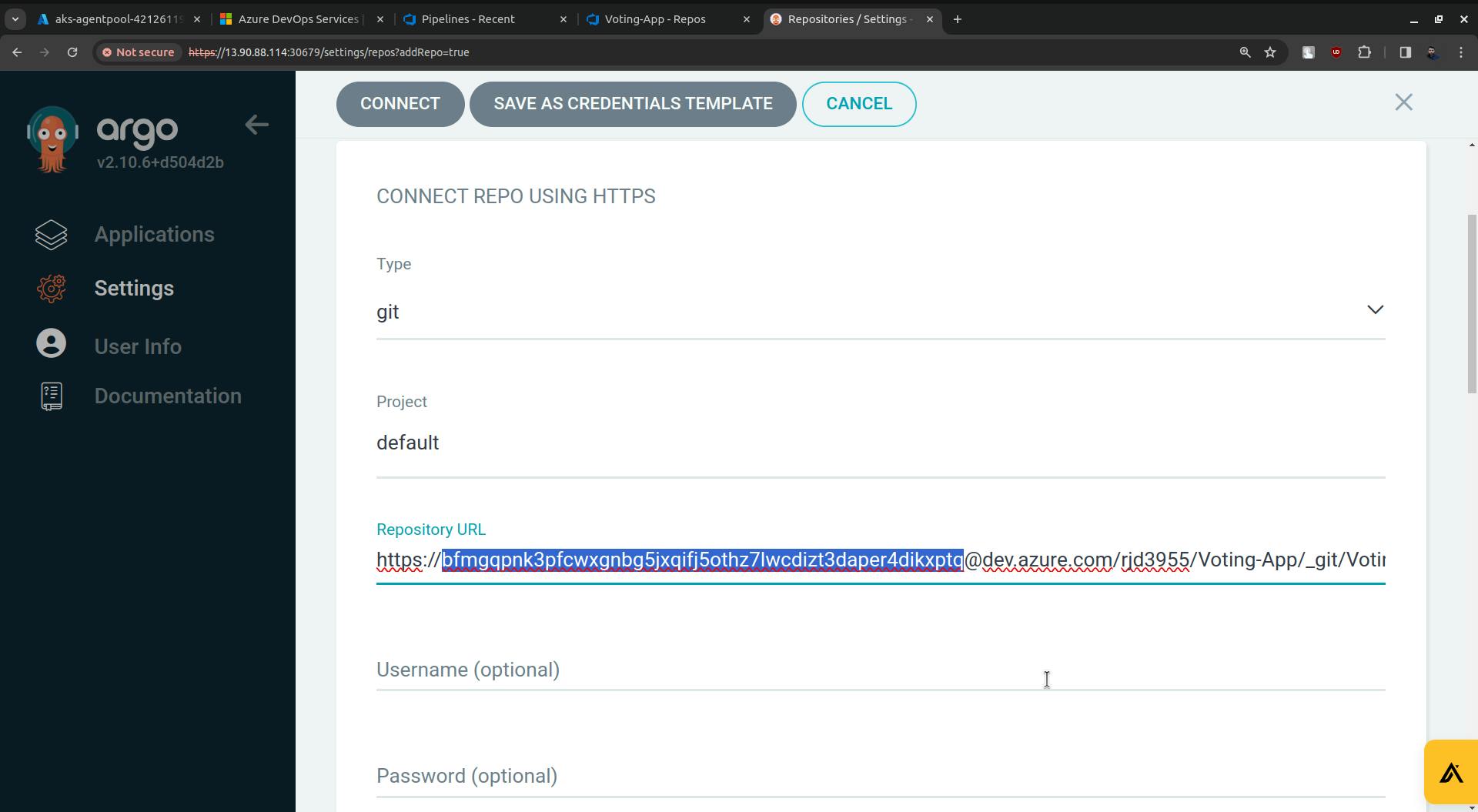
Click on the CONNECT button.
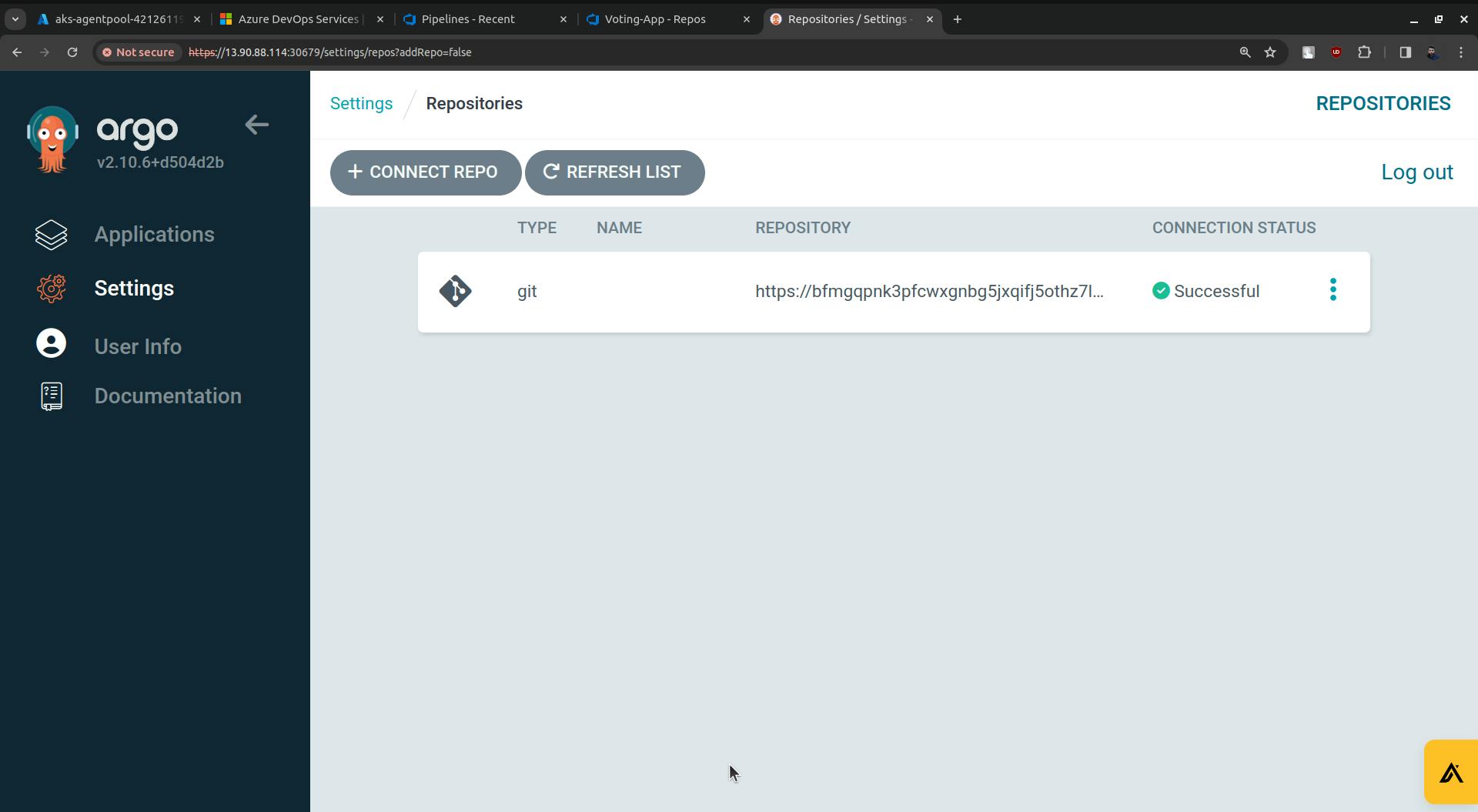
CONNECTION STATUS is Successful.
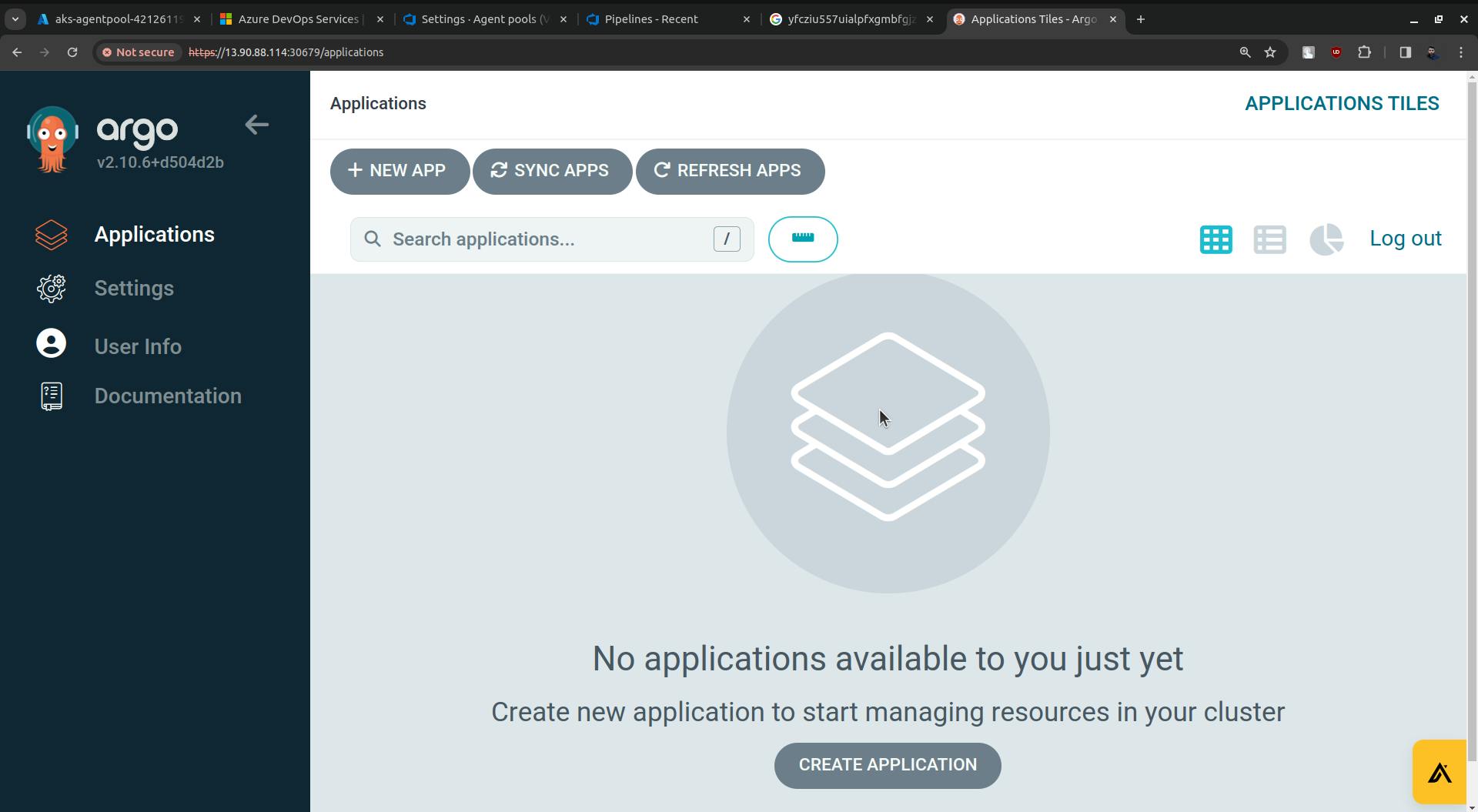
Now go to Applications, and click on NEW APP.
Click on the CREATE button.
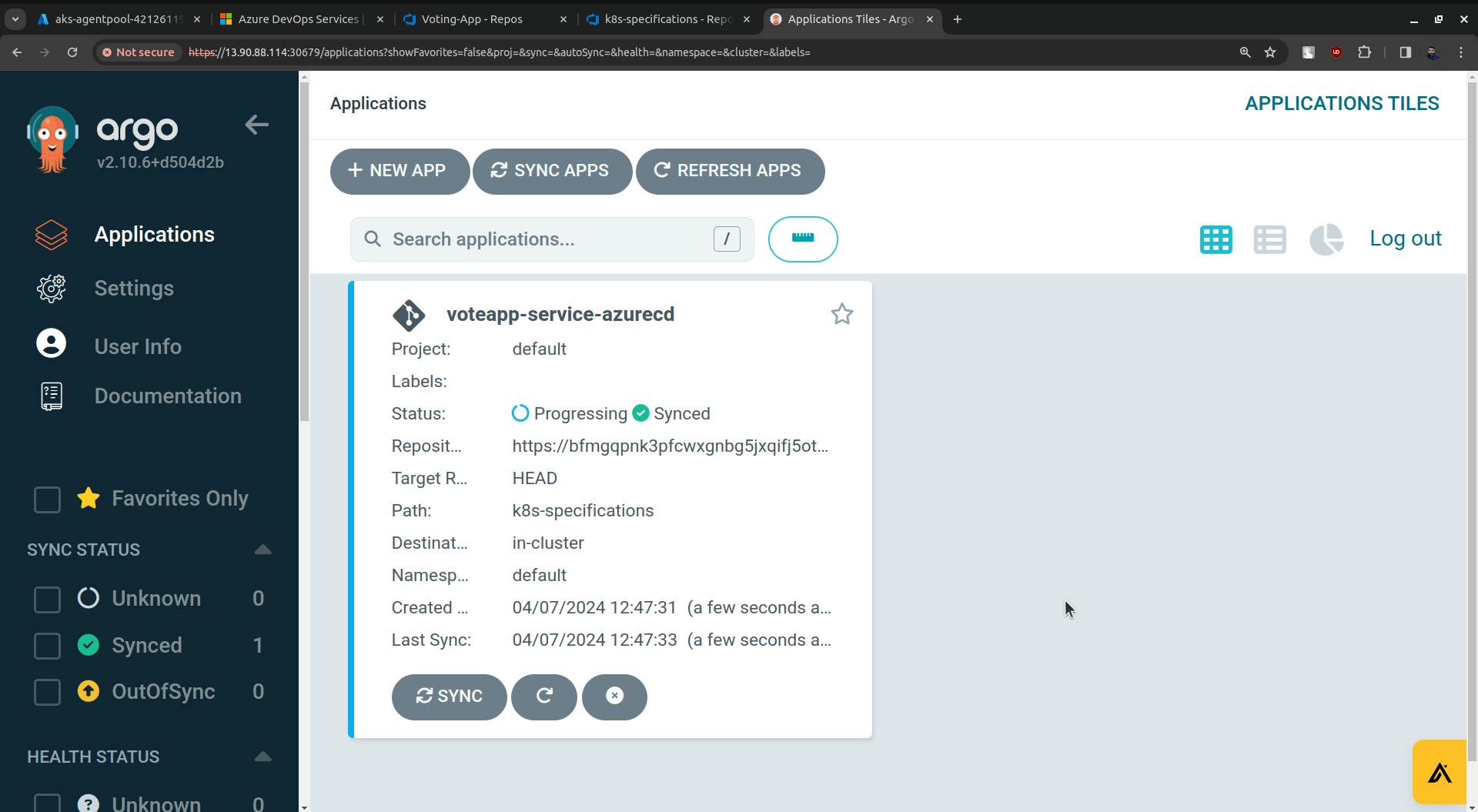
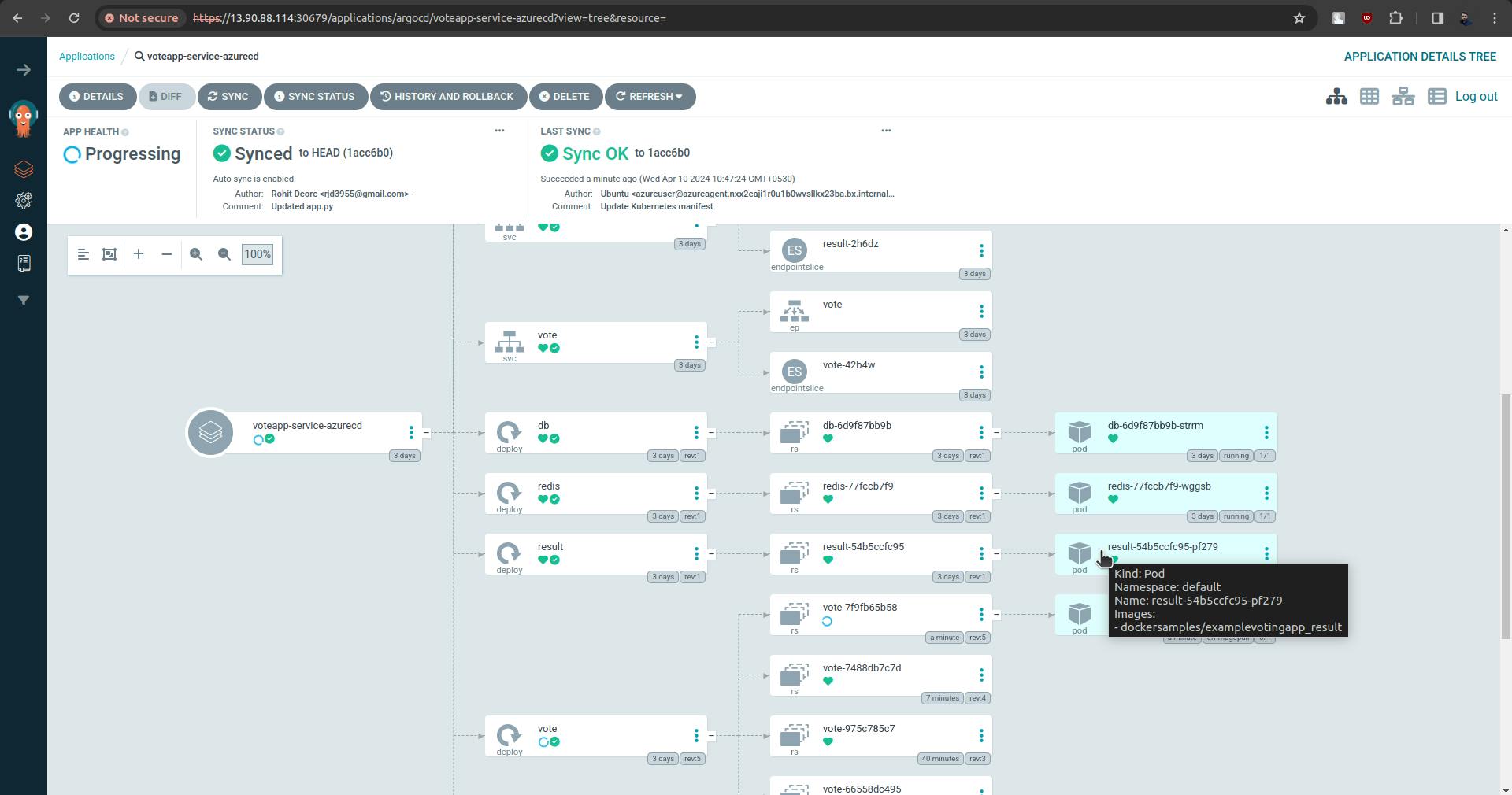
Now ArgoCD is configured and deployment is started onto to the k8s cluster automatically.
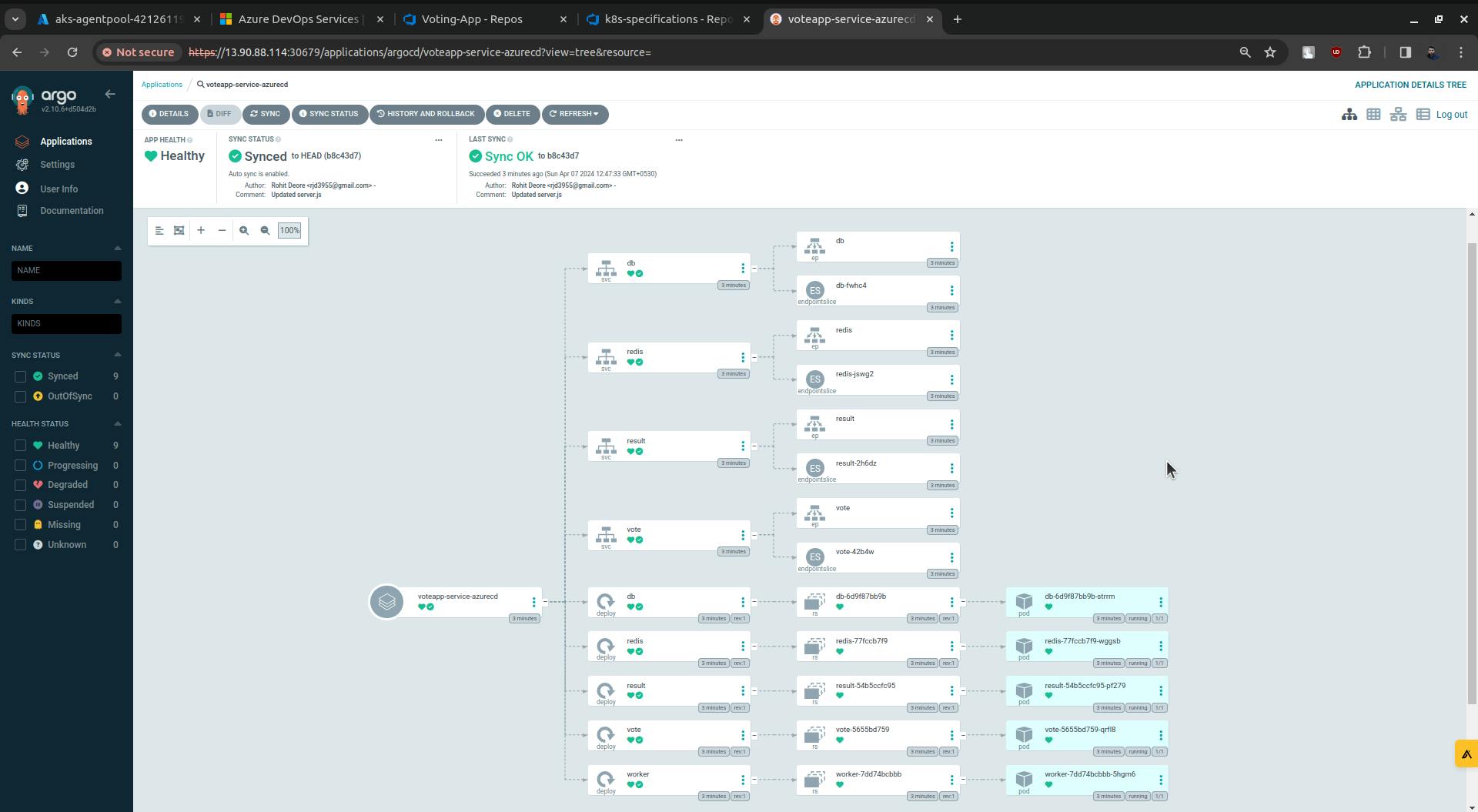
Now ArgoCD is all set, it is continuously looking at the manifest files which are in the k8s-specifications folder. If ArgoCD sees any changes to the manifest file it automatically deploys them onto the cluster.
Now to update the manifest files we need to add the update stage in pipelines. So as we make changes in code and commit is made those changes will reflected in manifest files and once the argo sees that there are updates in manifest files it will deploy those changes in the k8s cluster.
Go to Pipelines on the Azure DevOps platform.
Click on the Vote-Service pipeline.
Edit Pipeline.
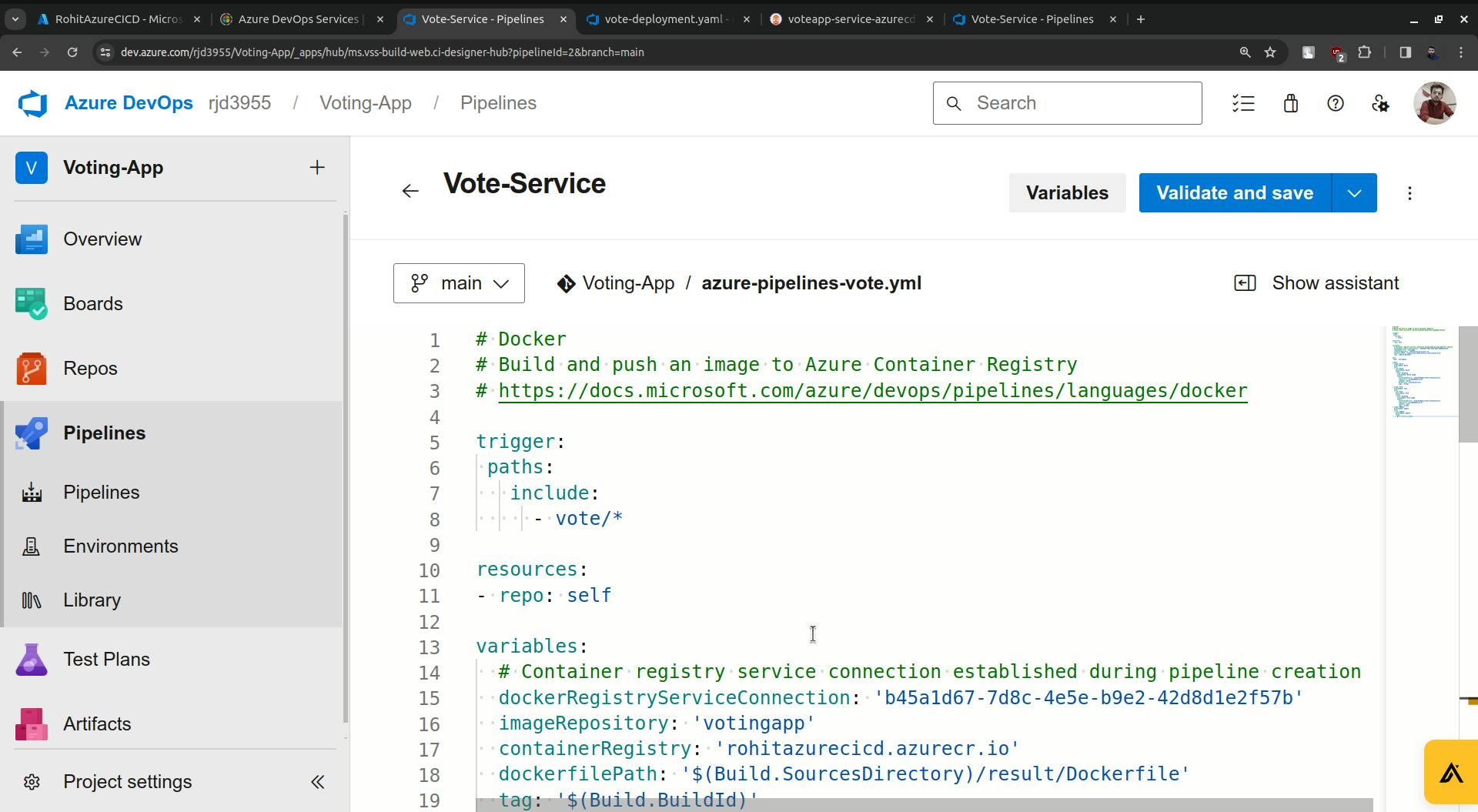
Just add a new stage in the pipeline.
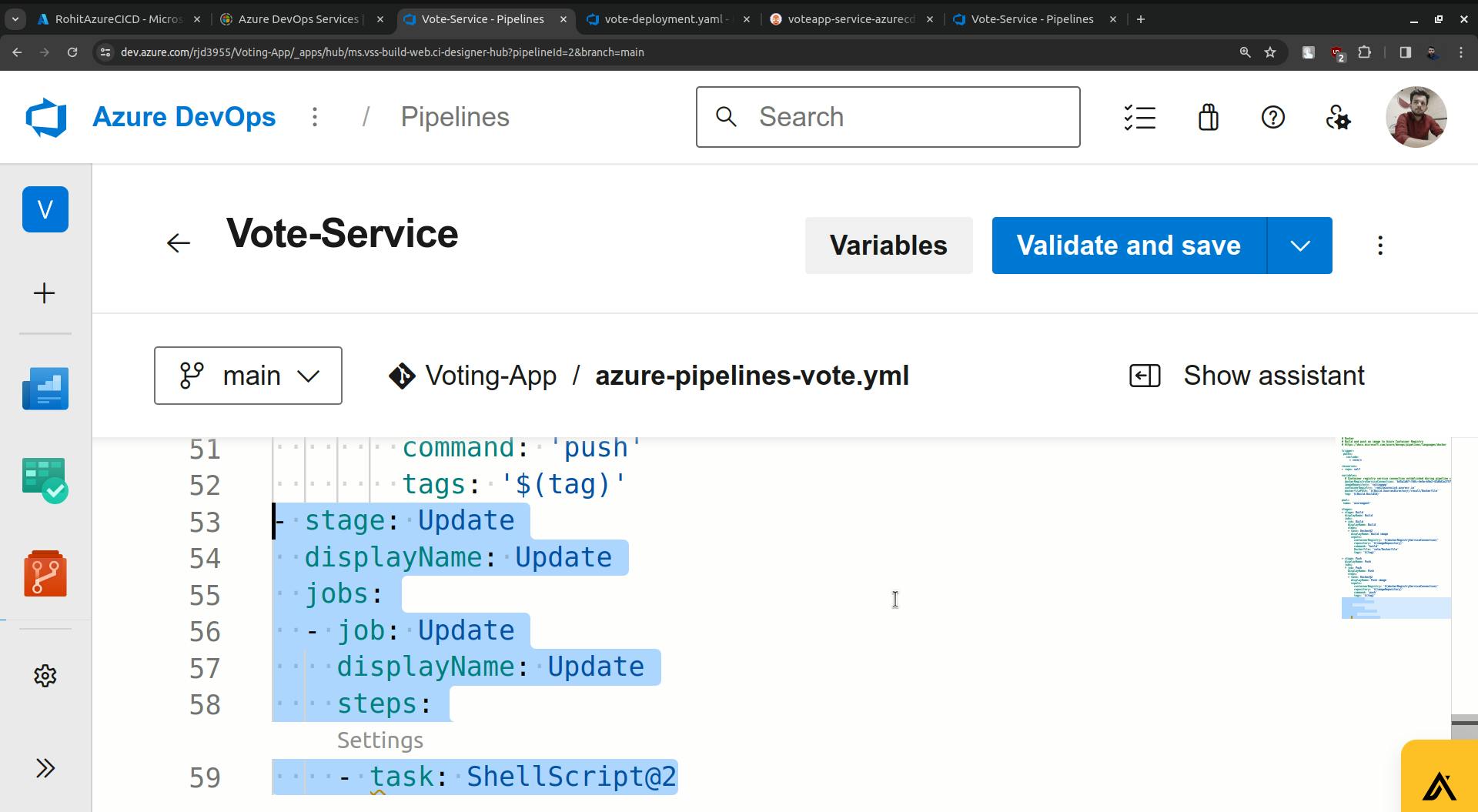
Now click on settings.
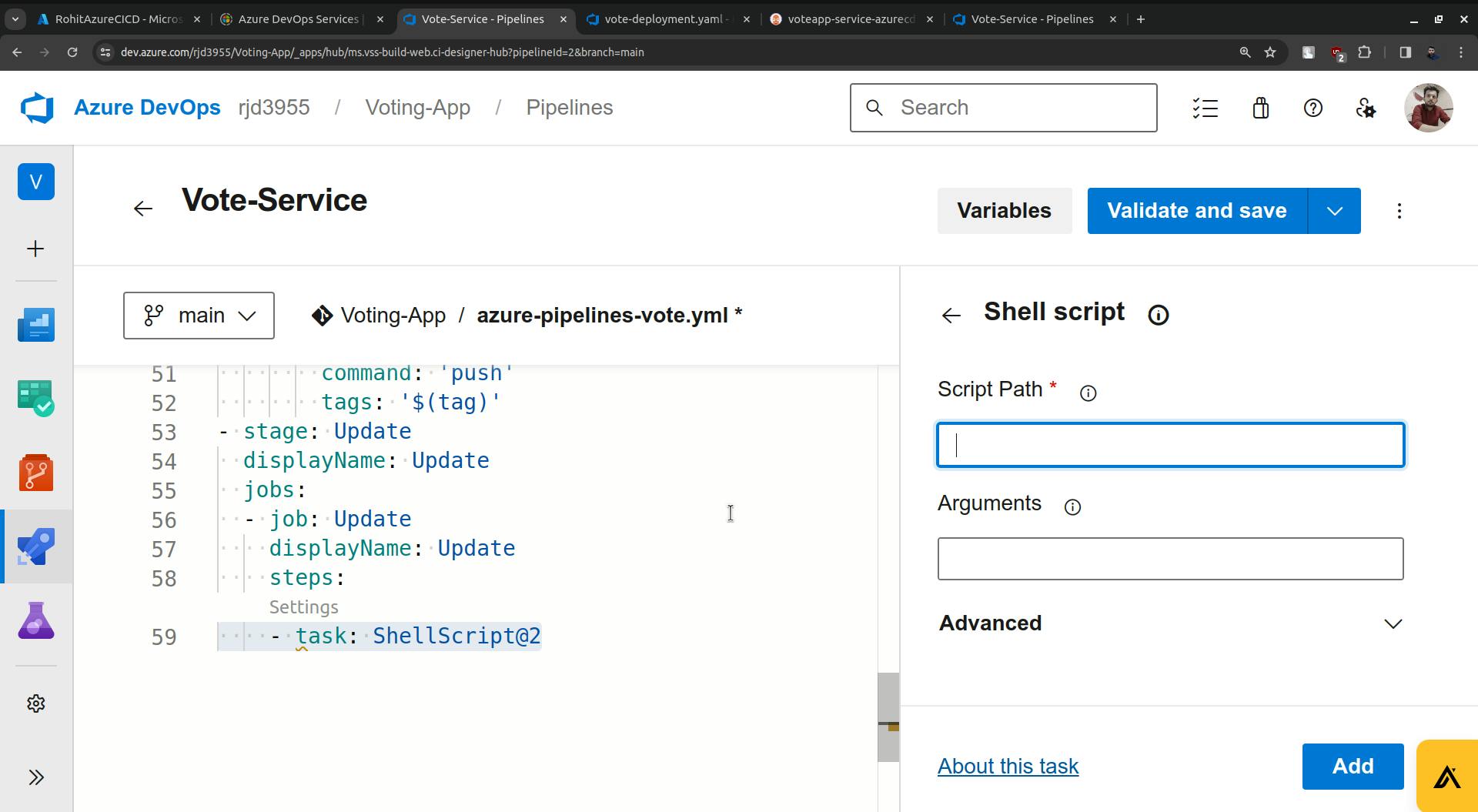
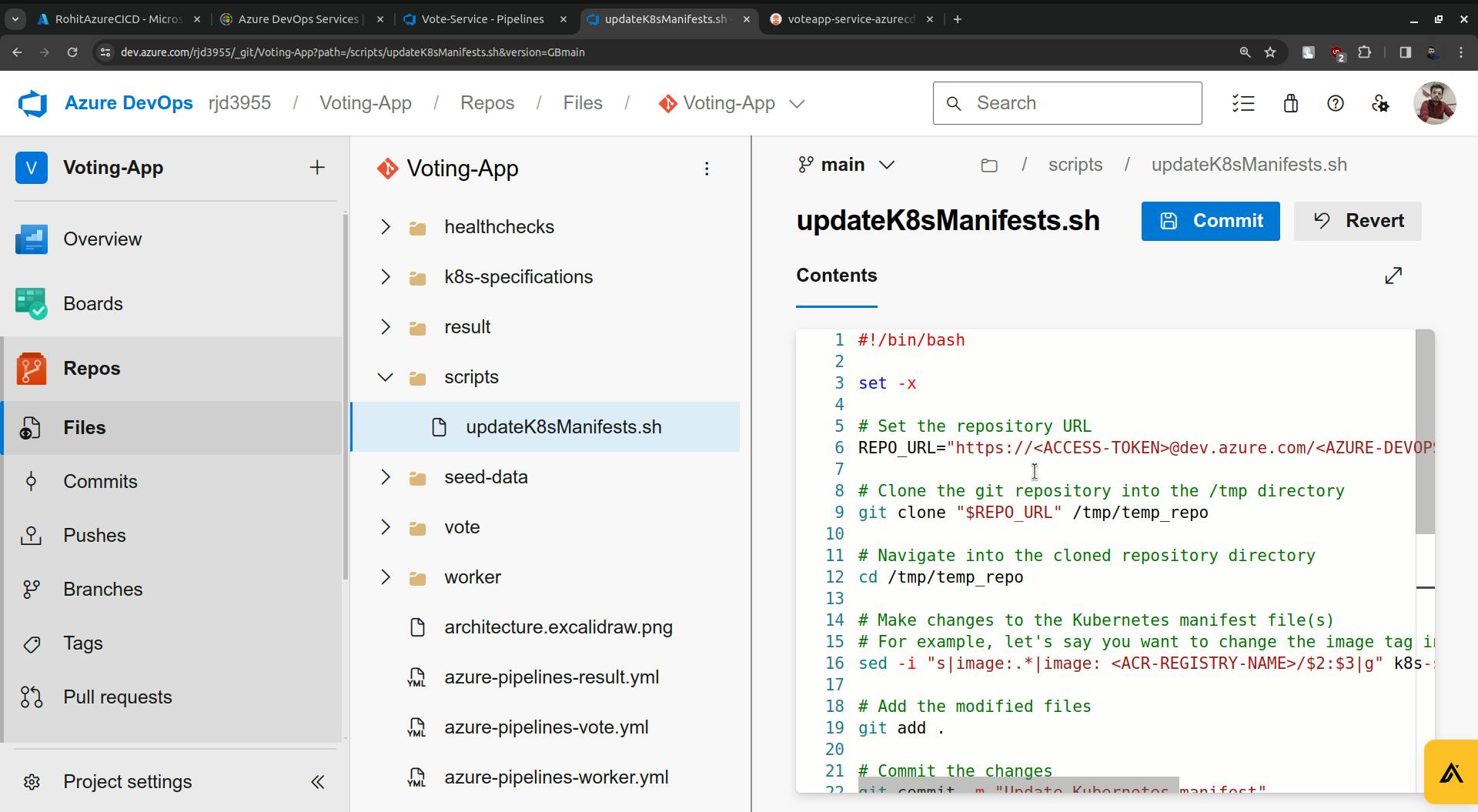
It is asking about the path to the shell script and the script is provided below.
#!/bin/bash
set -x
# Set the repository URL
REPO_URL="https://<ACCESS-TOKEN>@dev.azure.com/<AZURE-DEVOPS-ORG-NAME>/voting-app/_git/voting-app"
# Clone the git repository into the /tmp directory
git clone "$REPO_URL" /tmp/temp_repo
# Navigate into the cloned repository directory
cd /tmp/temp_repo
# Make changes to the Kubernetes manifest file(s)
# For example, let's say you want to change the image tag in a deployment.yaml file
sed -i "s|image:.*|image: <ACR-REGISTRY-NAME>/$2:$3|g" k8s-specifications/$1-deployment.yaml
# Add the modified files
git add .
# Commit the changes
git commit -m "Update Kubernetes manifest"
# Push the changes back to the repository
git push
# Cleanup: remove the temporary directory
rm -rf /tmp/temp_repo
Go to Repo and create a folder for the shell script.
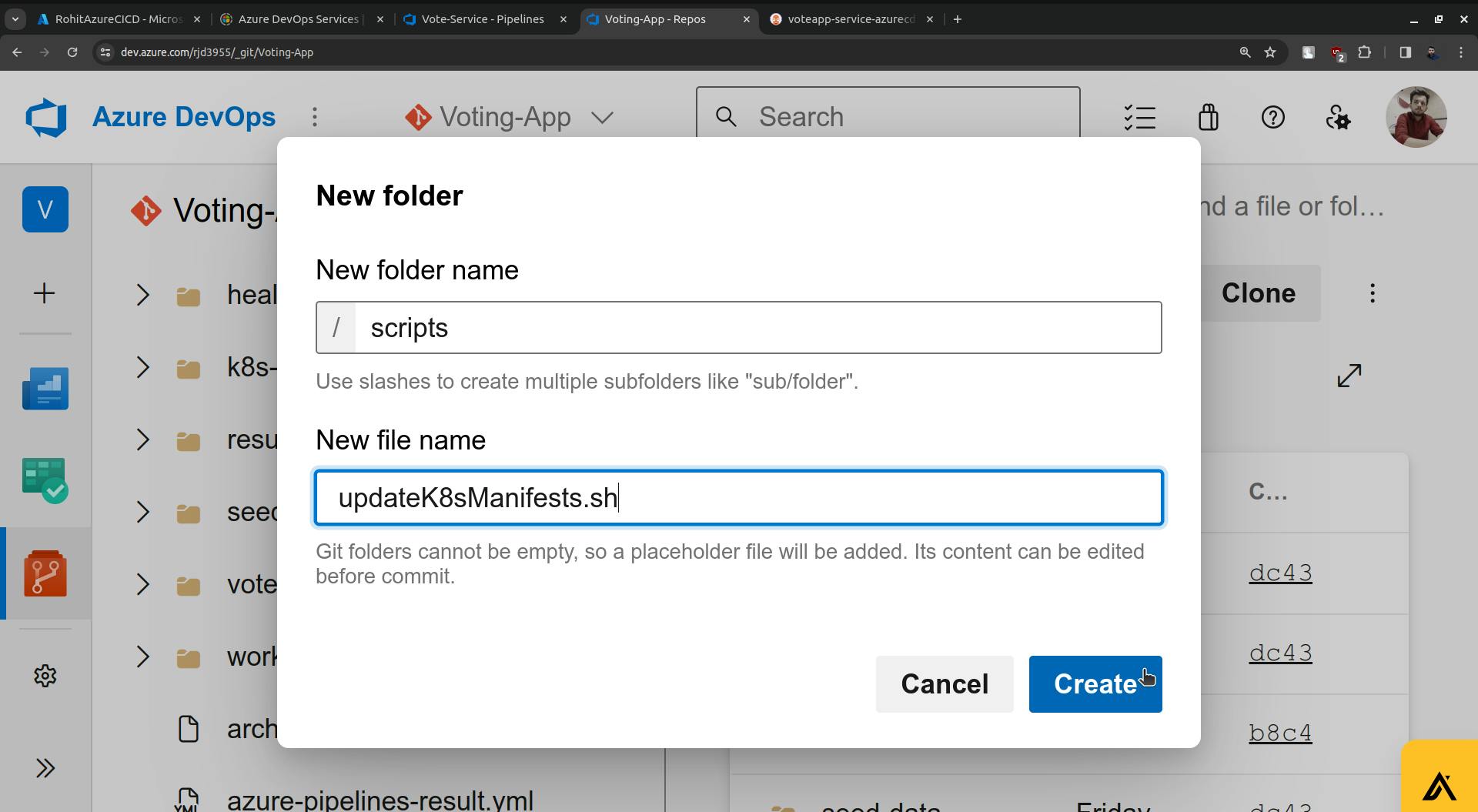
Copy the script and paste it here.
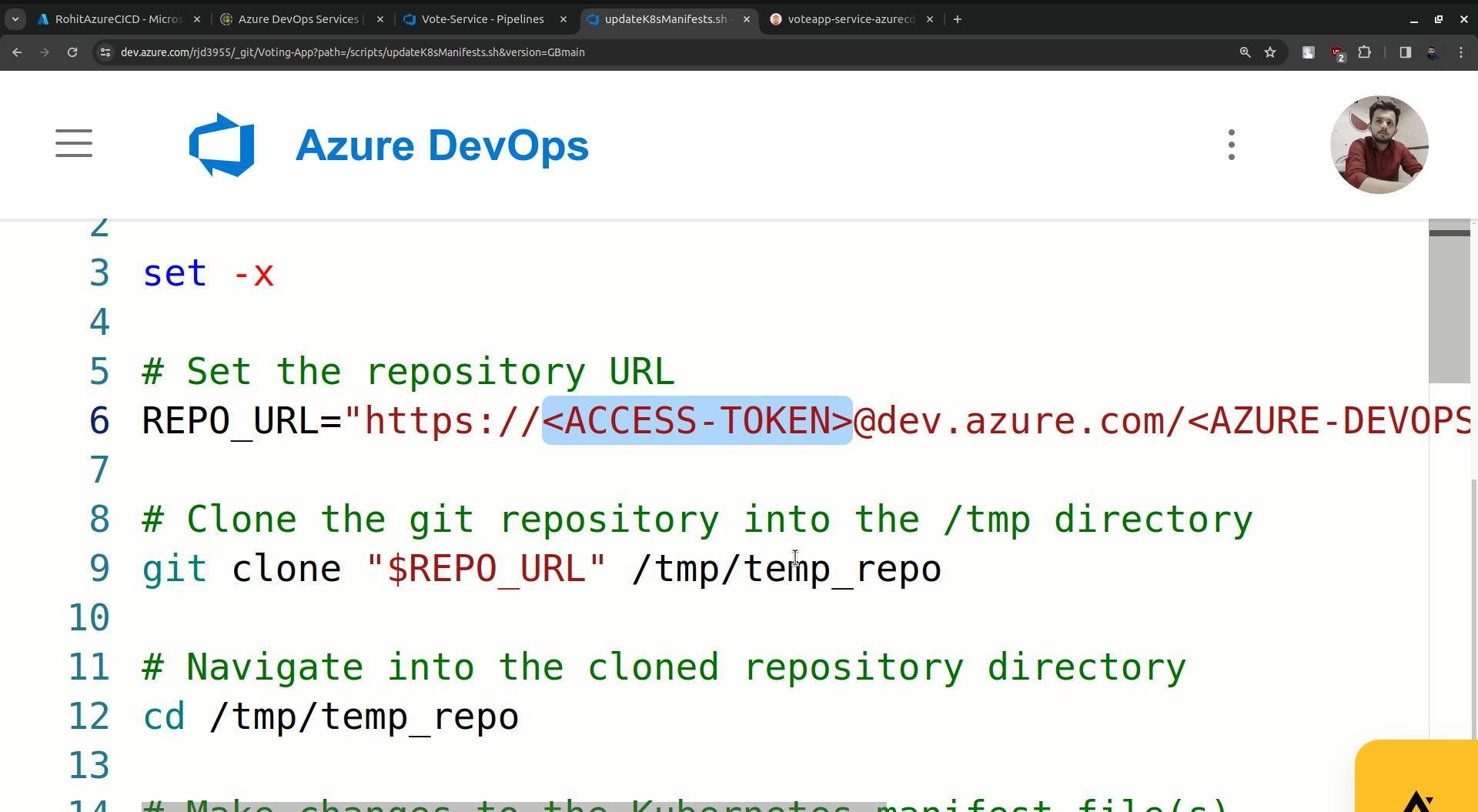
Paste the access token there (the token that we created for argoCD).
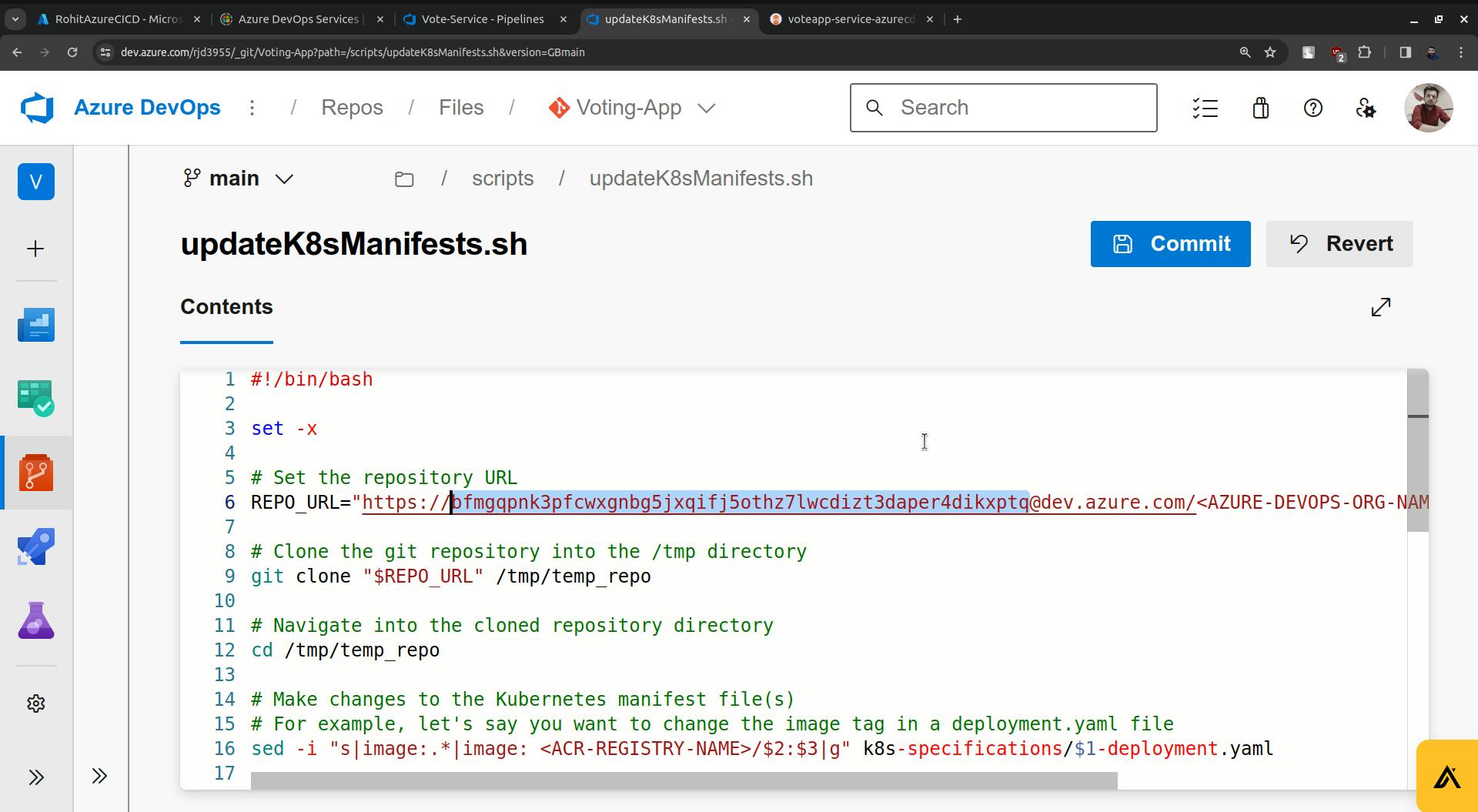
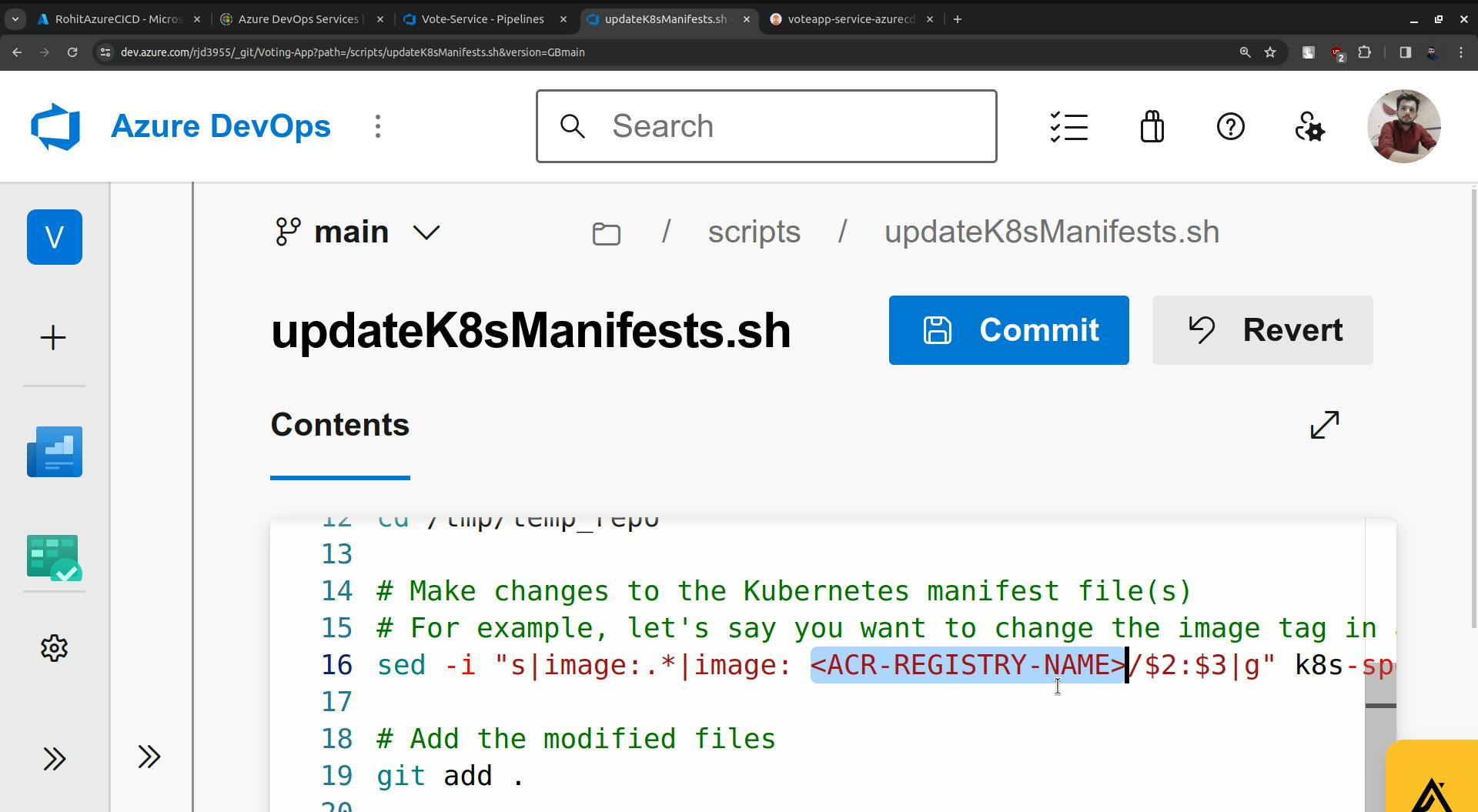
change the ACR name, in my case it is RohitAzureCICD.
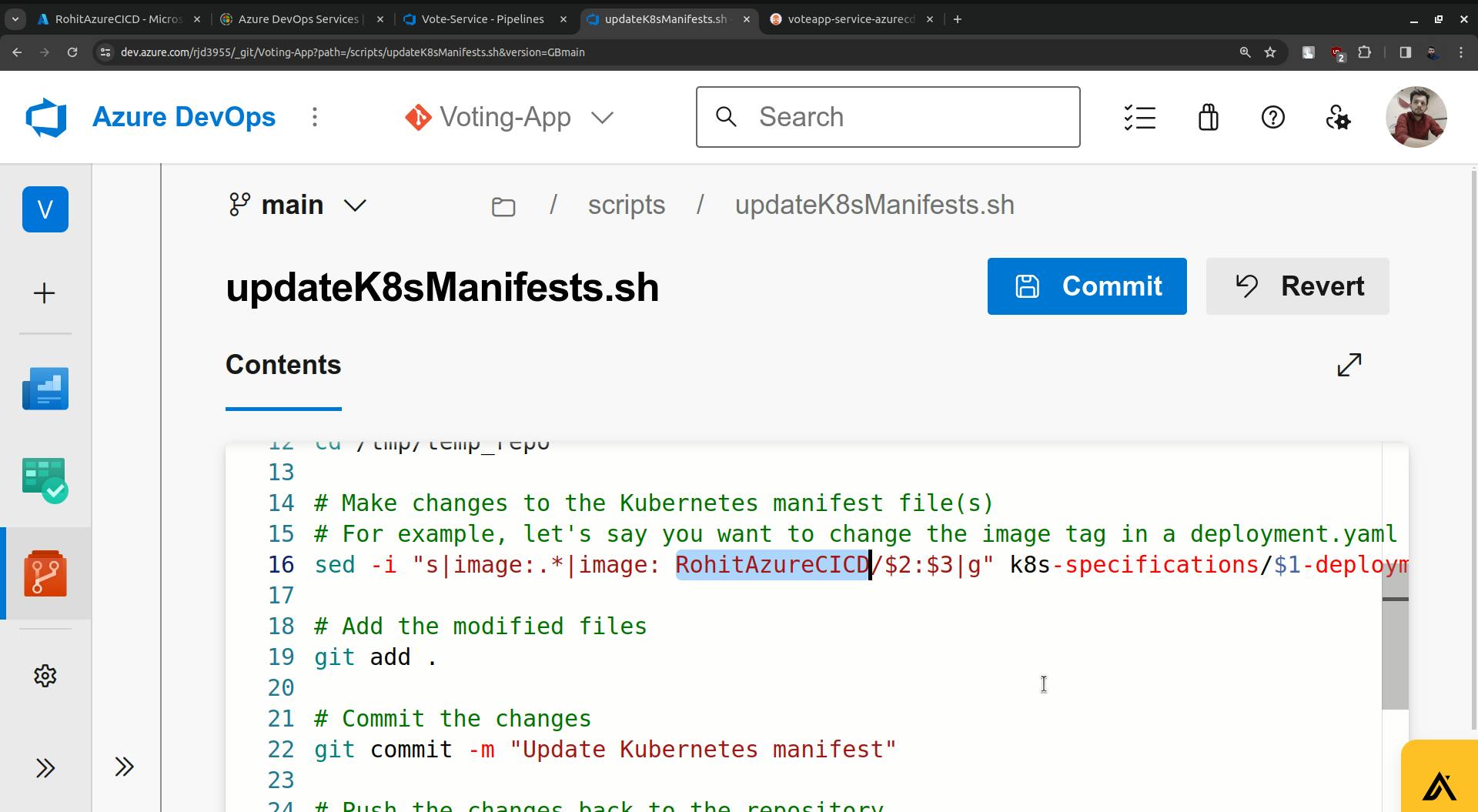
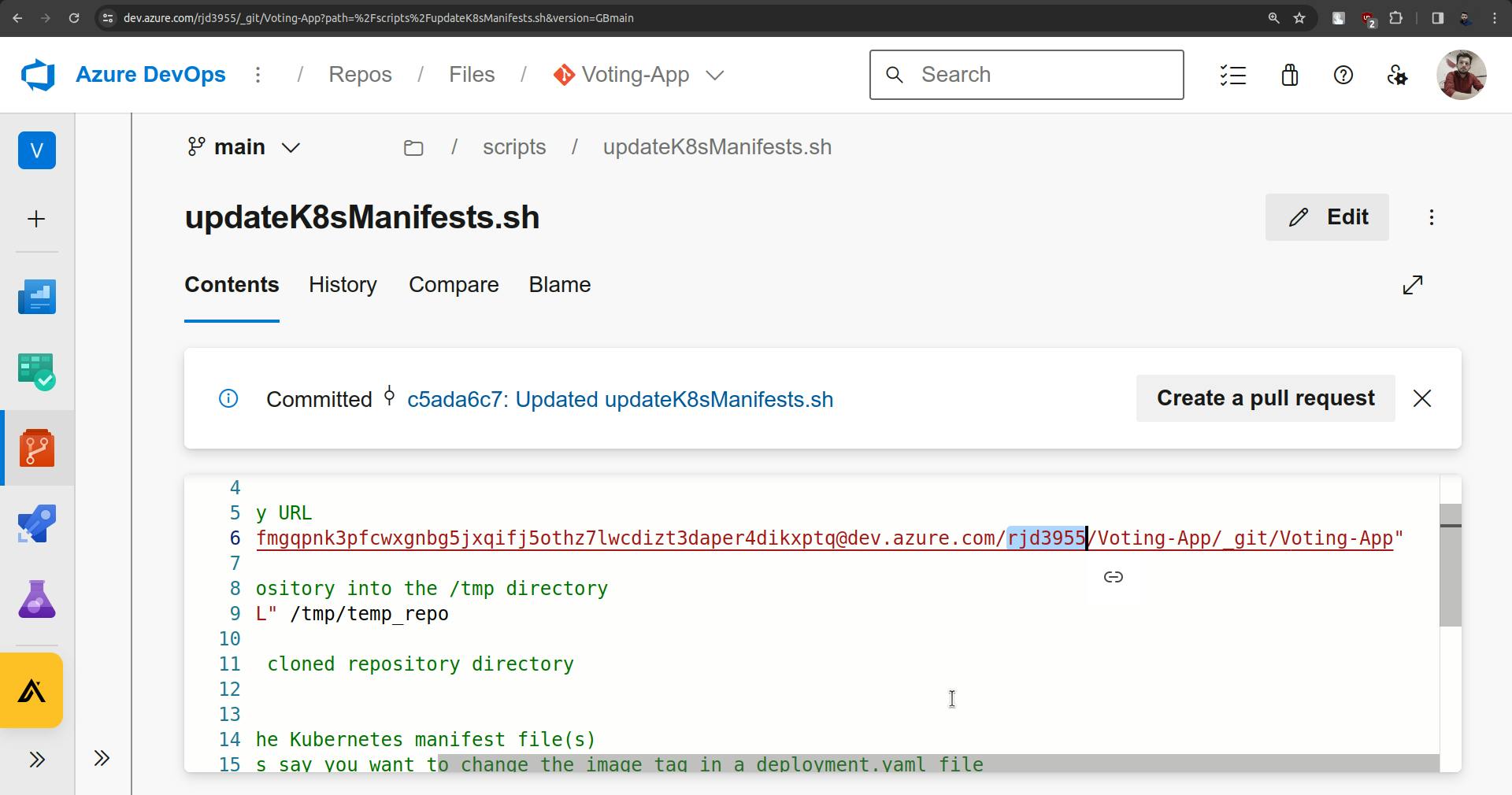
Change <AZURE-DEVOPS-ORG-NAME> this with actual Organization.
Now commit this file.
Go to pipelines and provide the path and other details.
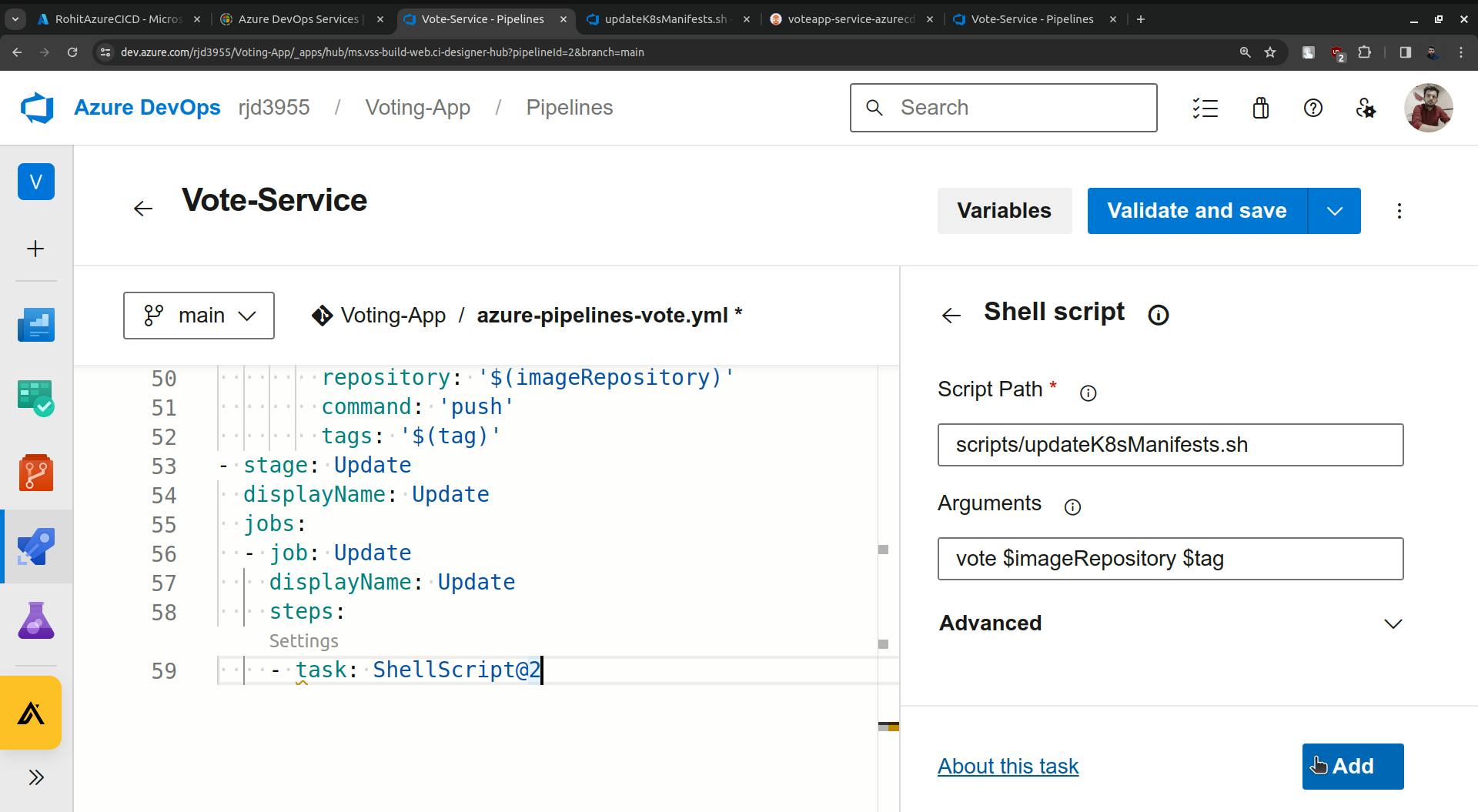
Click on the Add button.
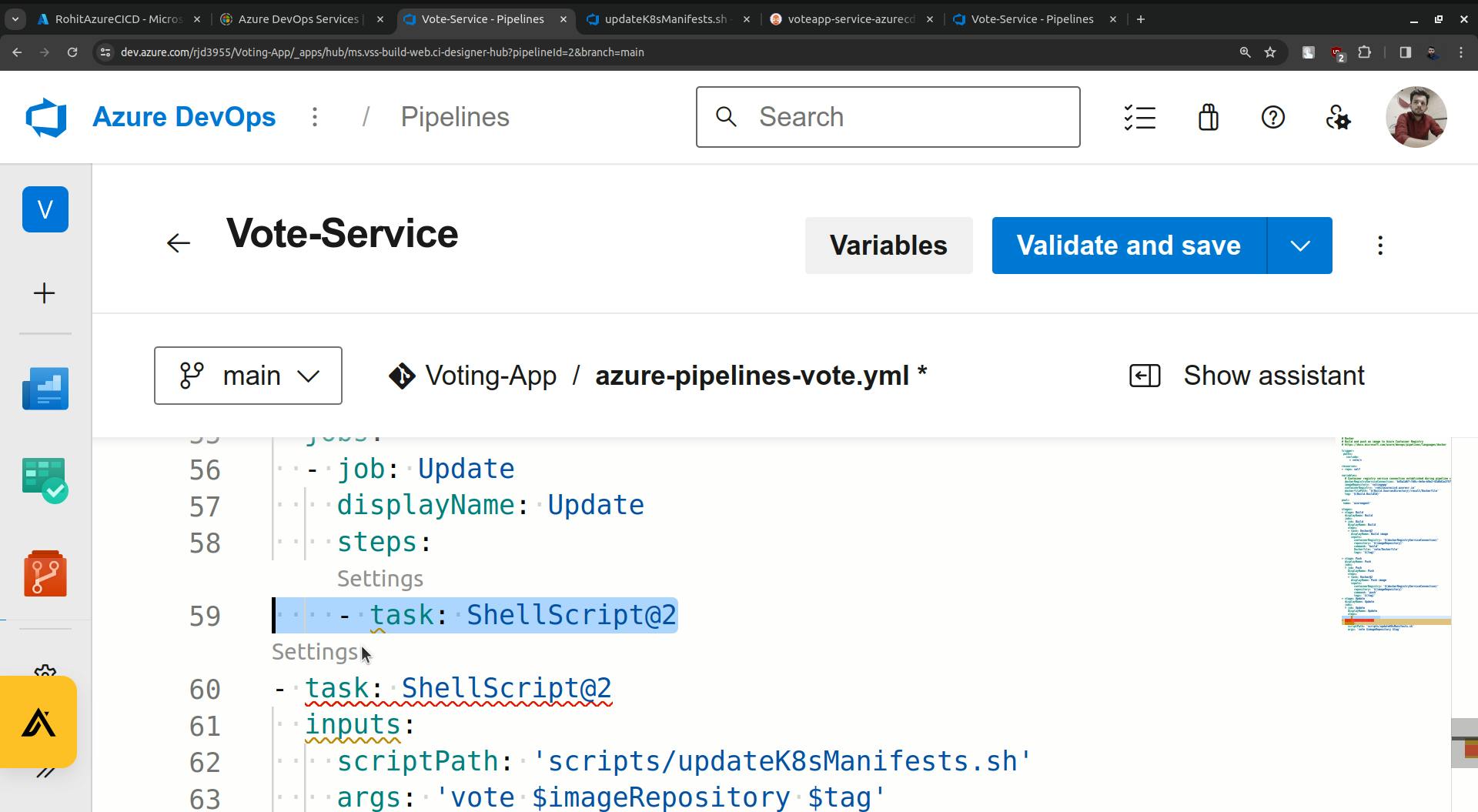
Remove that task line which is highlighted.
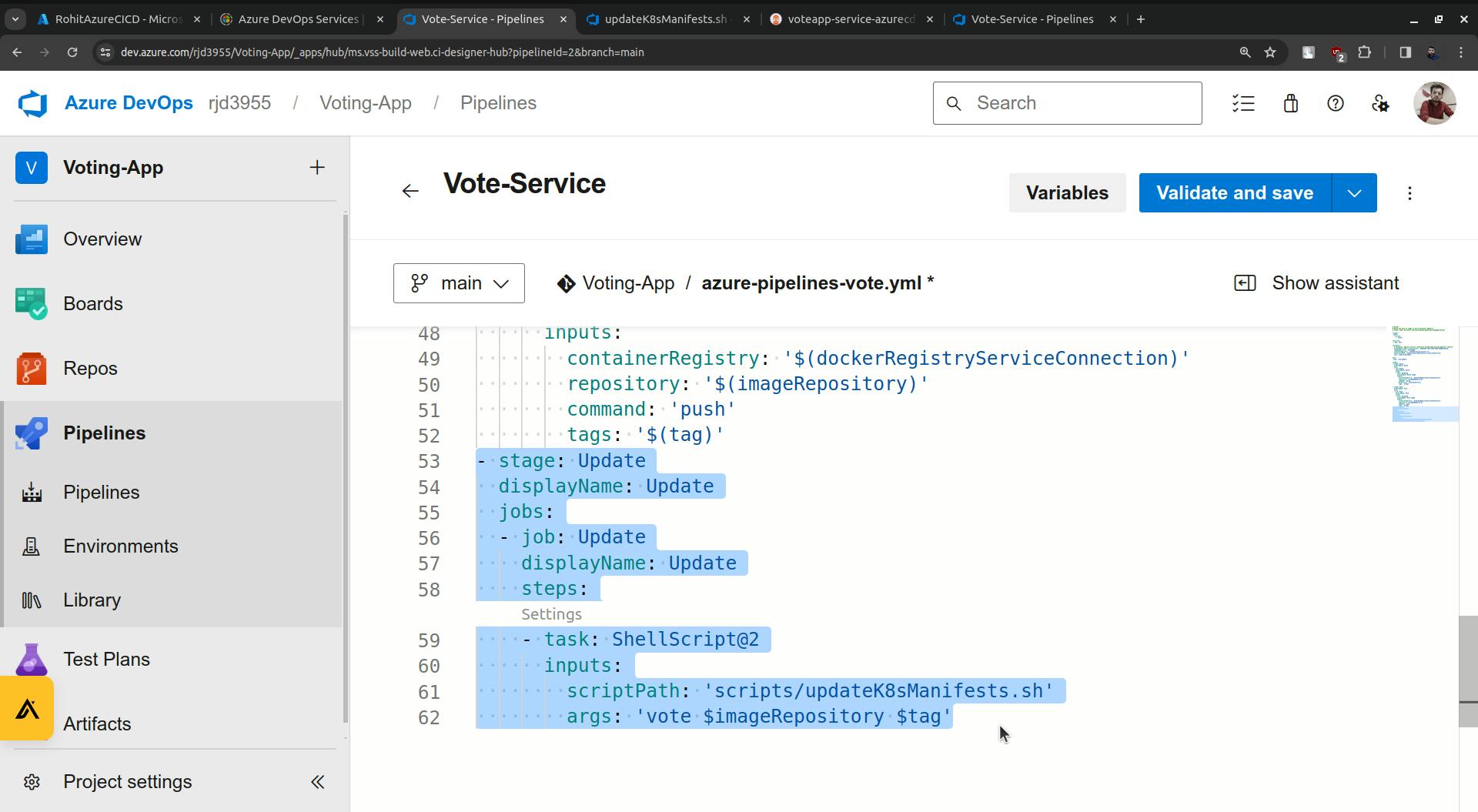
Save this.
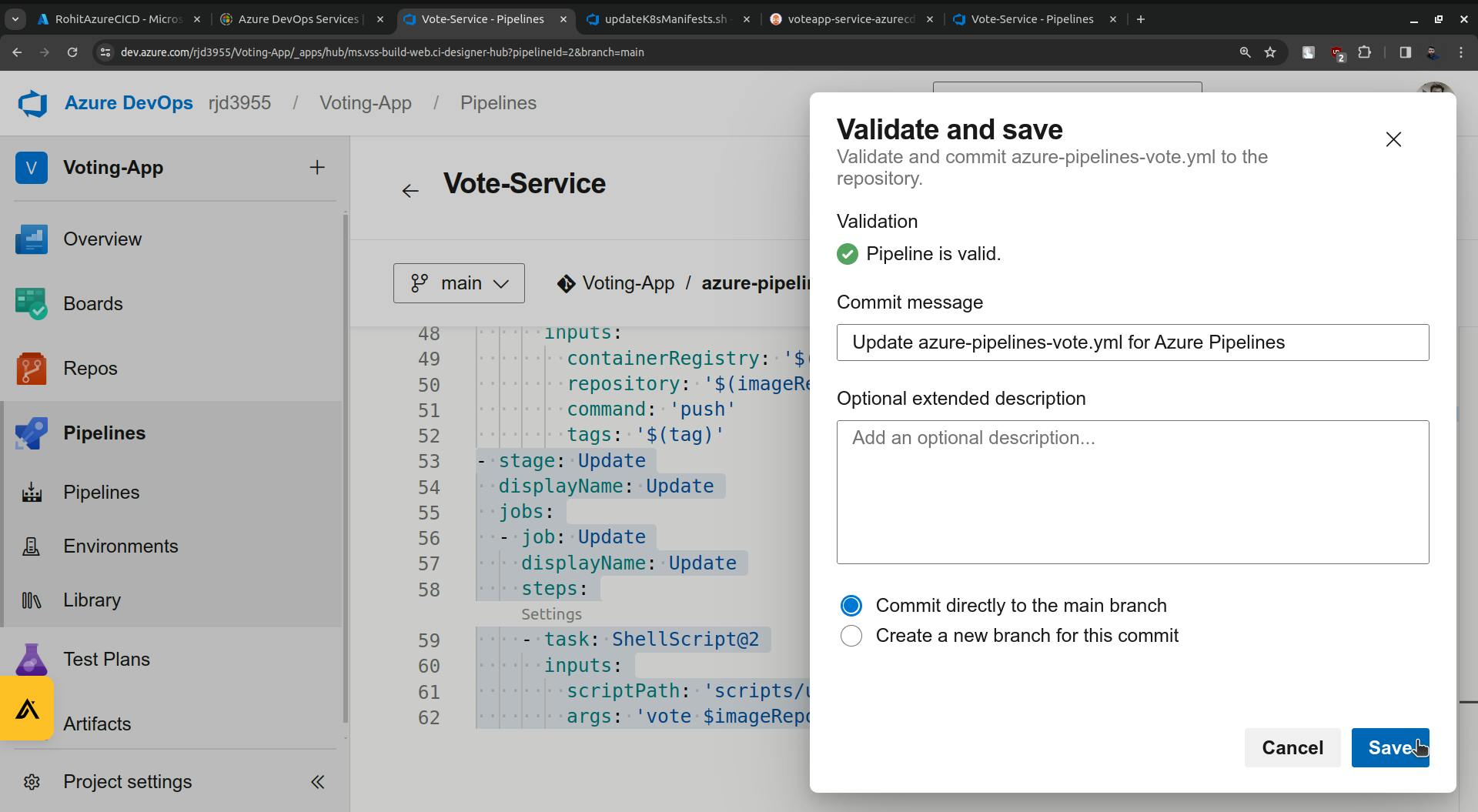
Run it.
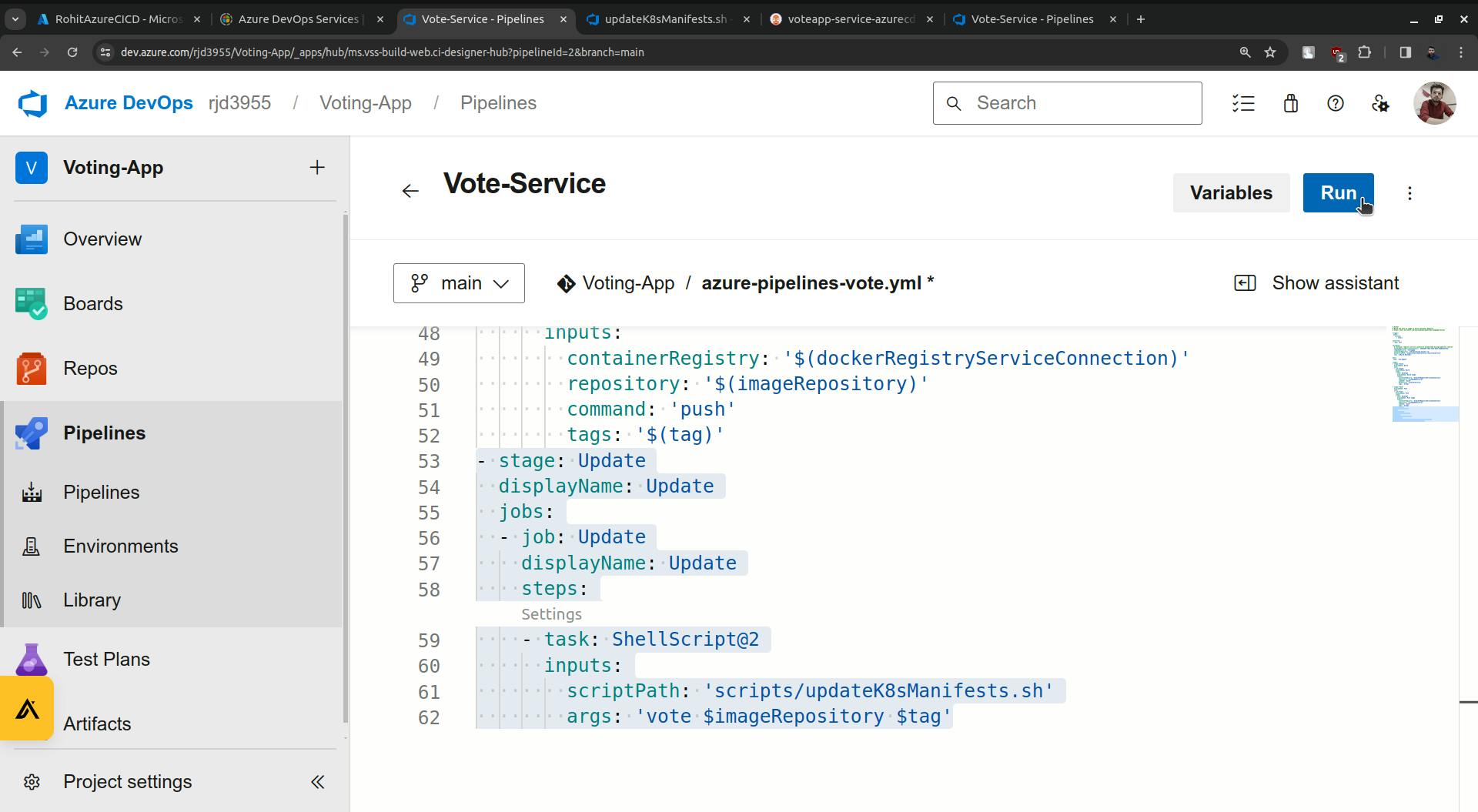
use brackets for the variables.
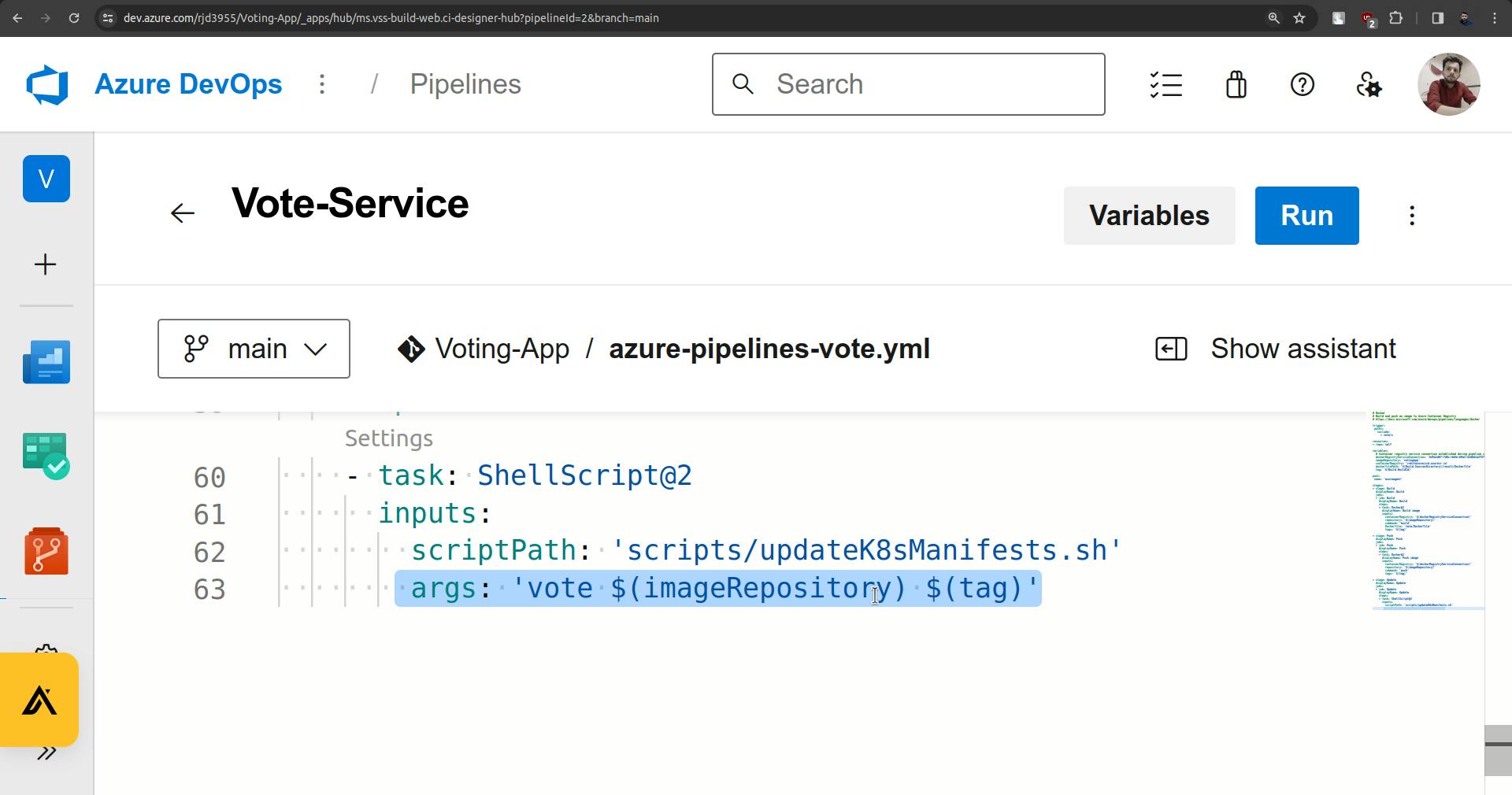
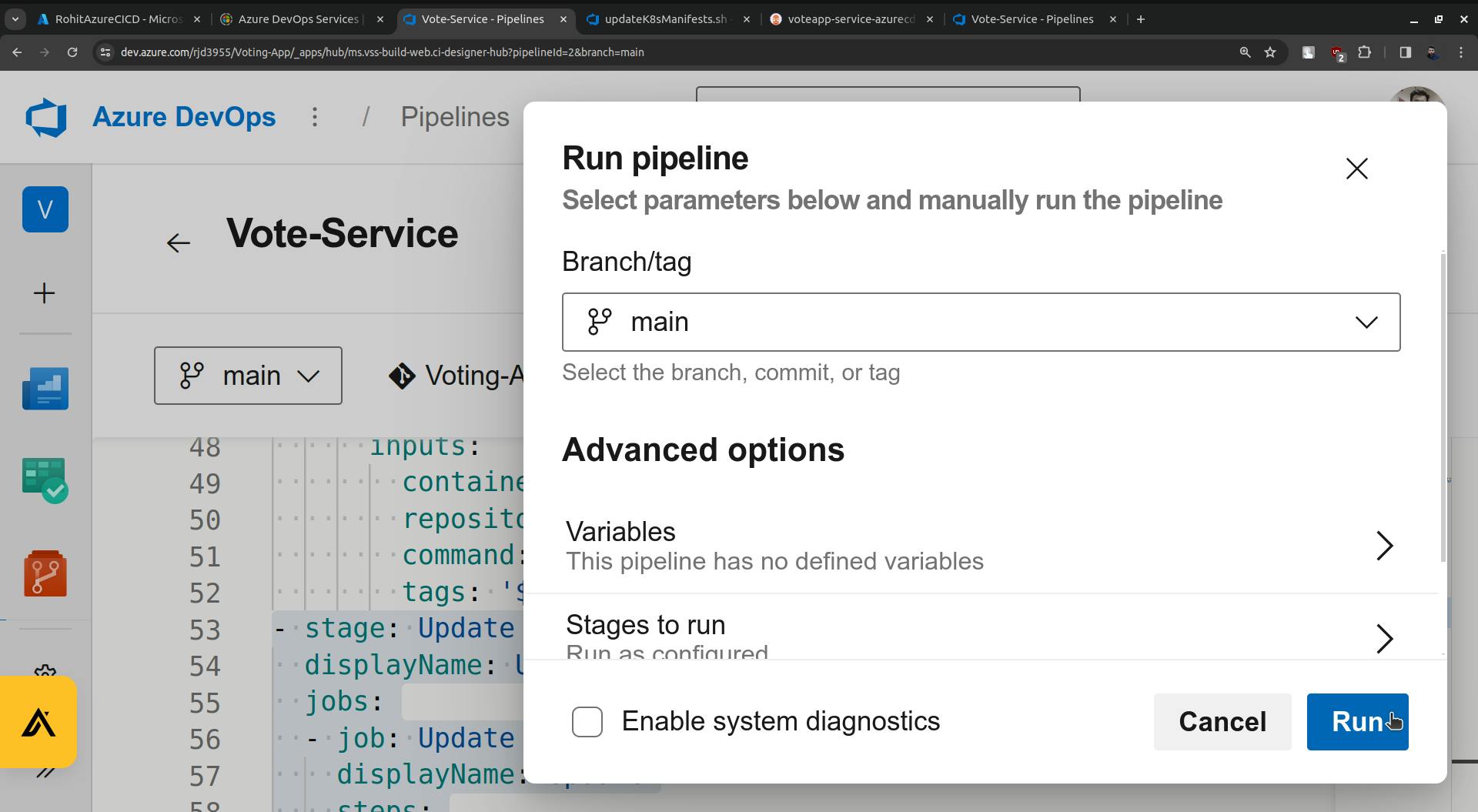
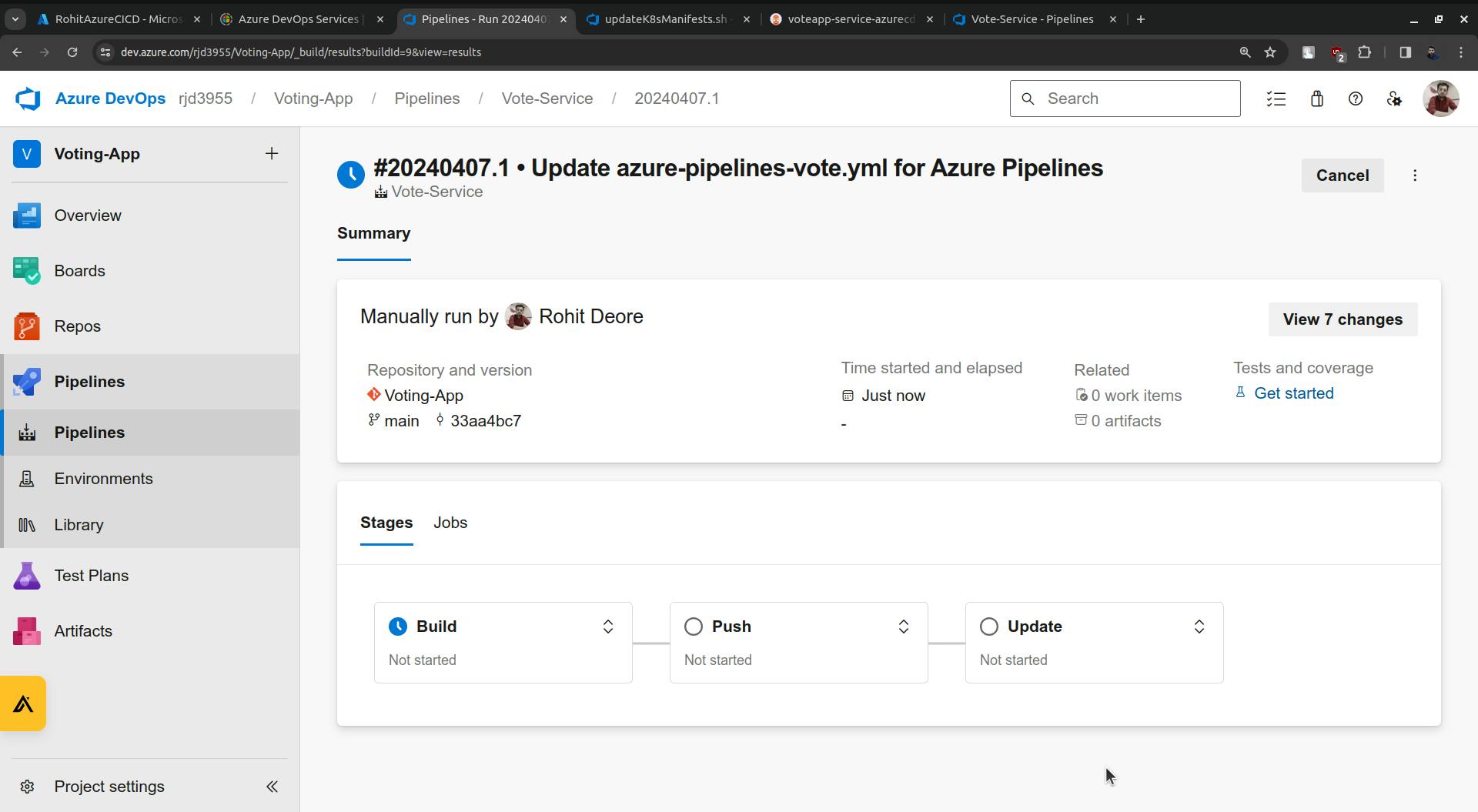
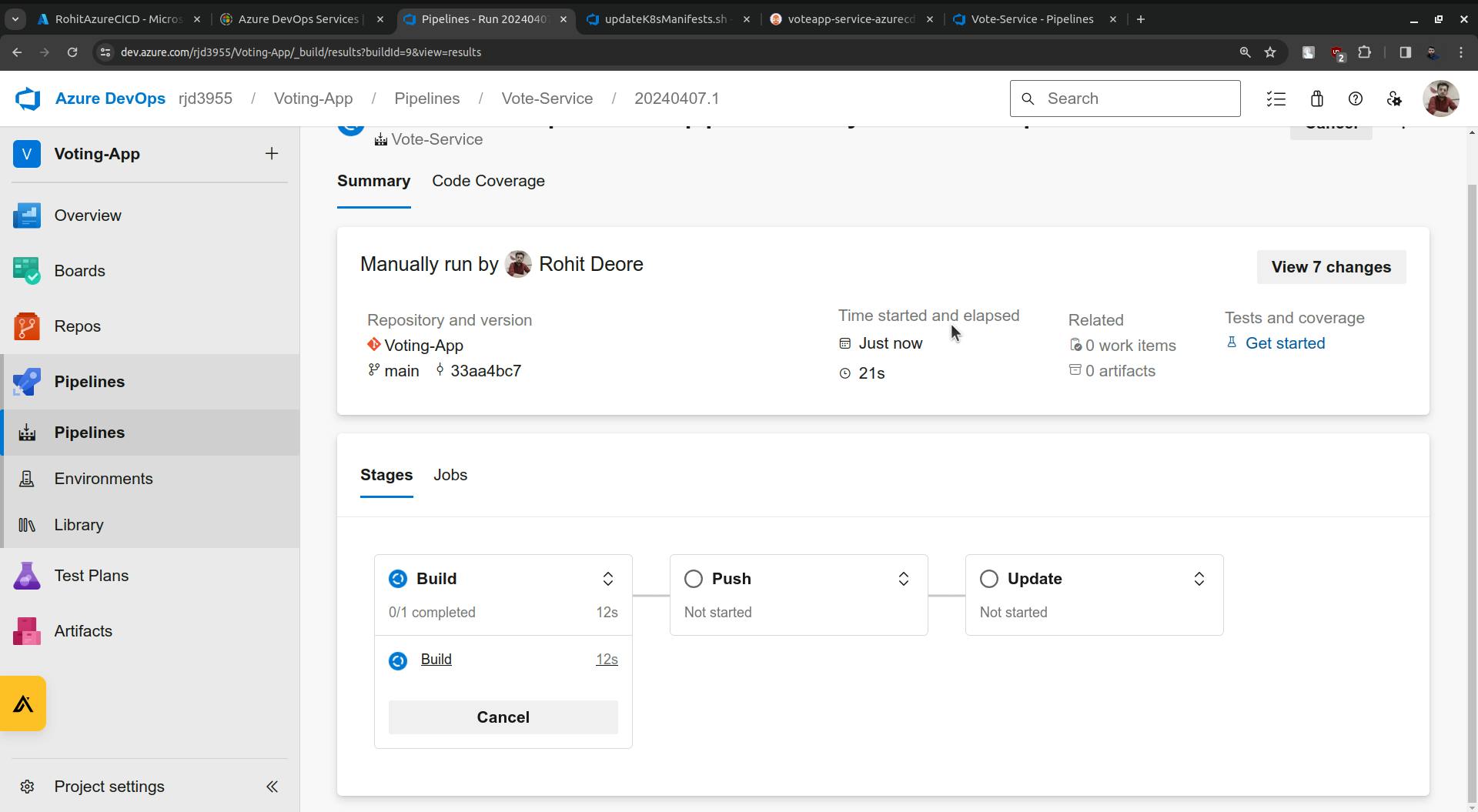
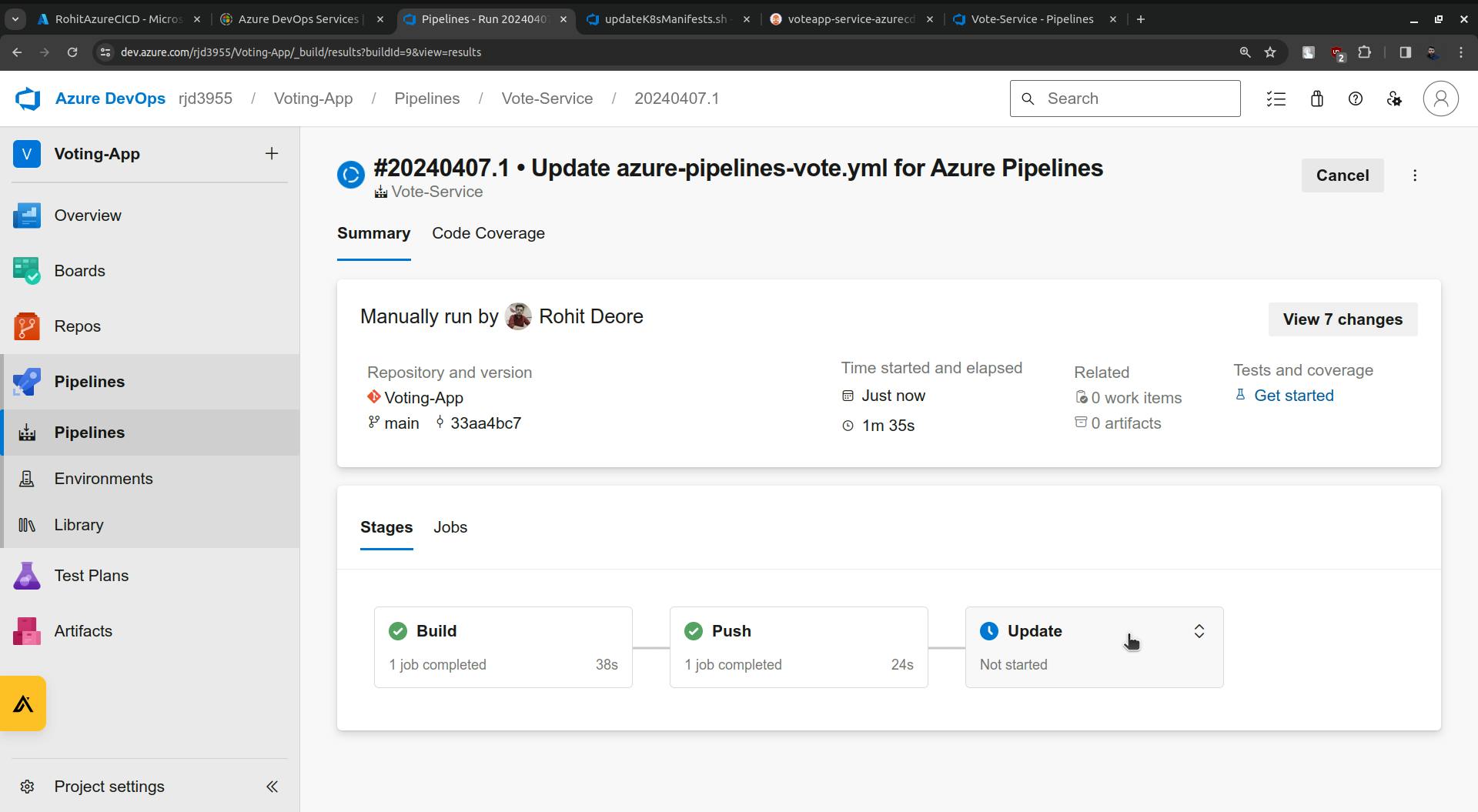
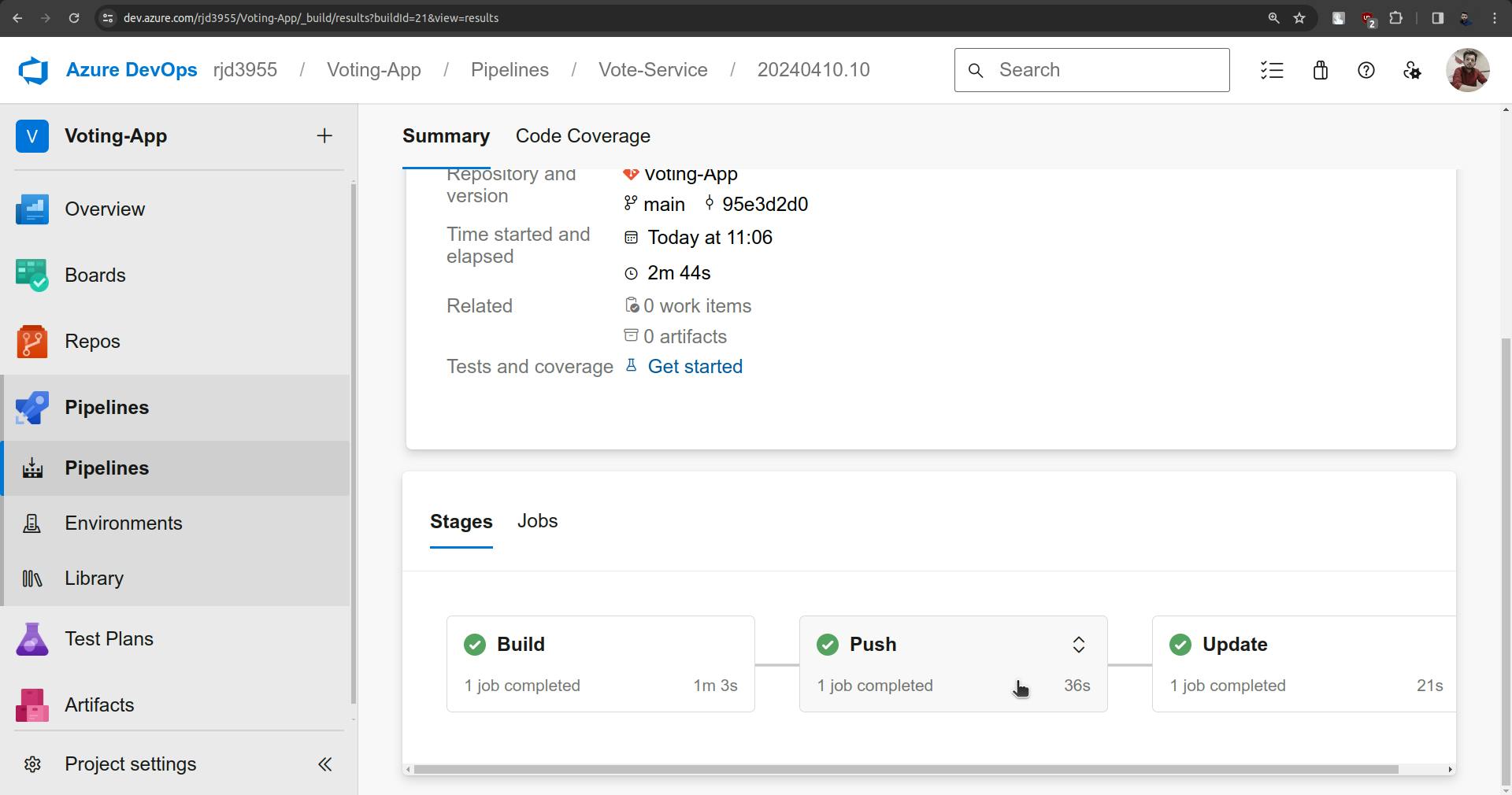
once the Update is done it will update the following highlighted image.
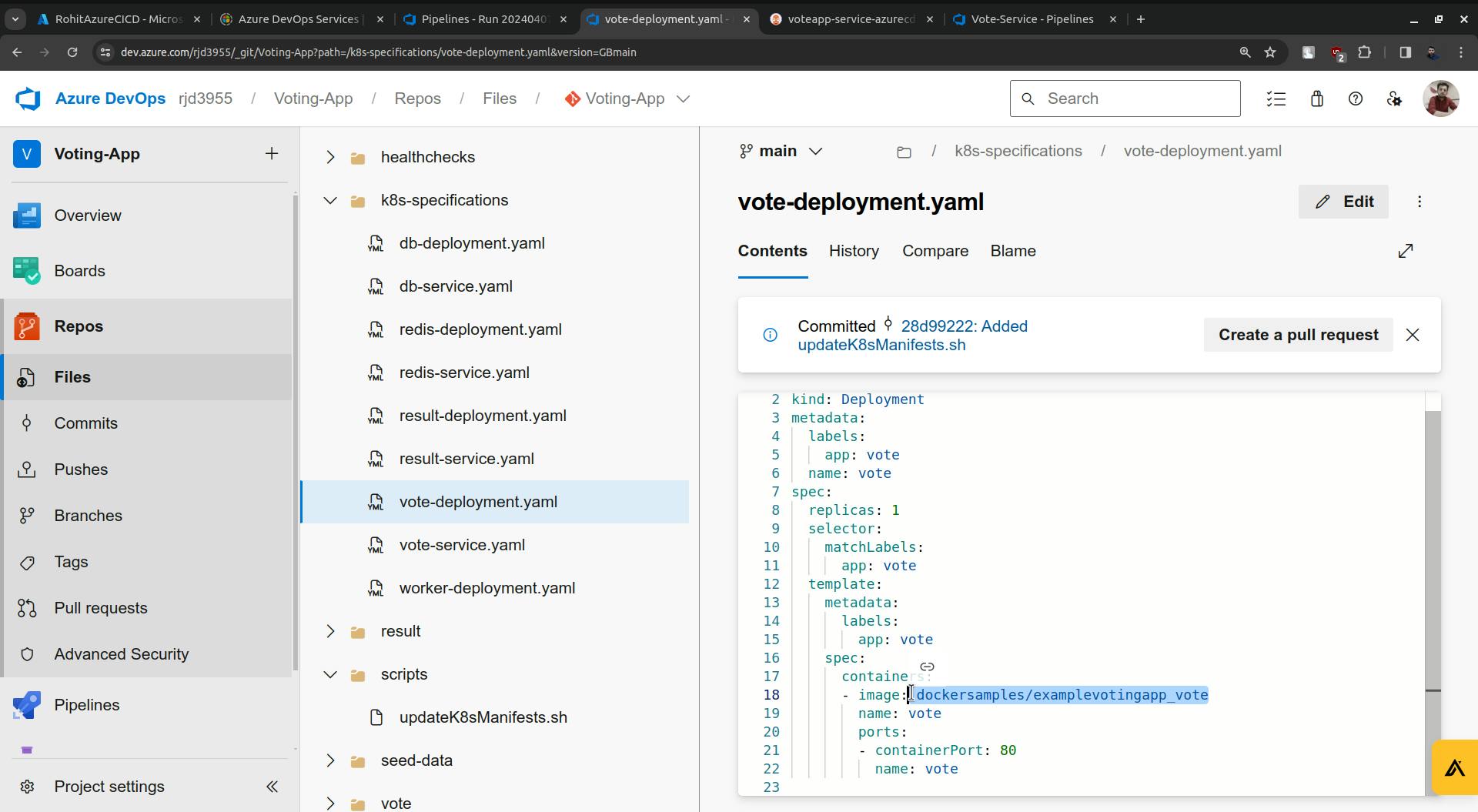
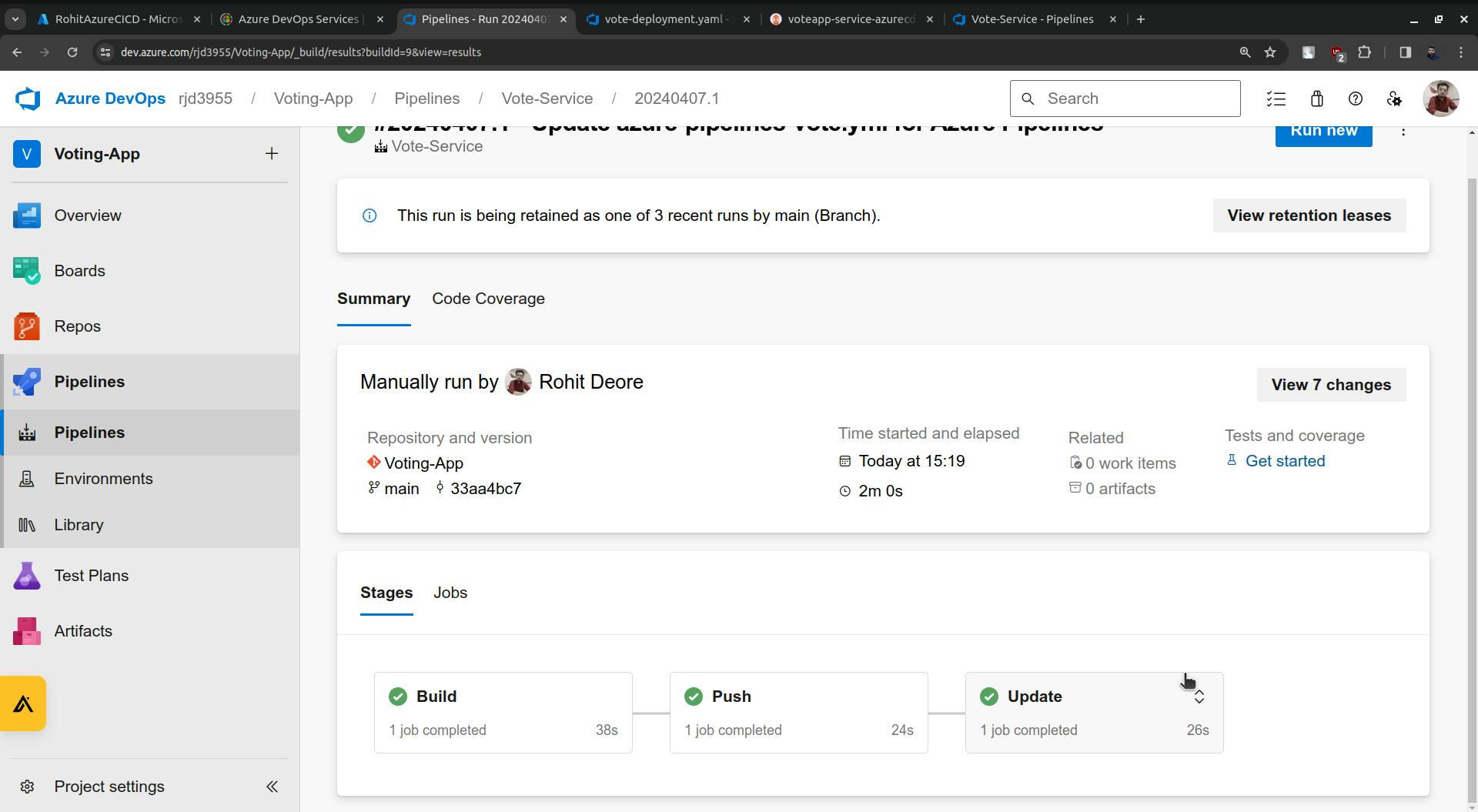
The update stage is completed and you will see the changes in the vote-deployment.yaml file.
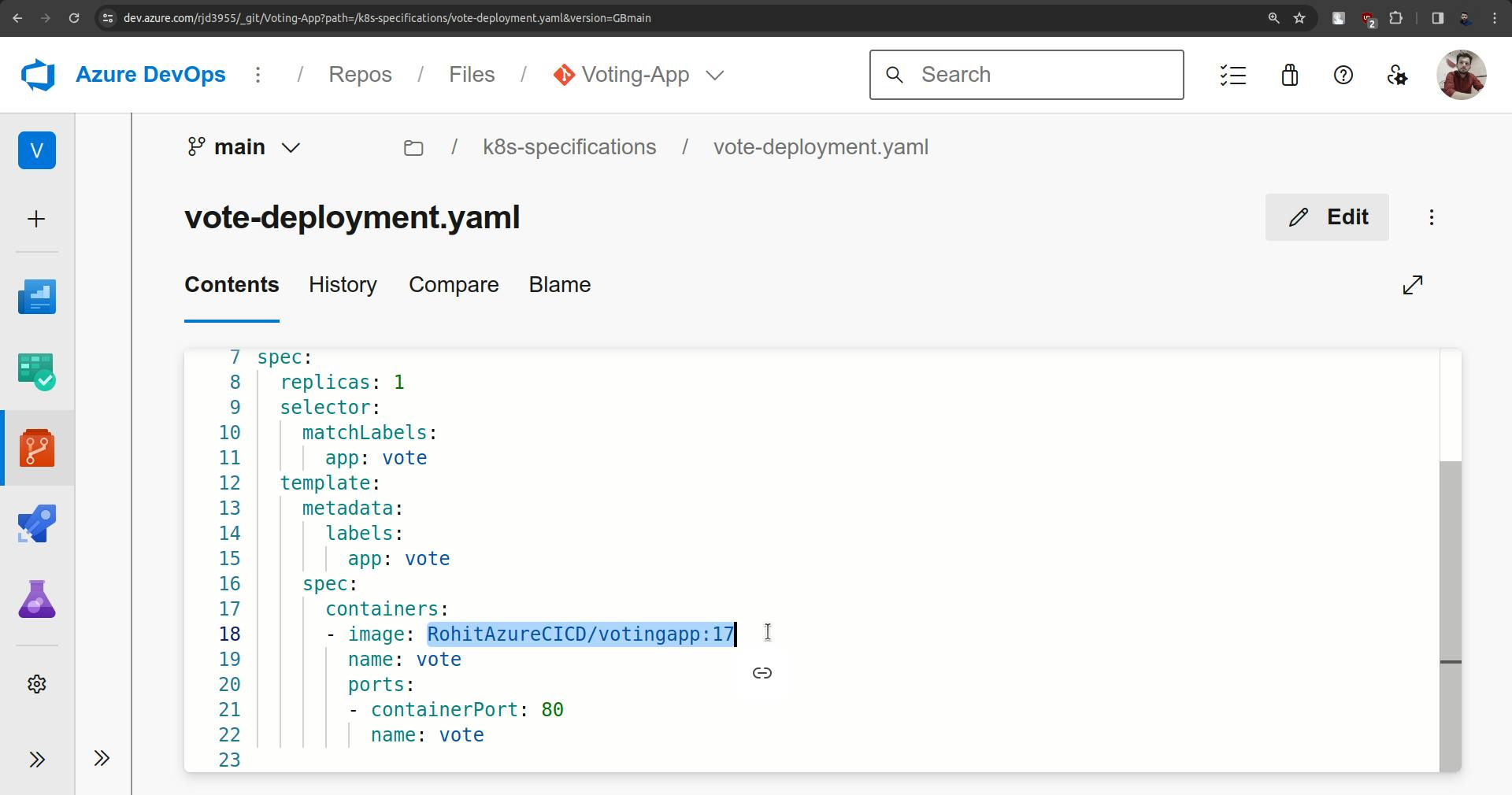
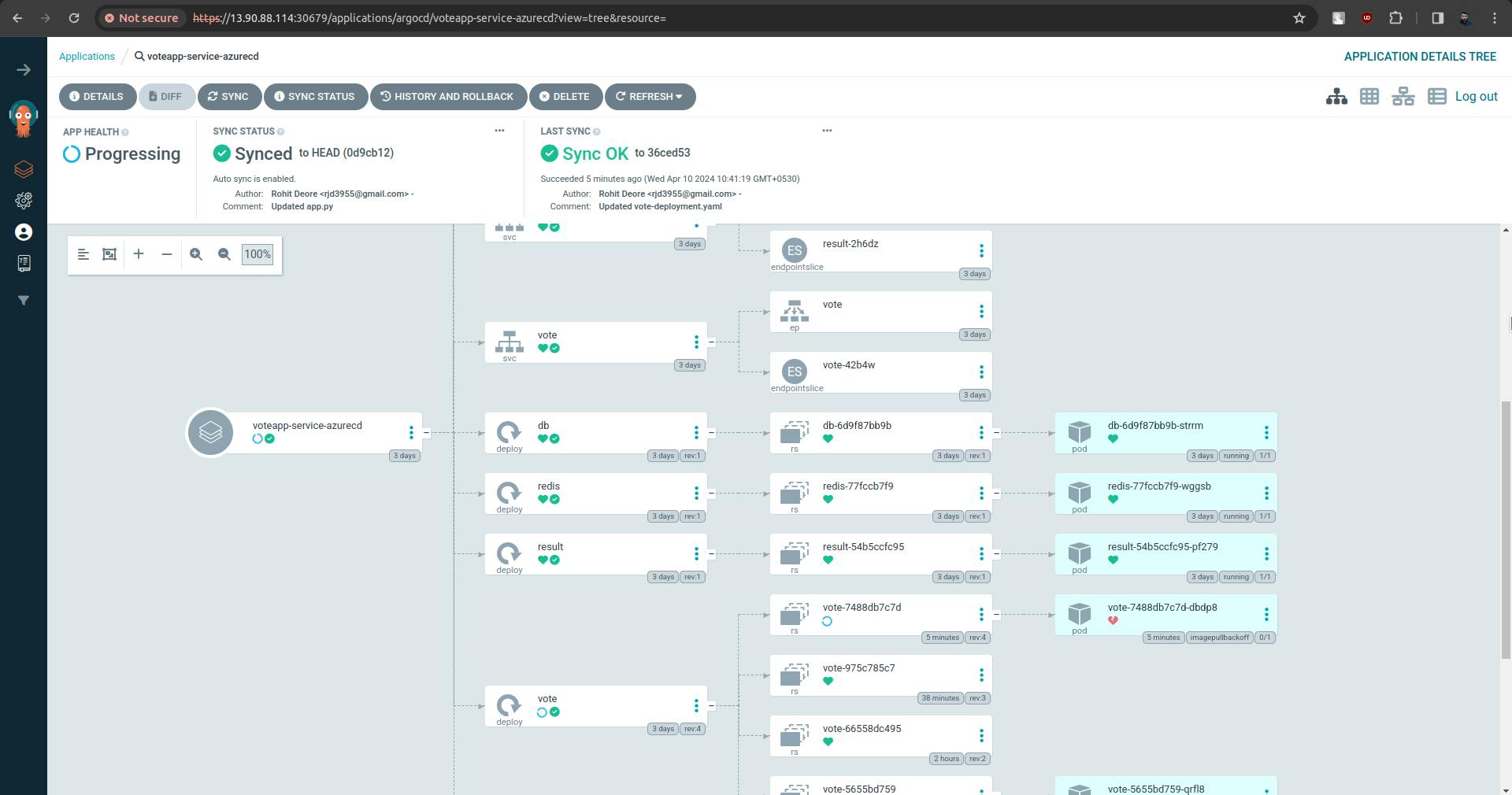
ArgoCD is watching for this repository once there are changes are found it will update the cluster. Here it will take three minutes to check the updates or changes in the repo.
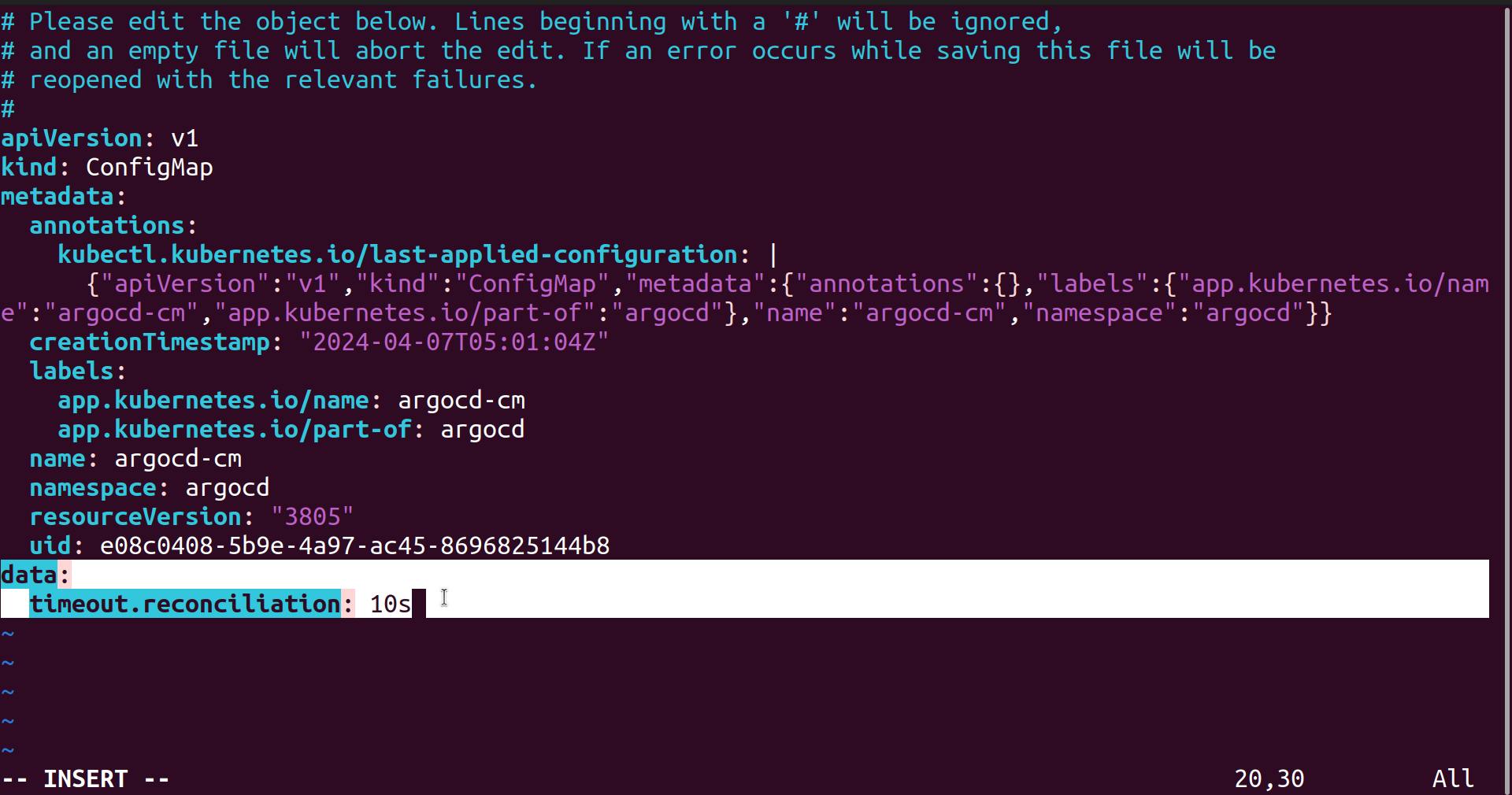
So by default sync time is 3 minutes, but we can change it from 3 minutes to 10 seconds.
kubectl edit cm argocd-cm -n argocd
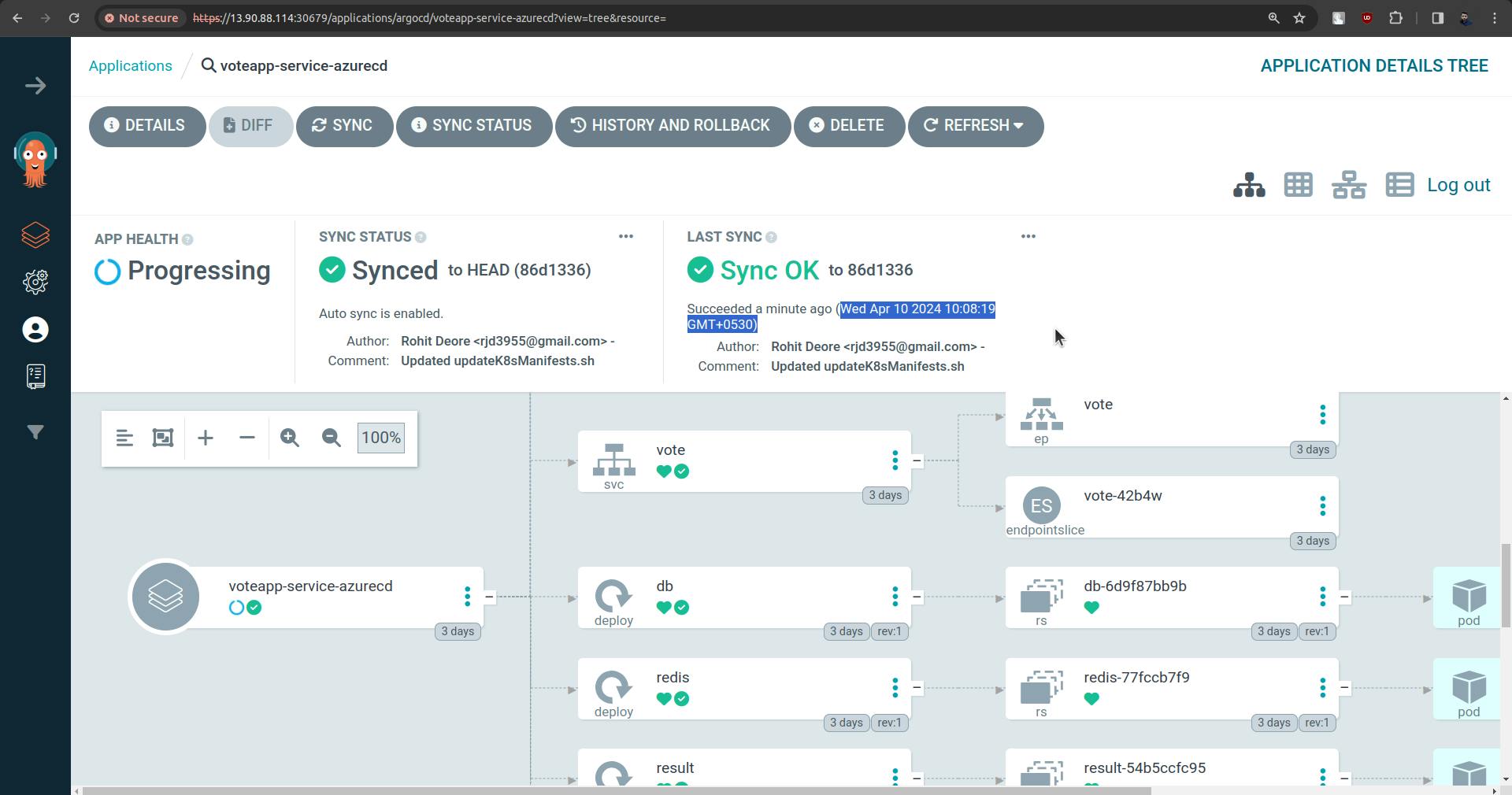
Changes just have been done 8 min ago.
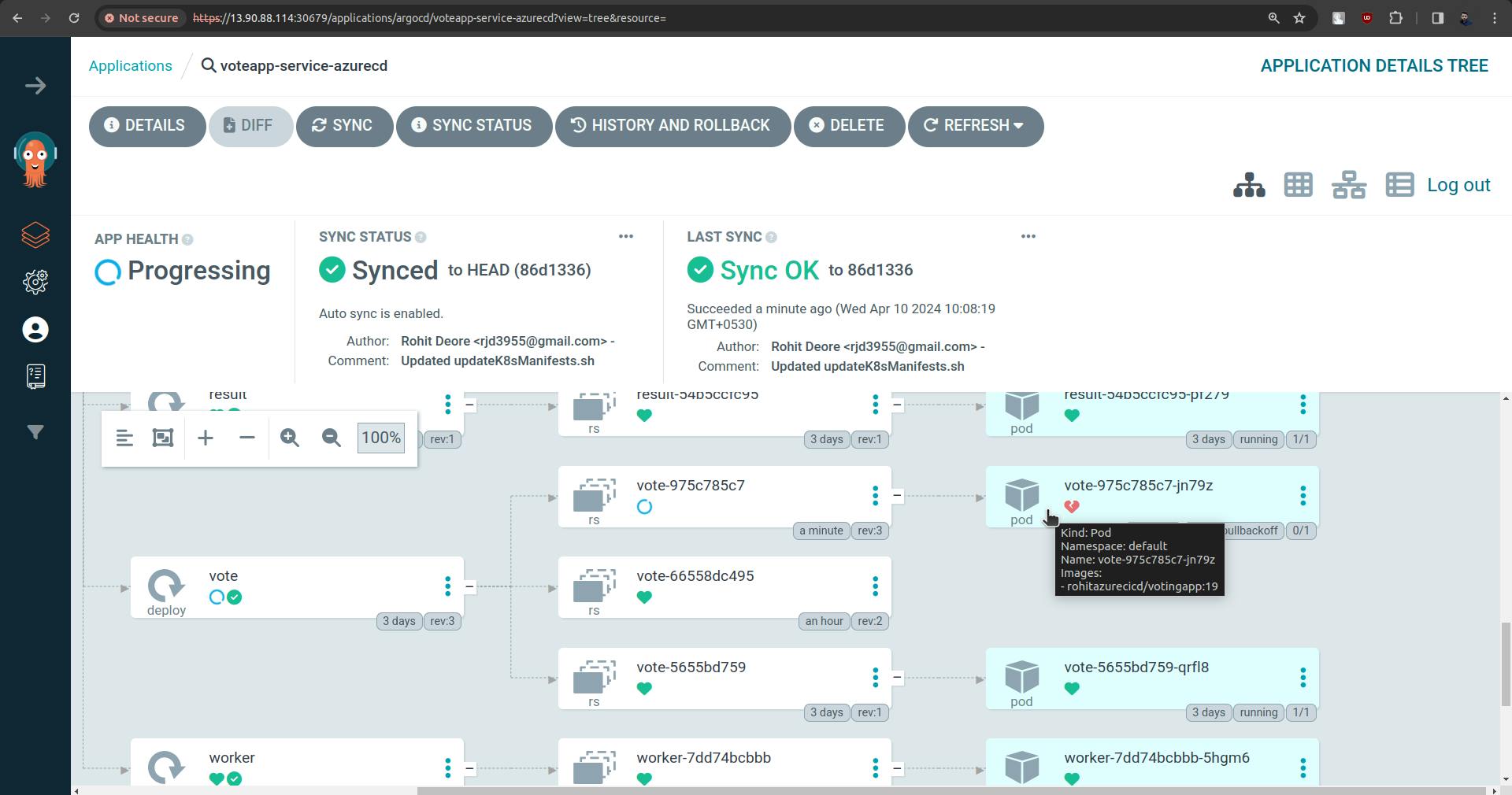
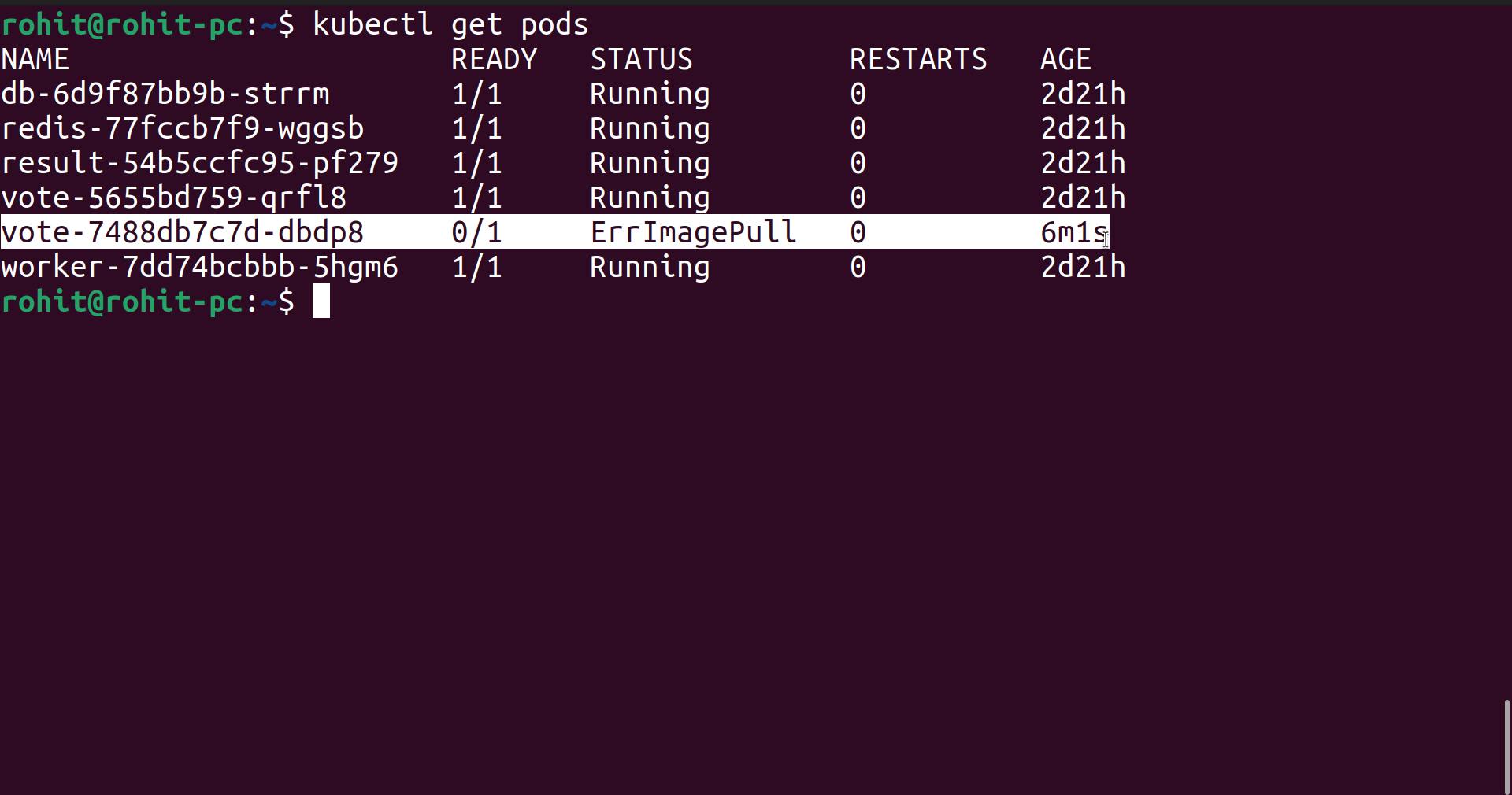
But in the above screenshot, you can see that the pod is not up.
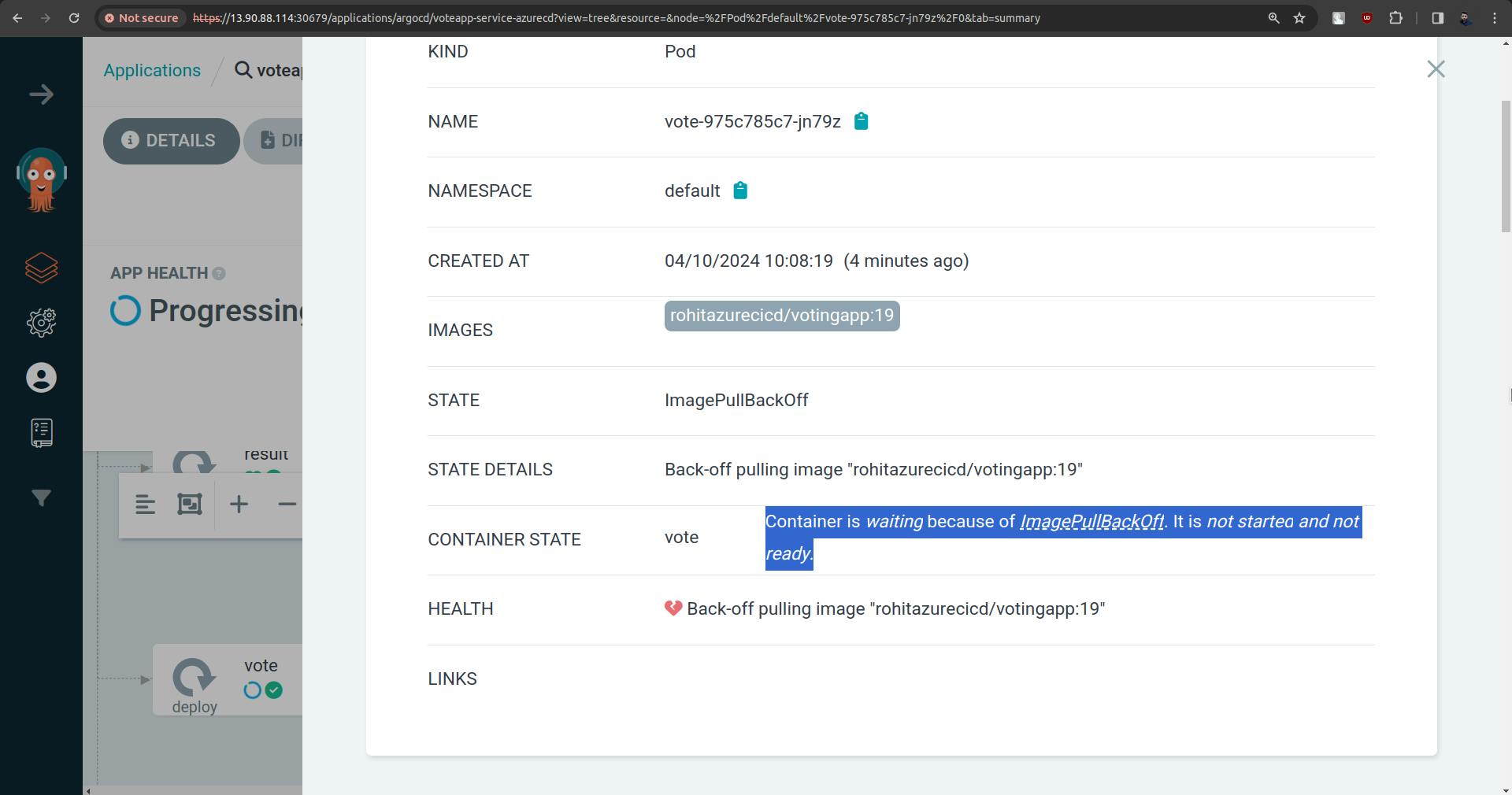
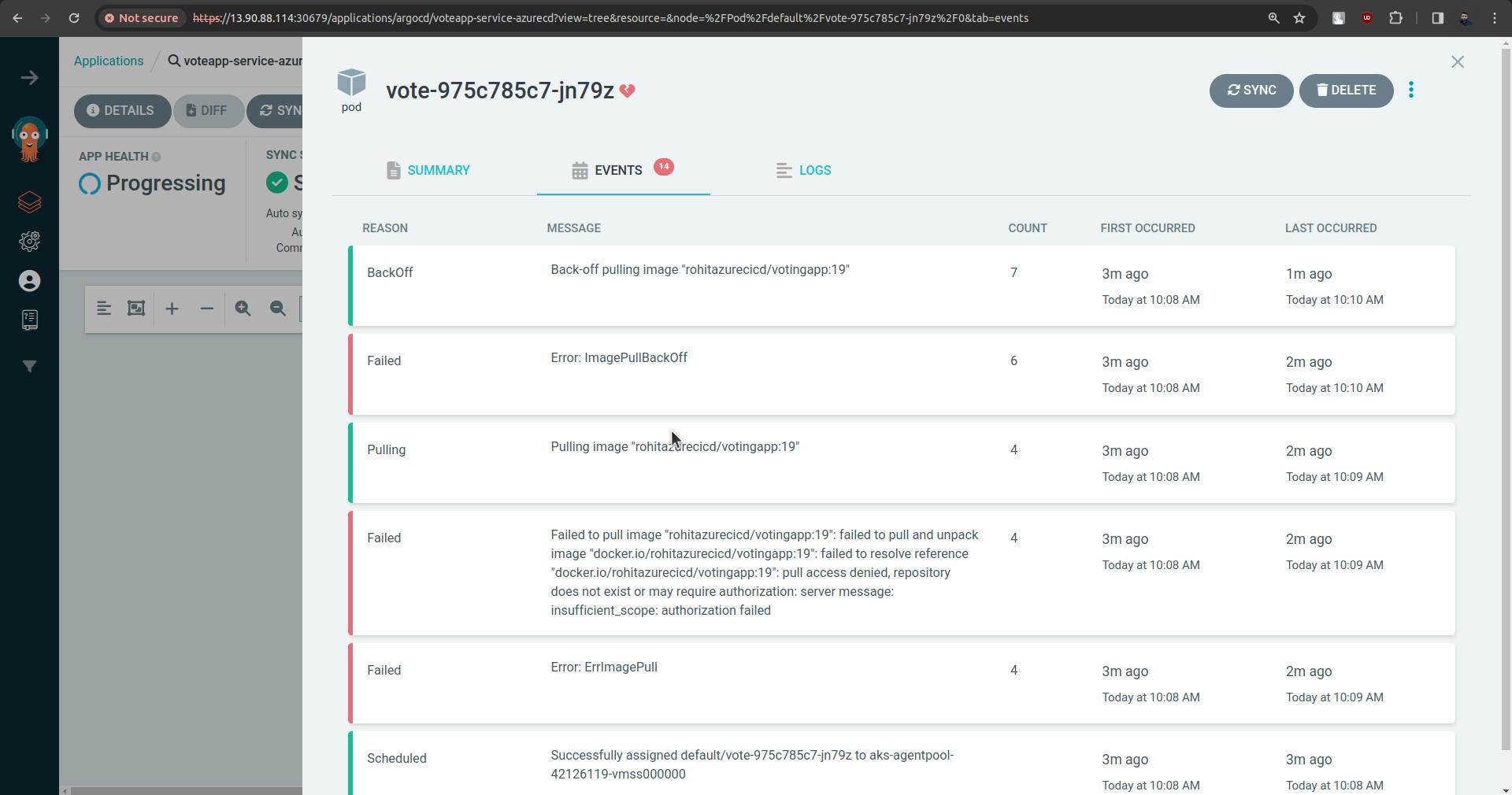
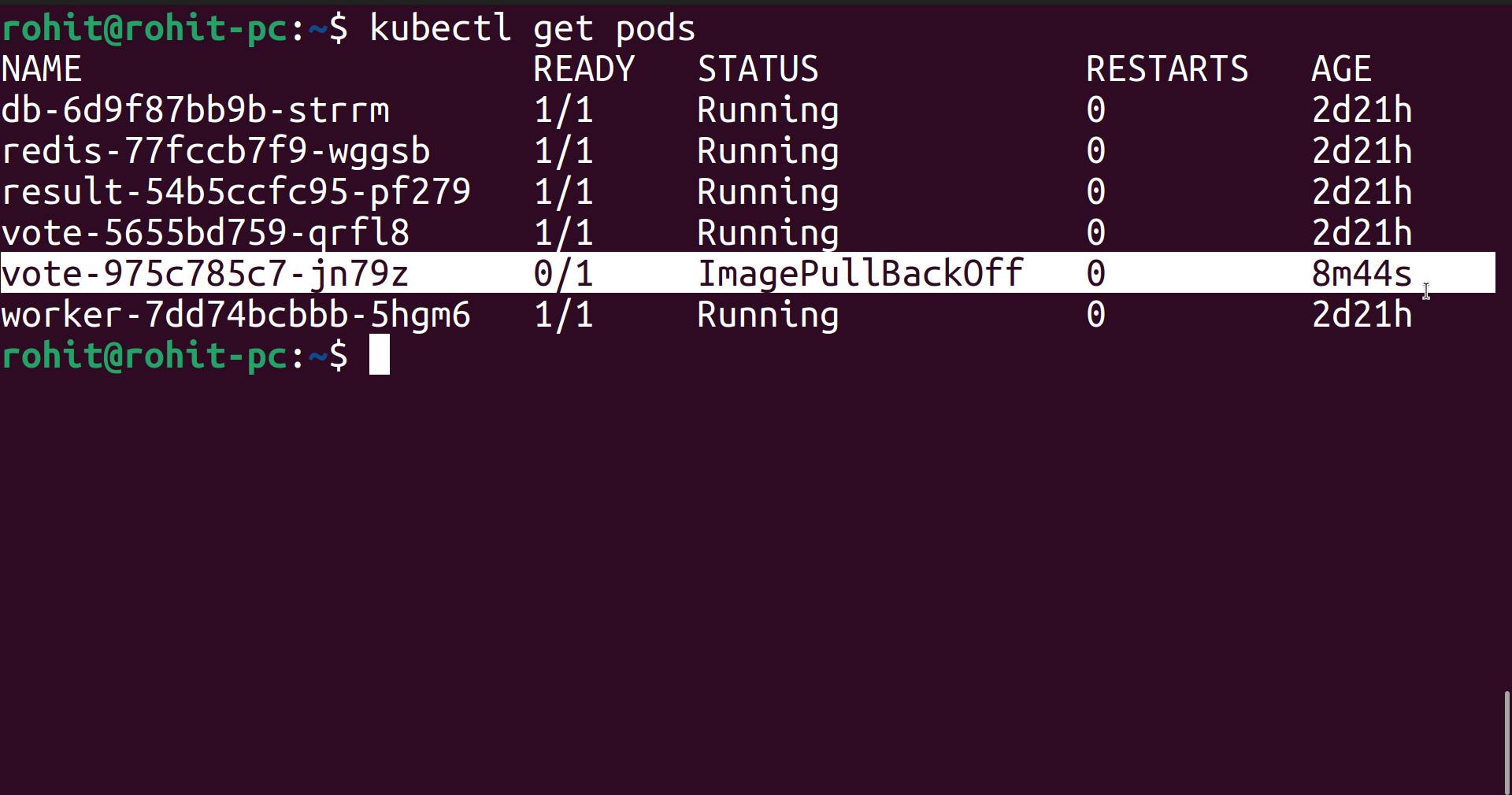
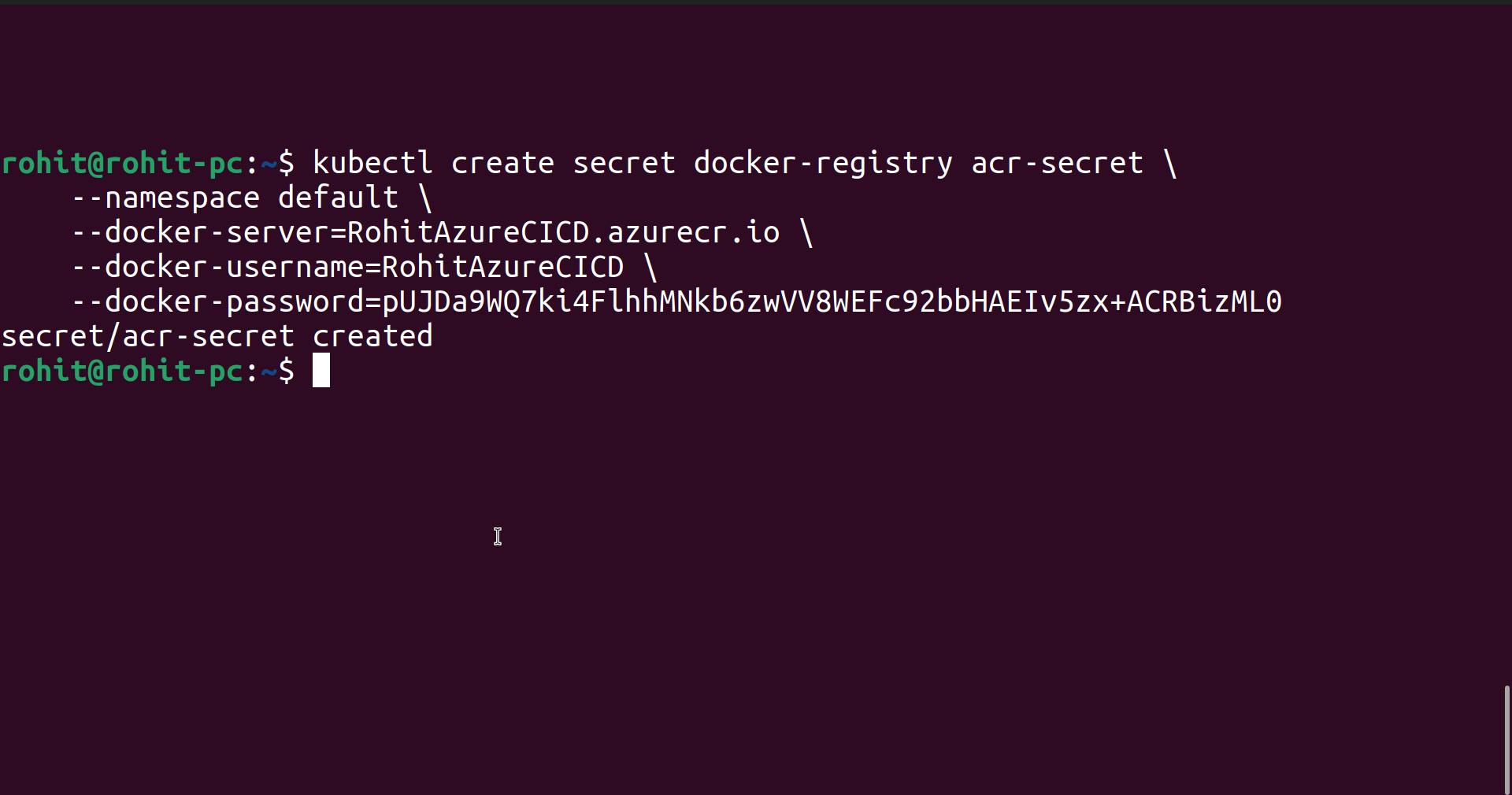
This is because we are pulling images from private registry, now how will Kubernetes understand what is username and password.
To solve this we need to use the concept called " ImagePullSecrets "
Go to Container registries.
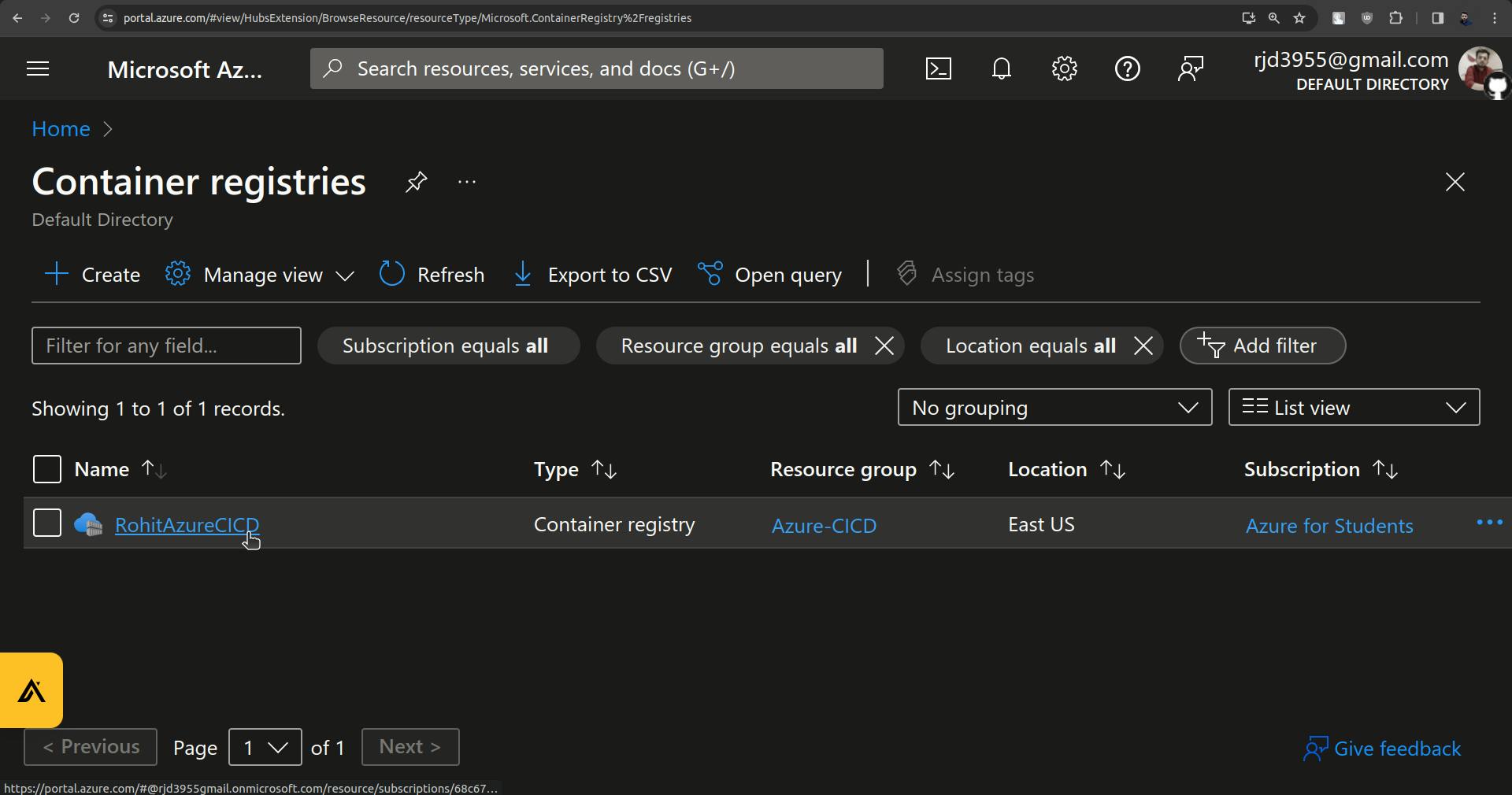
Click on Access keys.
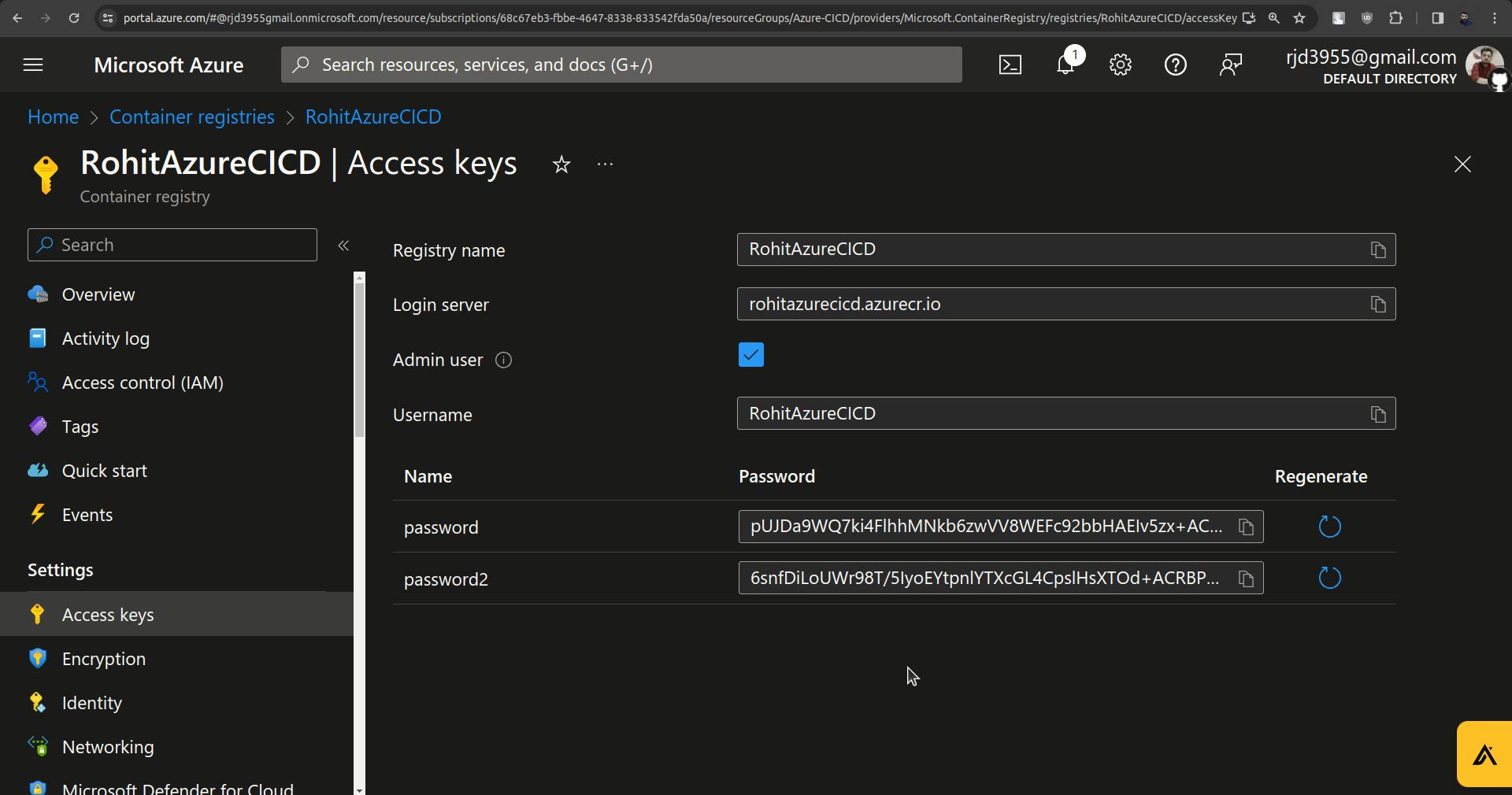
Go to the terminal and use the command.
command:
kubectl create secret docker-registry <secret-name> \
--namespace <namespace> \
--docker-server=<container-registry-name>.azurecr.io \
--docker-username=<service-principal-ID> \
--docker-password=<service-principal-password>
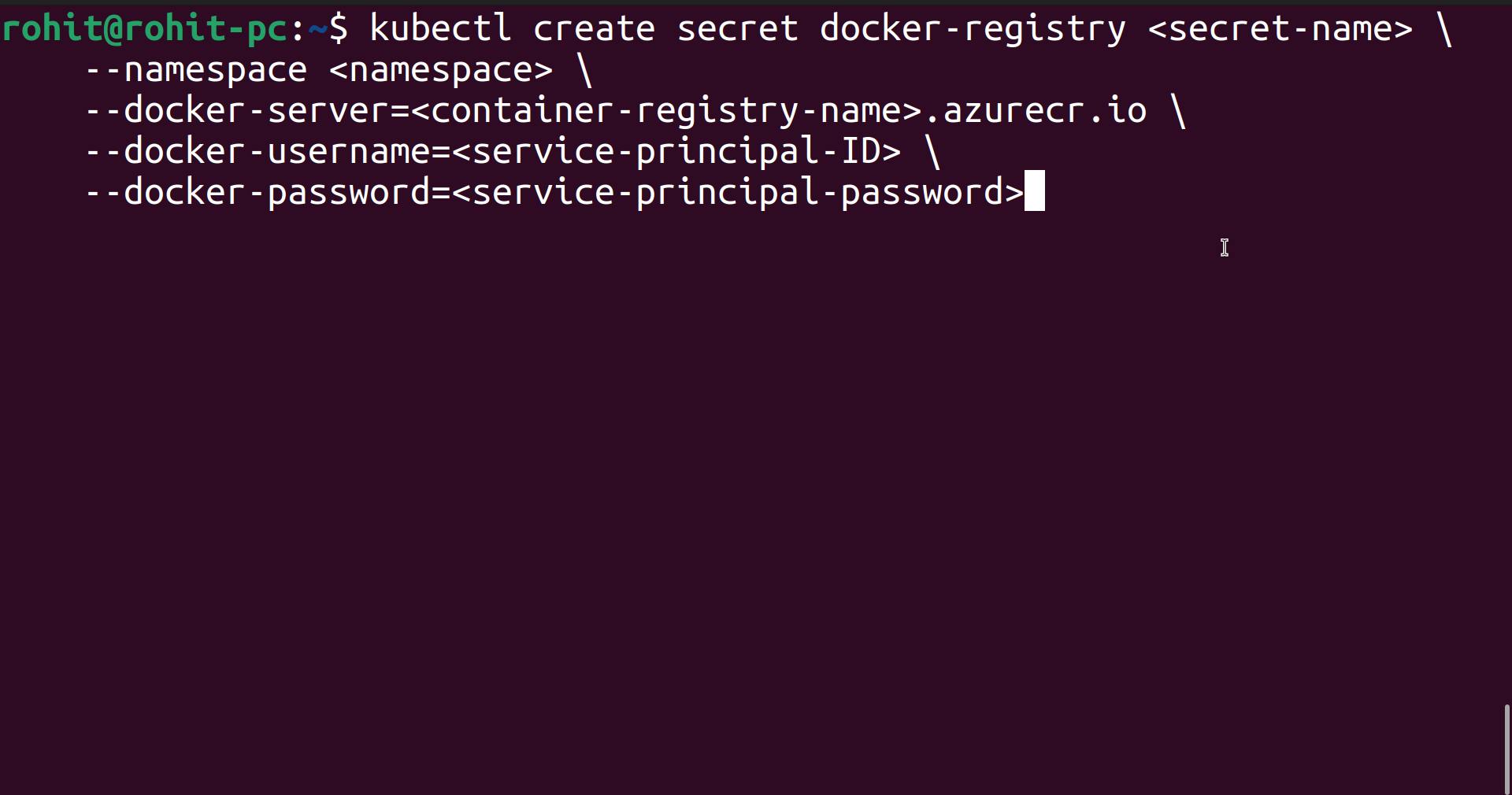
Here change the following things.
1.<secret-name>
2.<namespace>
3.<container-registry-name>
4.<service-principal-ID>
5.<service-principal-password>
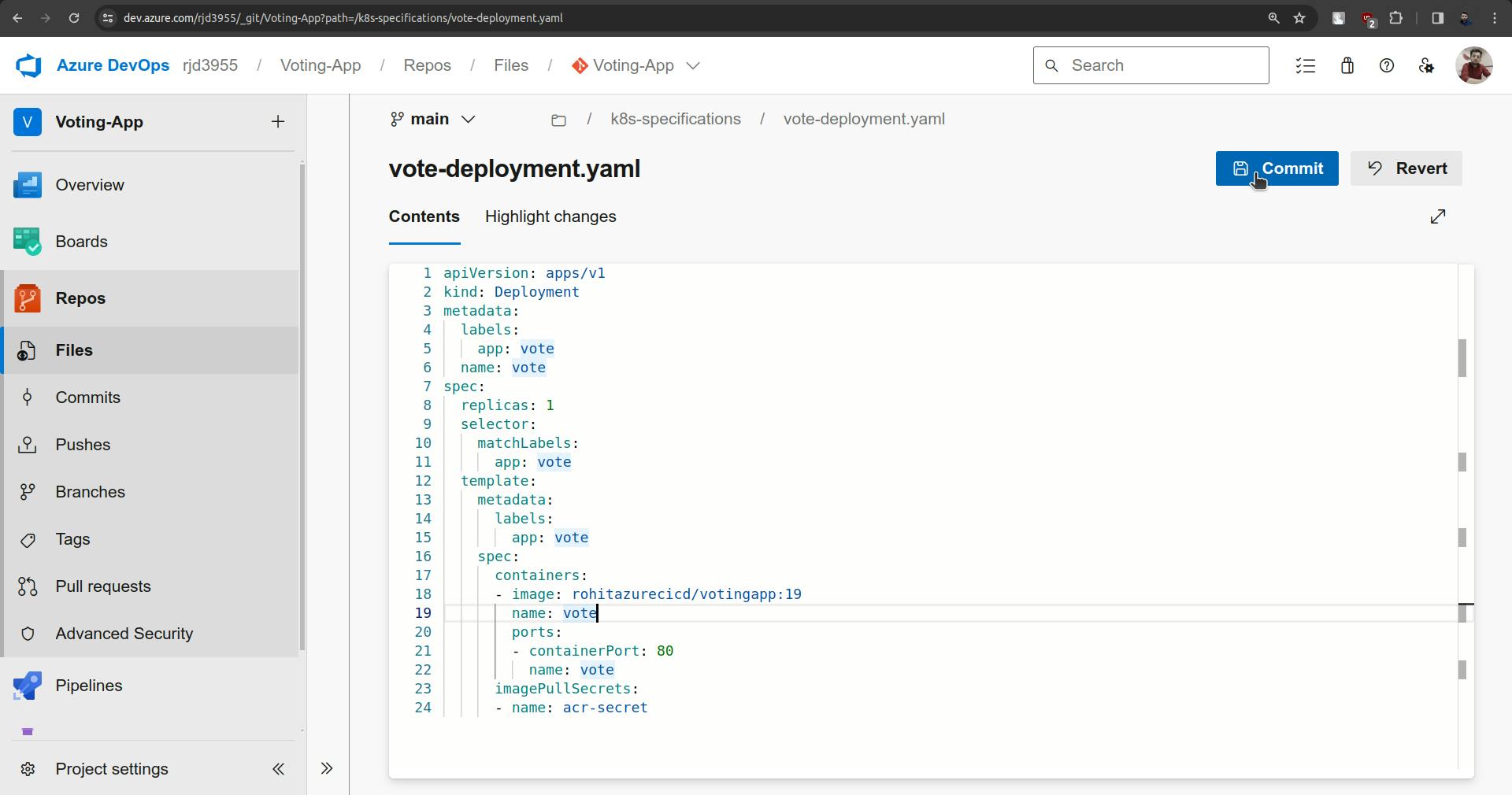
Now got vote-deployment.yaml file and the following thing which highlighted.
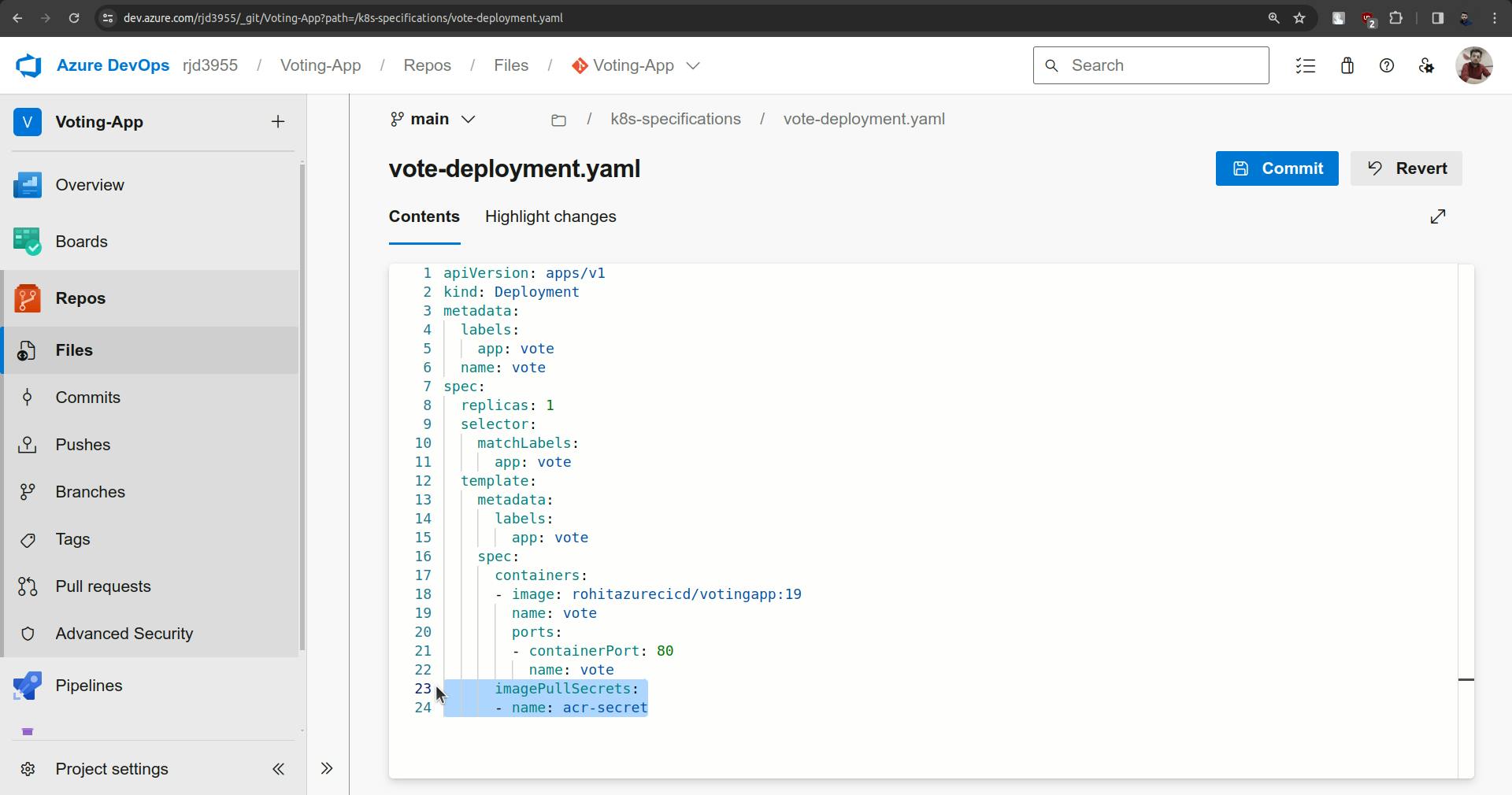
imagePullSecrets:
- name: acr-secret
And commit it.
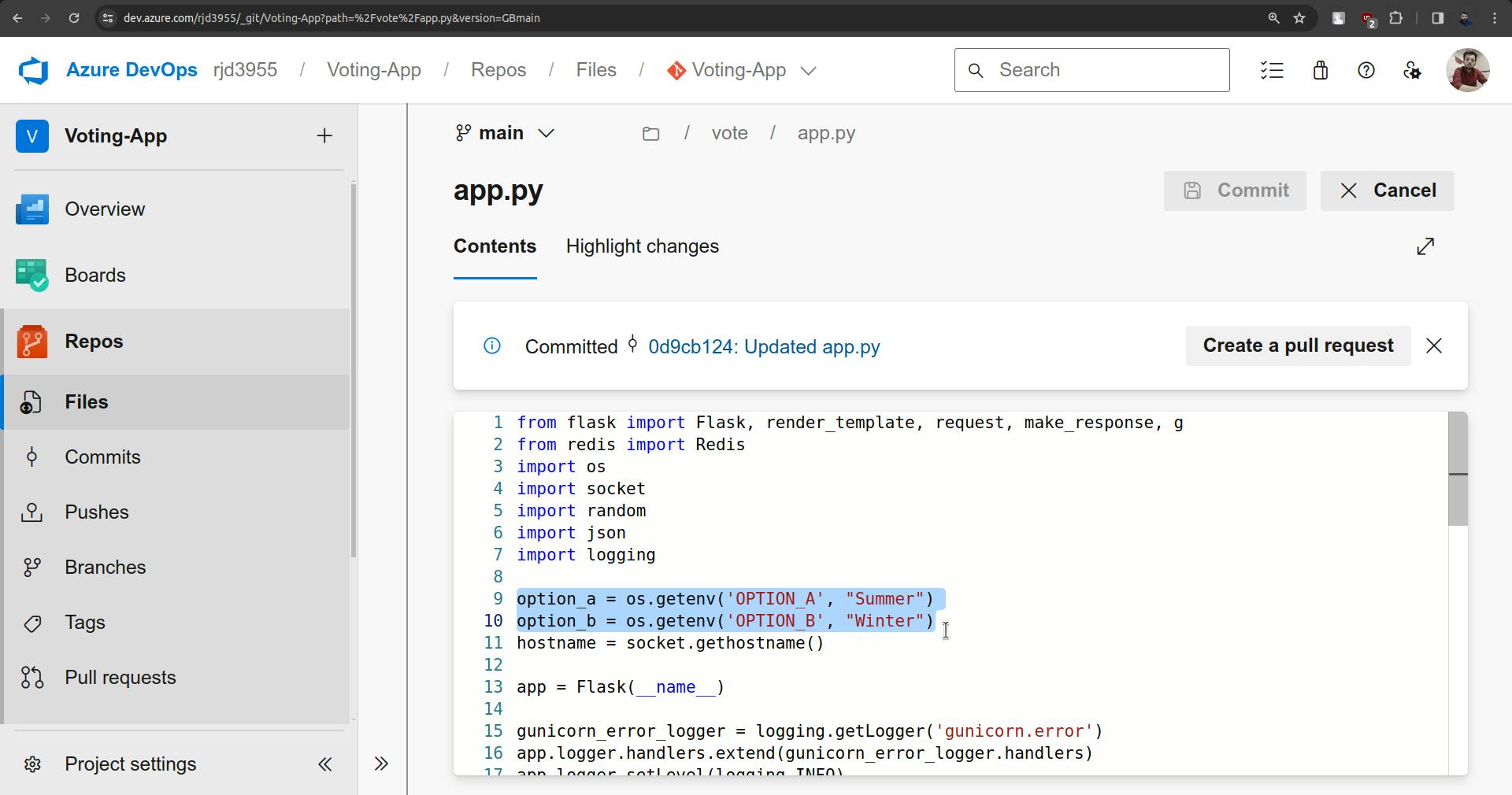
Now to check CICD go to vote folder and open app.py.
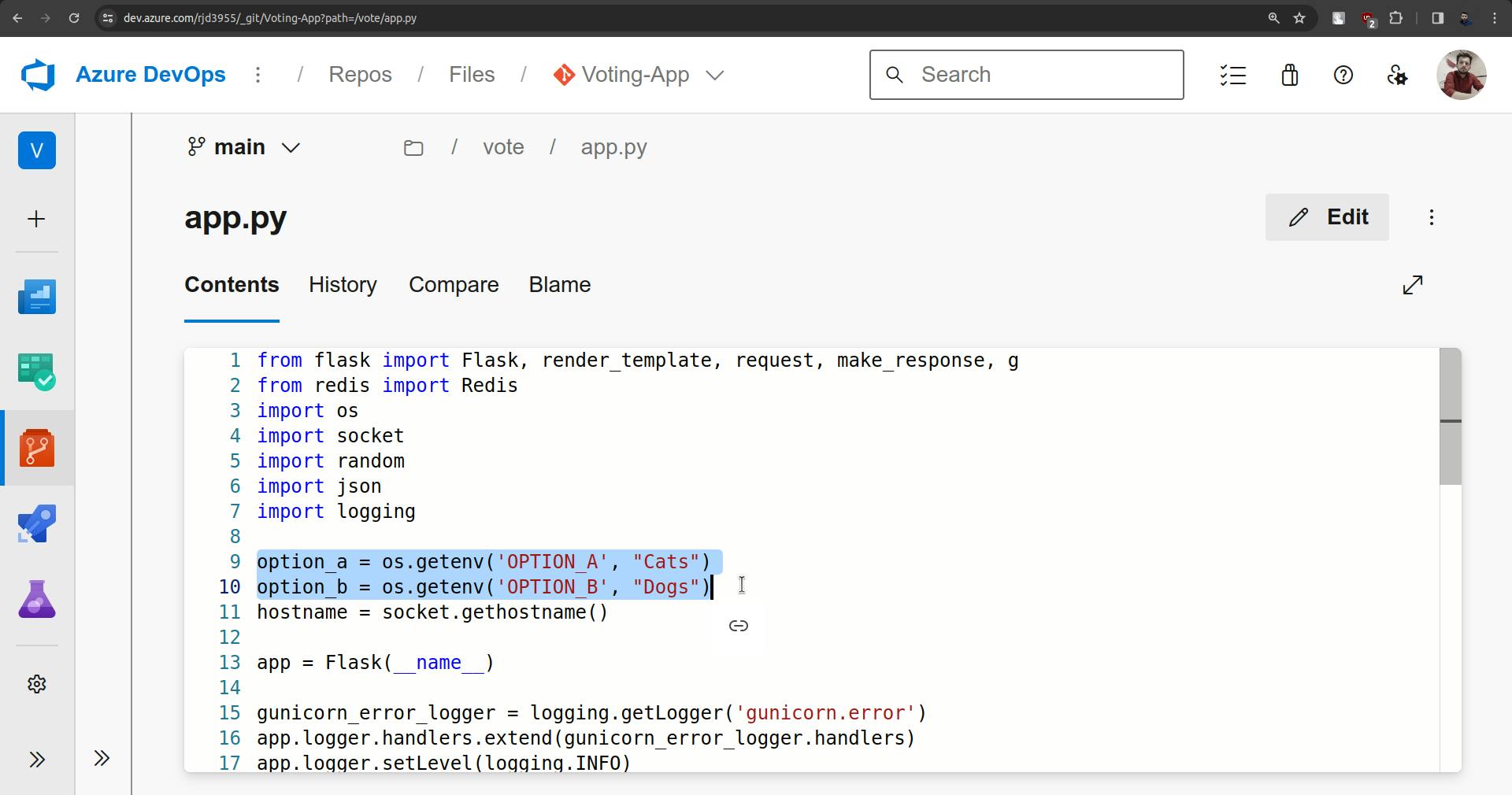
Change both options.
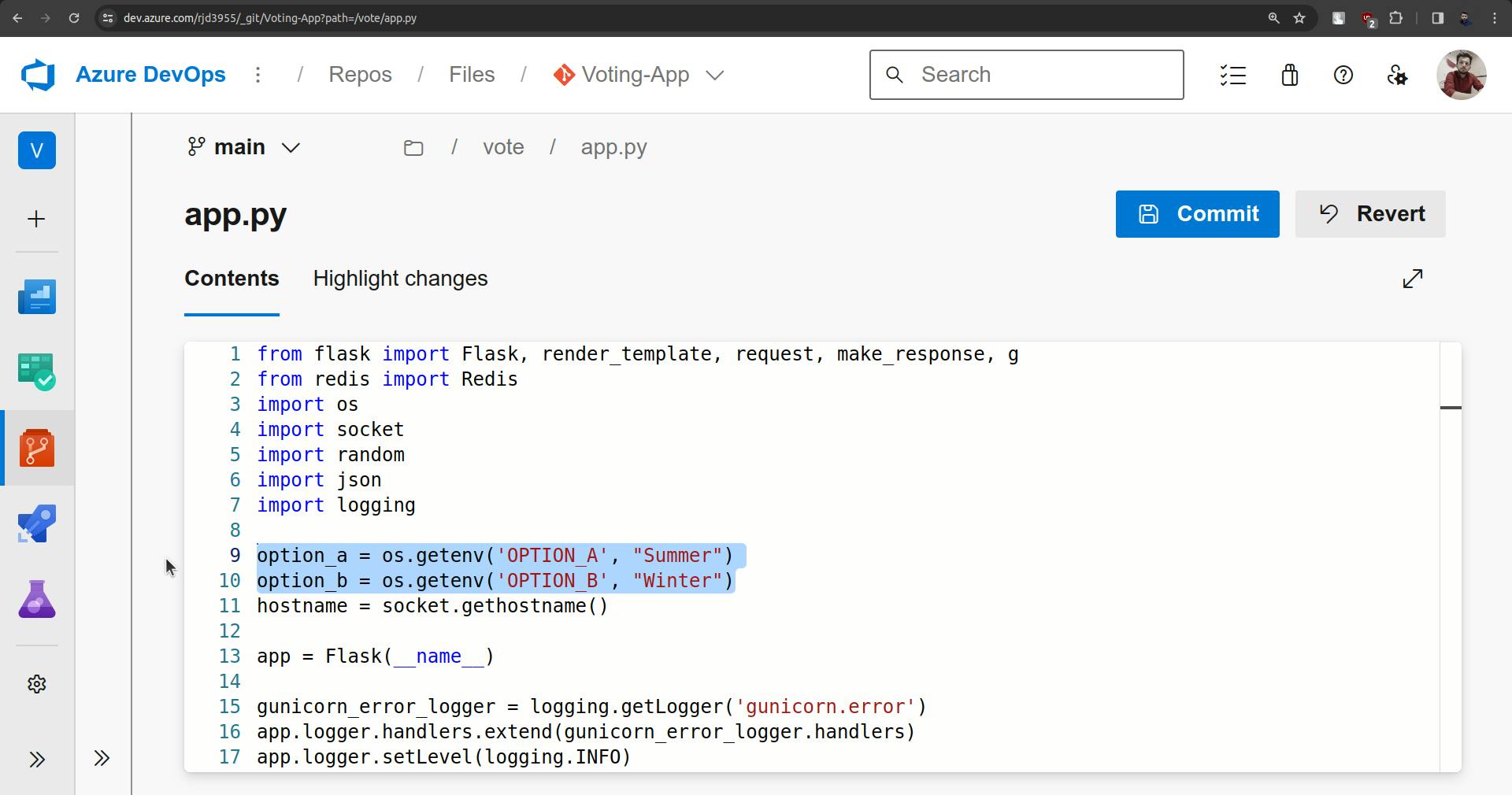
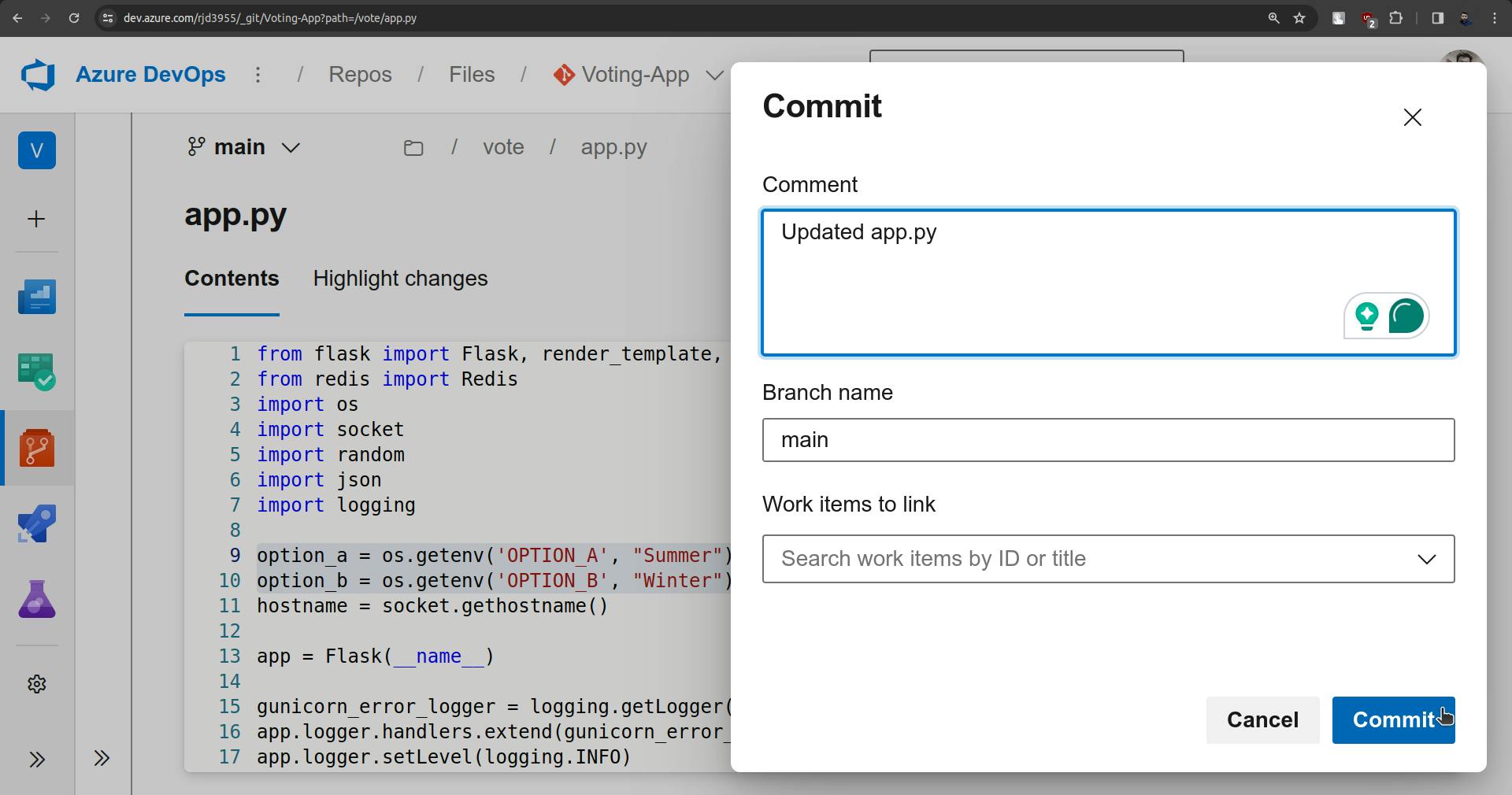
Commit the changes.
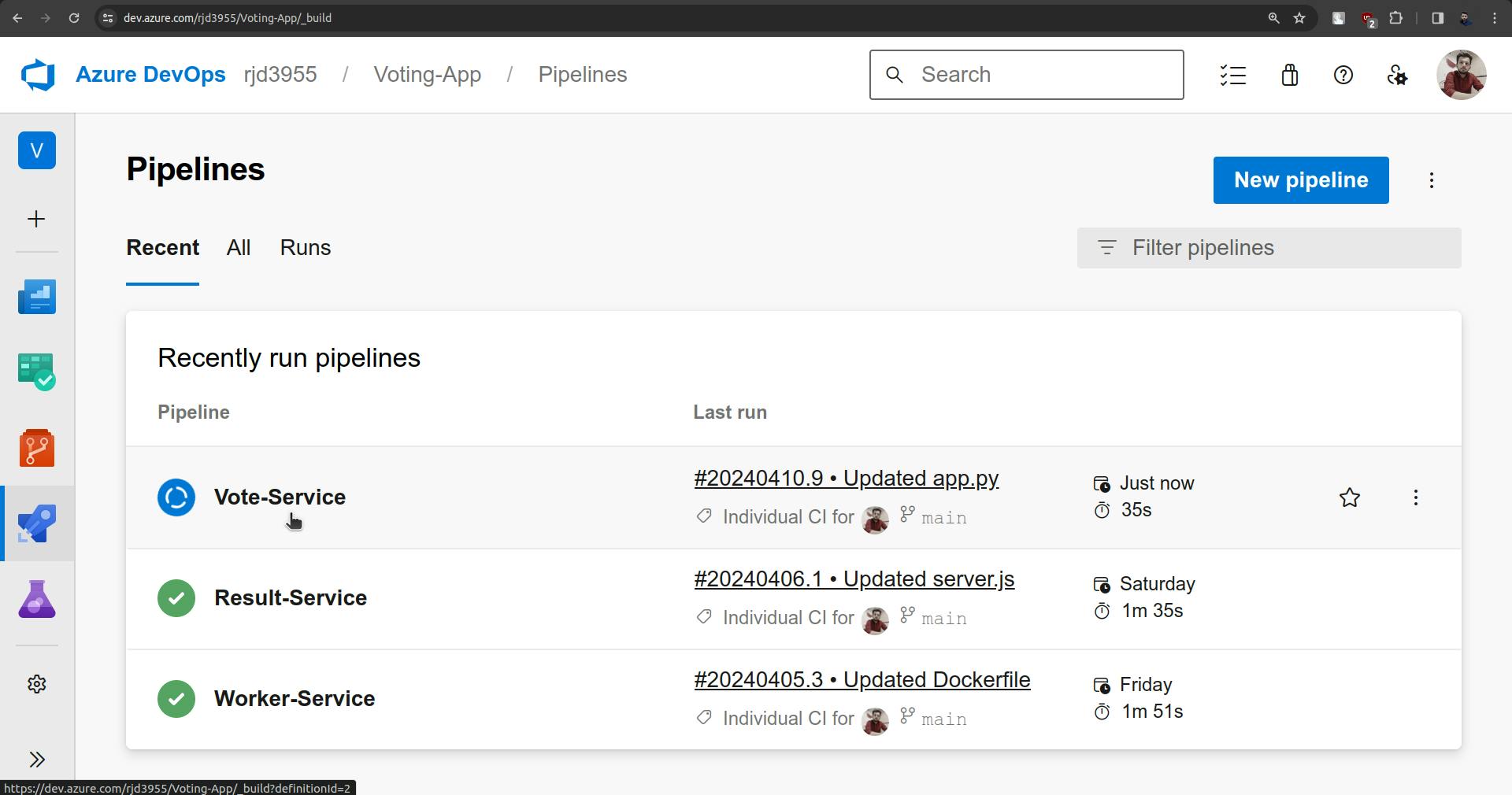
Now the pipeline should be triggered automatically.
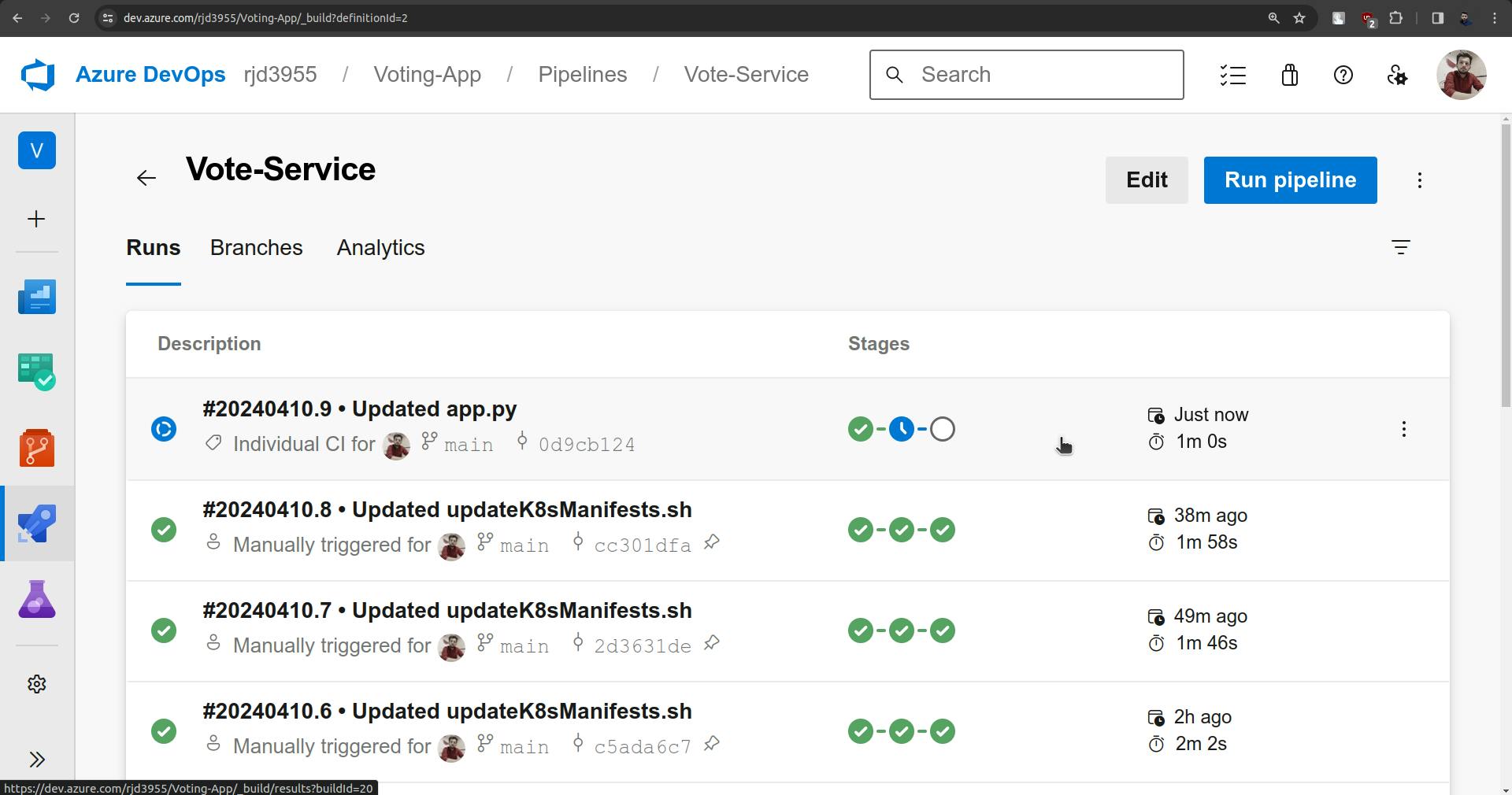
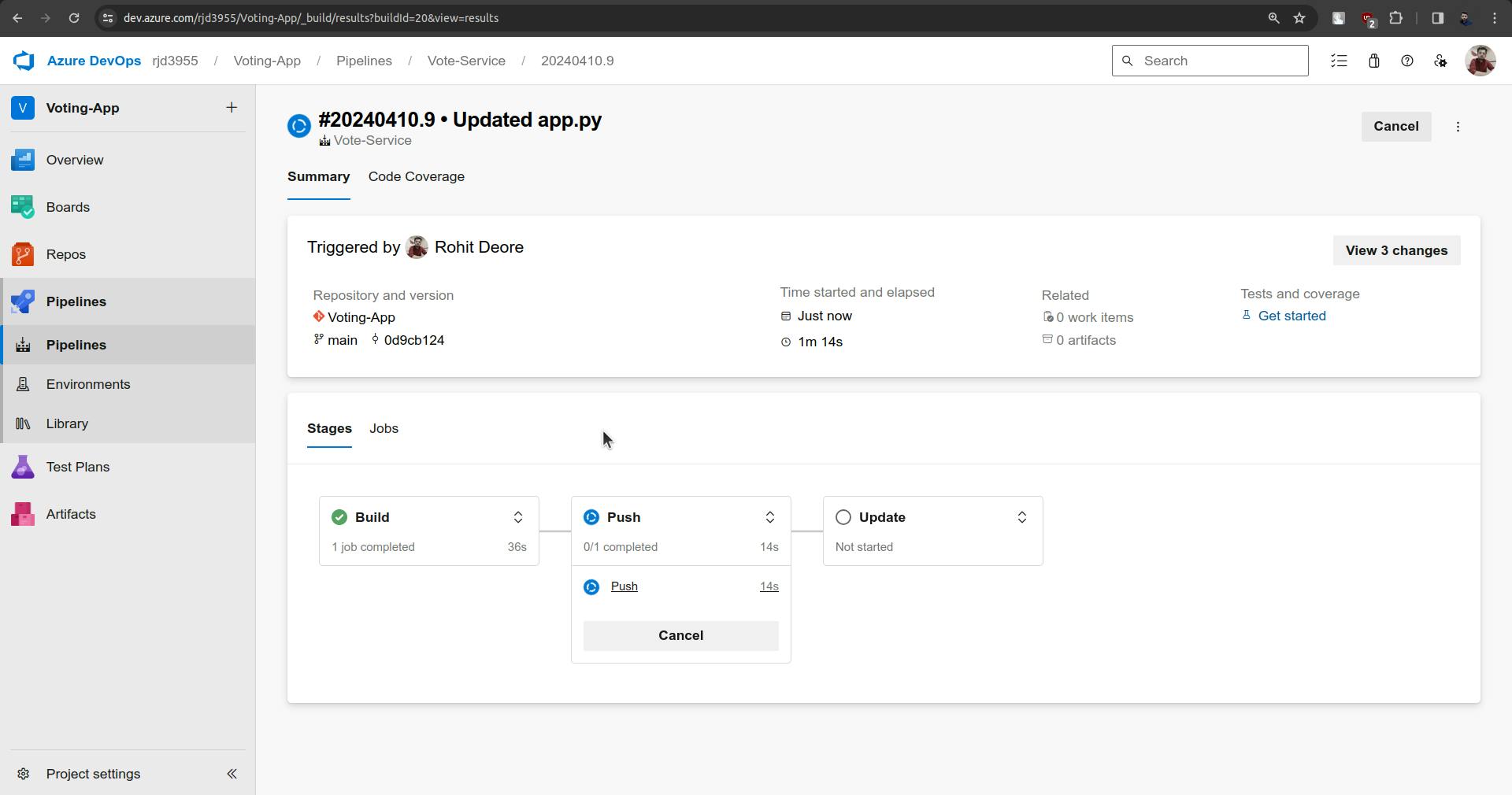
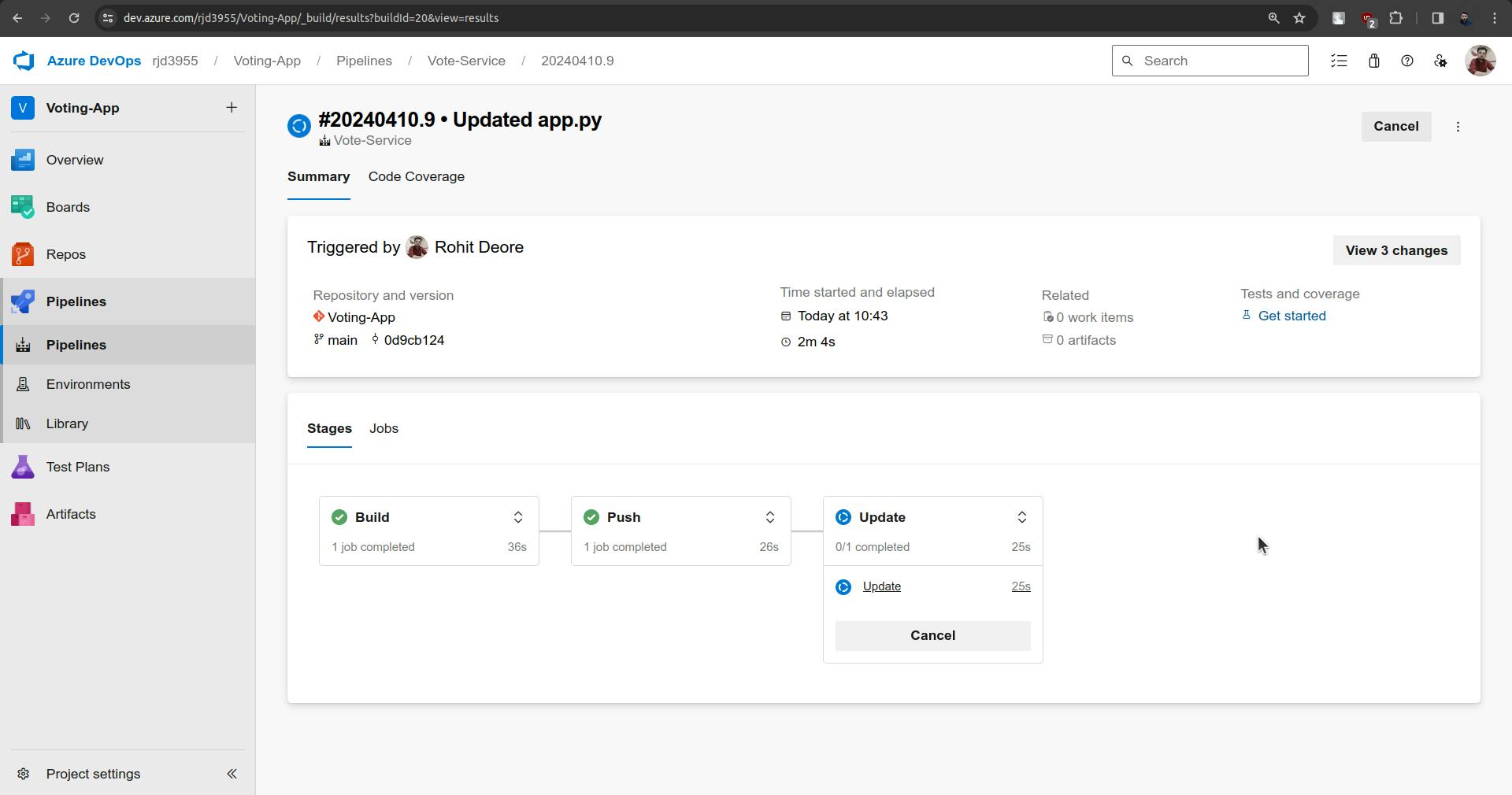
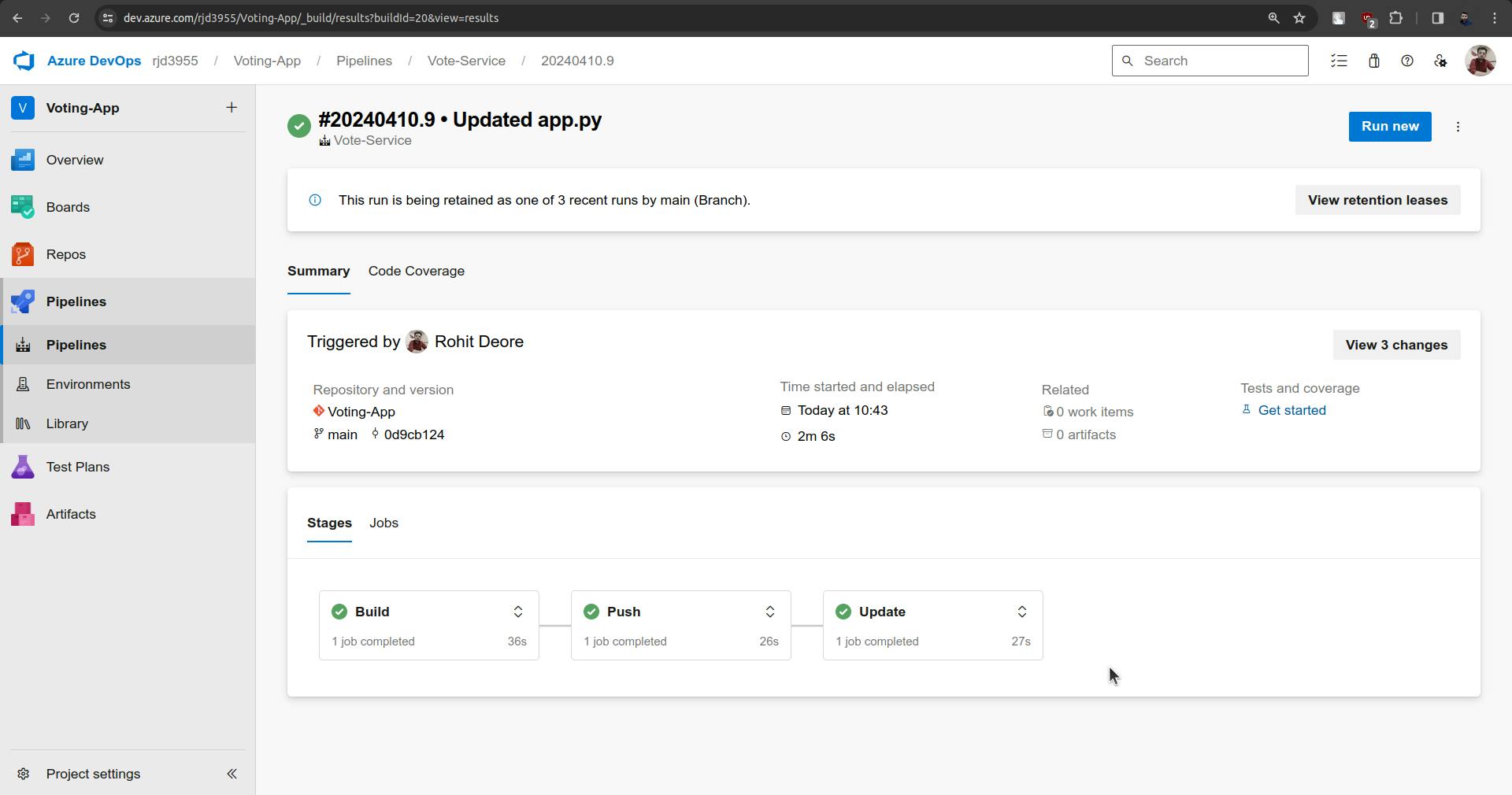
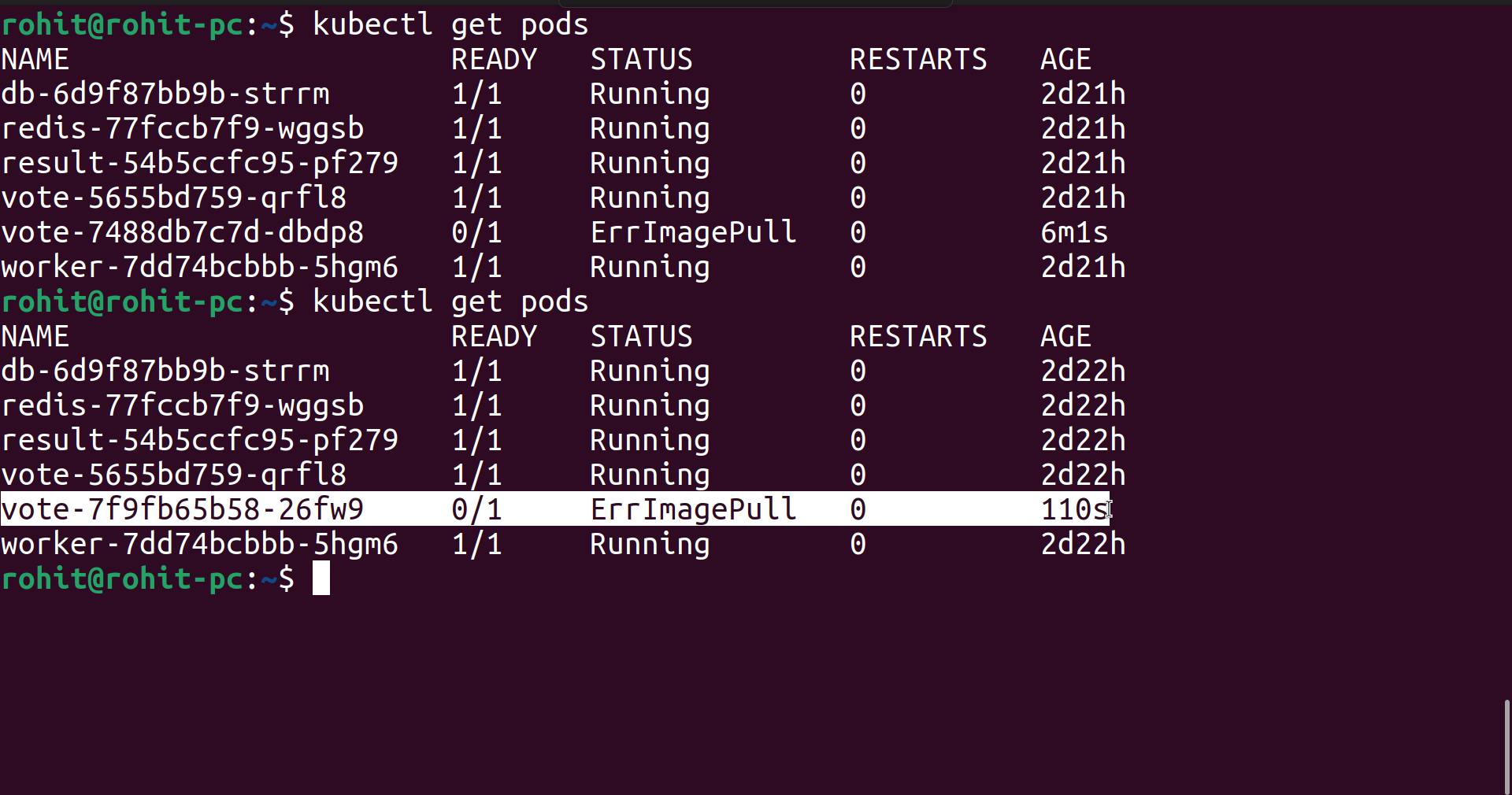
Changes are not synced yet.
It will take little time.
sync is done and there are some issues with the pod.
To solve this, go to the script and follow the screenshots provided below.
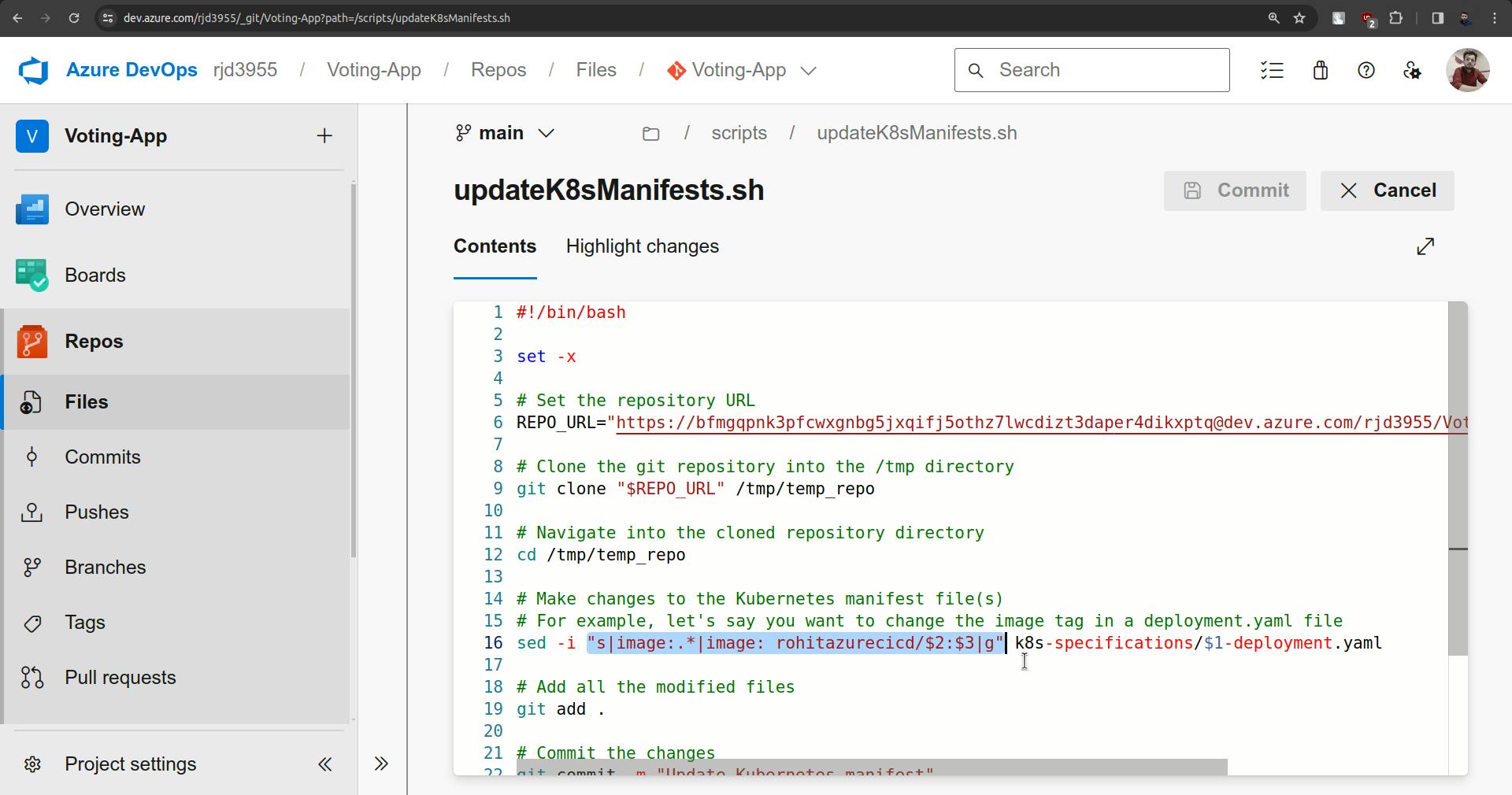
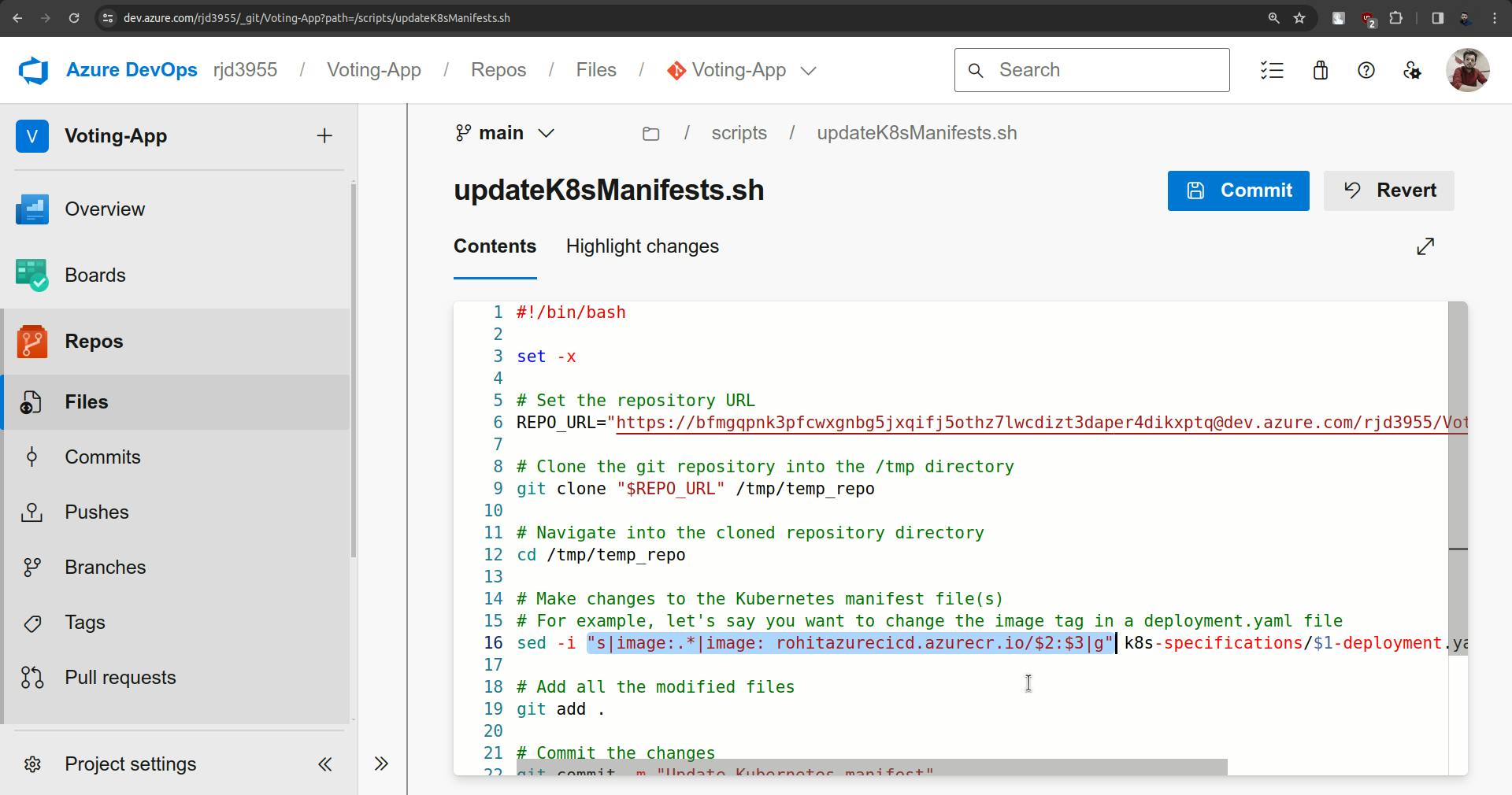
Observe the changes from screenshots, make them and click on commit.
Now try to trigger CICD by making some changes.
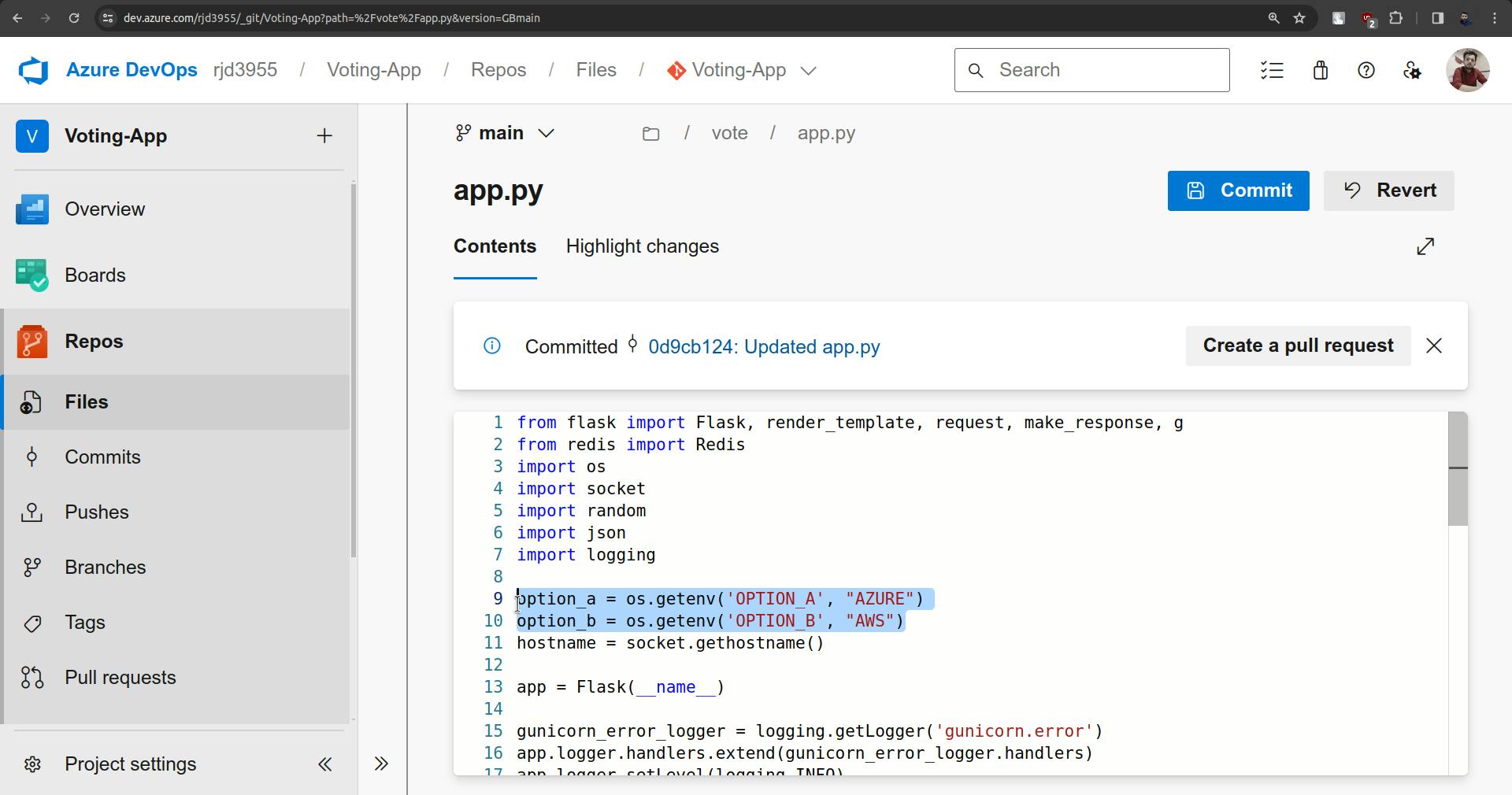
Commit and CICD will triggered.
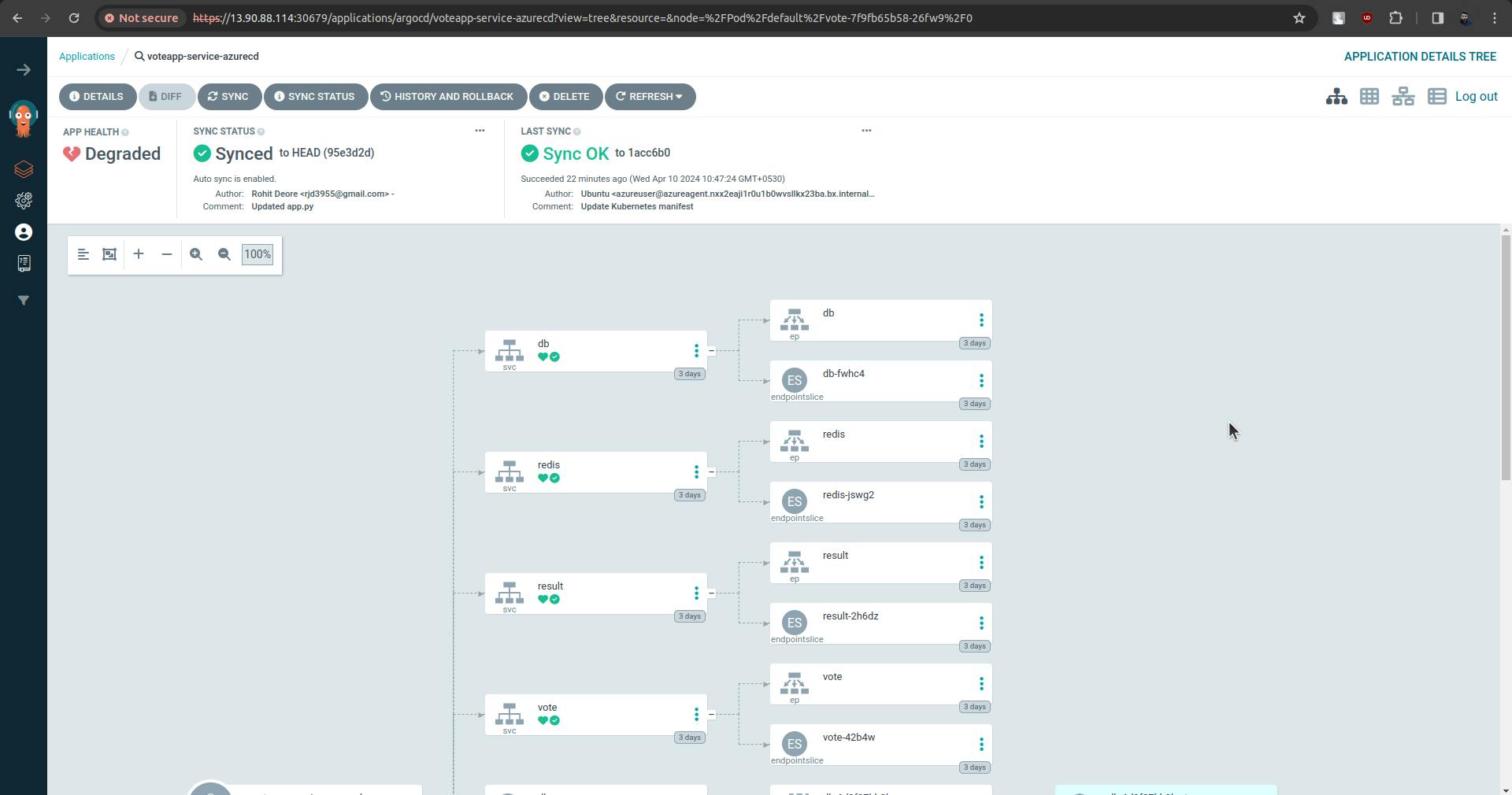
There is an issue with pod.
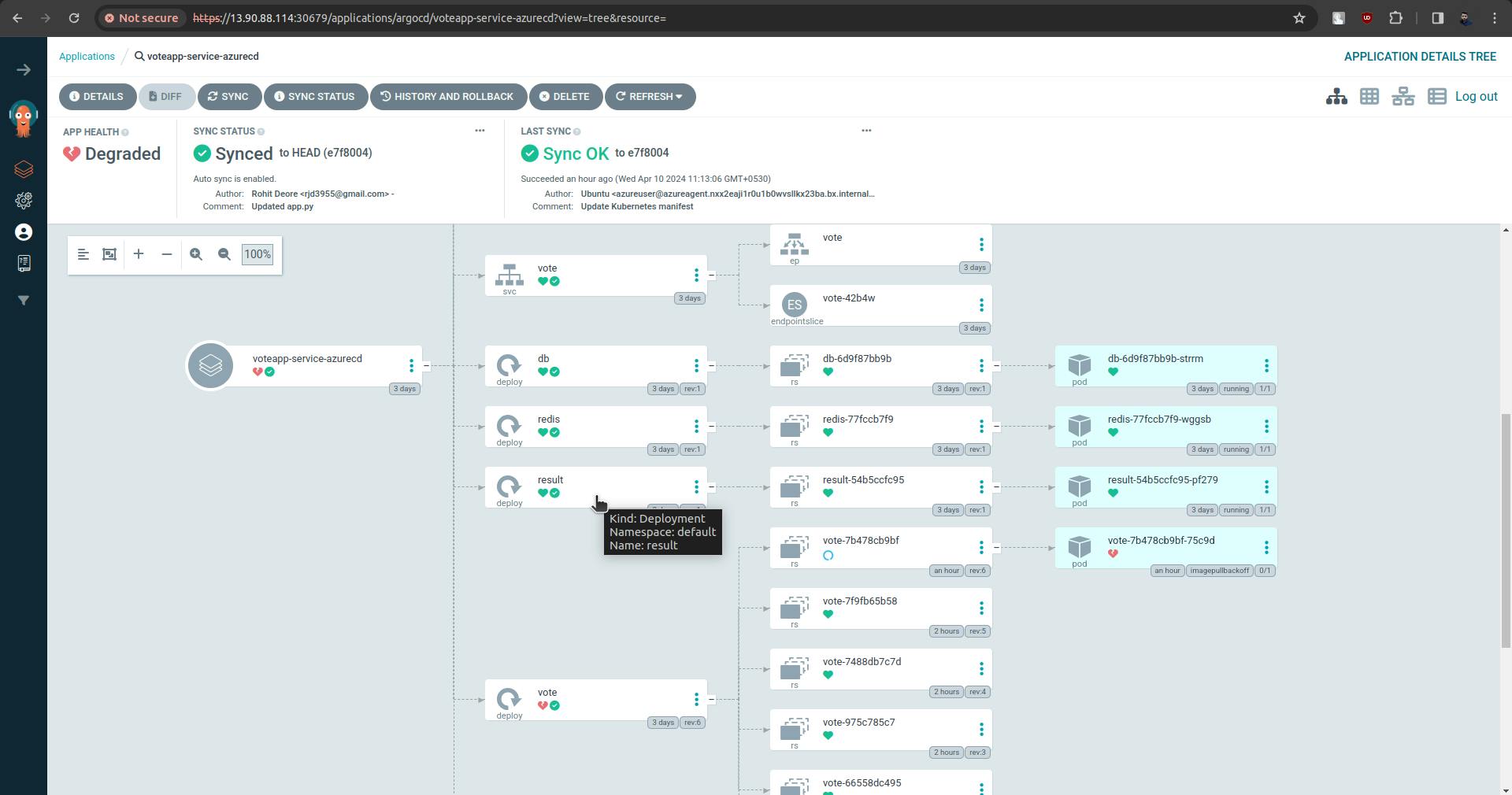
There is an issue between Azure Container Registry and k8s.
Keep in mind that while creating ACR use lowercase alphabets to name it.
*** Now I have changed the ACR name to lowercase alphabets ***
Now let's make some changes in the vote app and verify our CICD.









Congratulations we have completed the CD part
Thank you for staying with me.
Keep exploring...